
How to allow internet-only access for apps in ThreatLocker?
This document outlines the step-by-step process of how to allow internet-only access for apps in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 06 – Network Control & Ringfencing.
Introduction
In some cases, you may want to allow an application to access the internet while restricting its access to internal resources, shared drives, or other local systems.
With ThreatLocker Application Control and Network Ringfencing, you can configure an application to have internet-only access by explicitly blocking internal IP ranges while permitting external communication.This guide explains how to create a policy that allows Google Chrome to access only the internet and nothing else.
Implementation
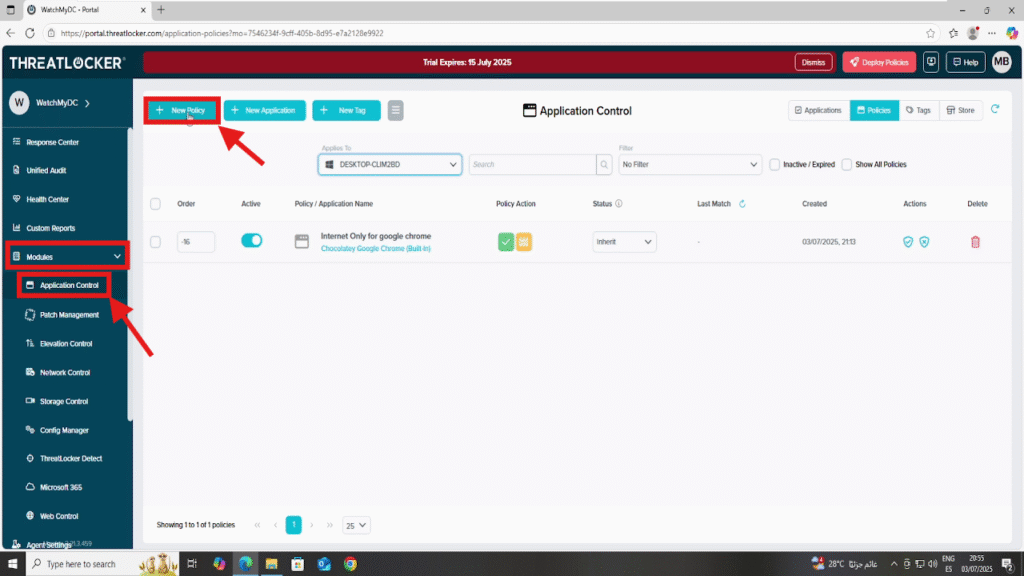
Step 1: Access the Application Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Application Control
- Click Create Policy
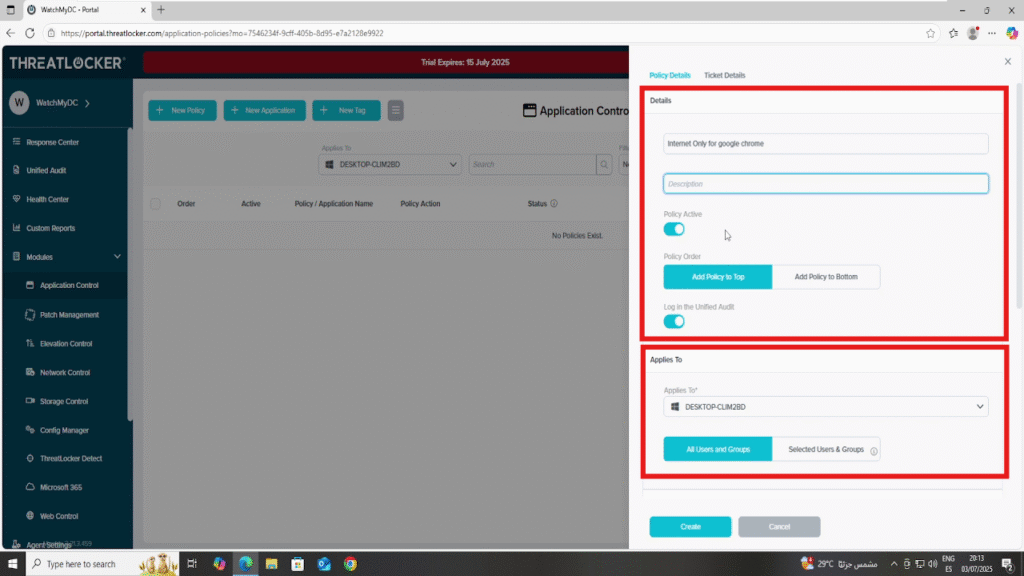
Step 2: Create the Application Control Policy
- Fill the policy form
- In the Details section
- Name: Internet Only for Google Chrome
- Description: Allow internet access only for Google Chrome
- In the Applied To section
- Select the target computer or computer group where the policy should apply
- In the Condition section
- Select the application:Google Chrome
- Select All Interfaces
- Select No Policy Expiration to keep the rule active indefinitely.
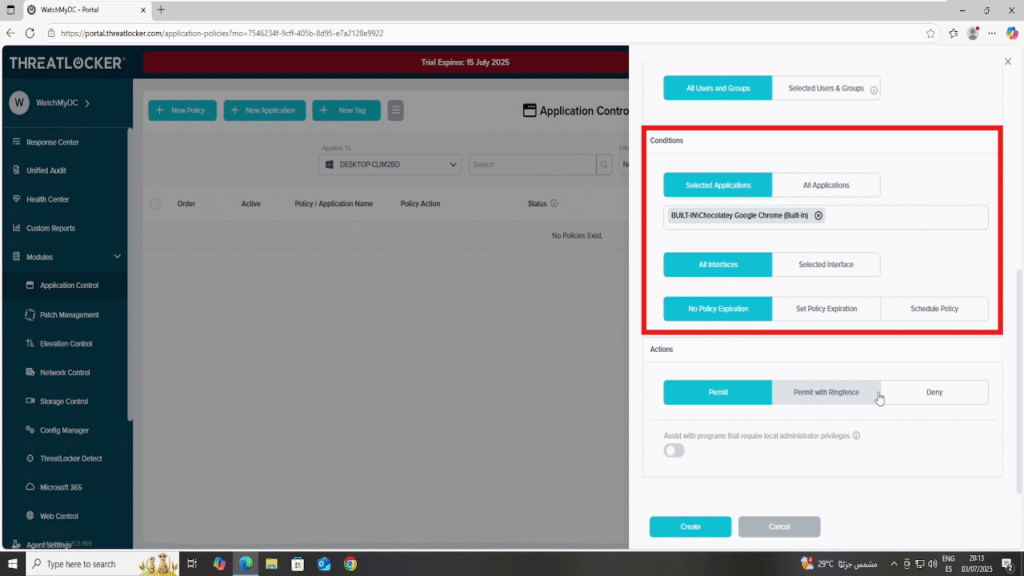
In the Action section:
- Select Permit with Ringfencing
- Then enable all the following options:
- Restrict this application from interacting with other applications
- Restrict this application from accessing files
- Restrict this application from changing the registry
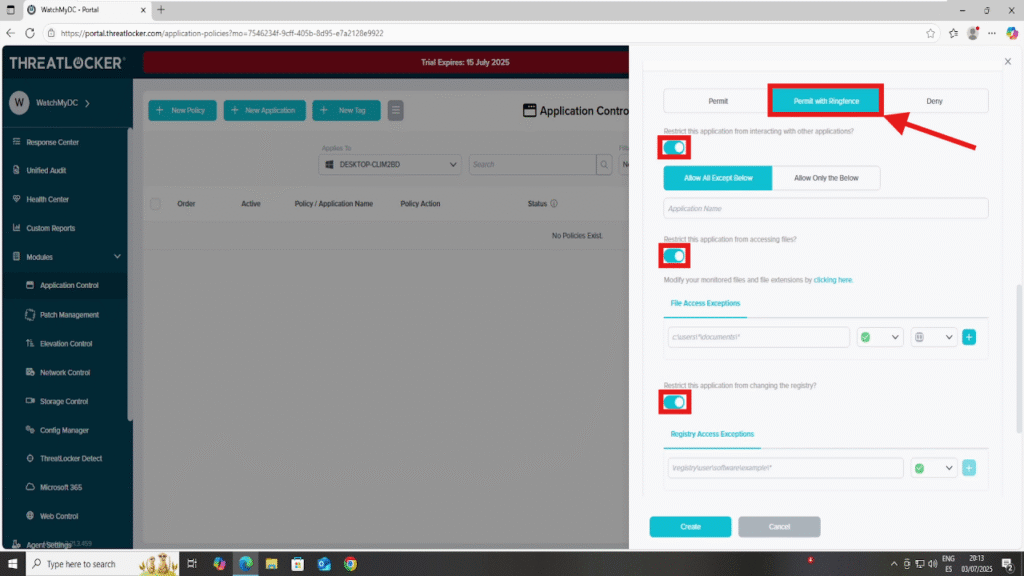
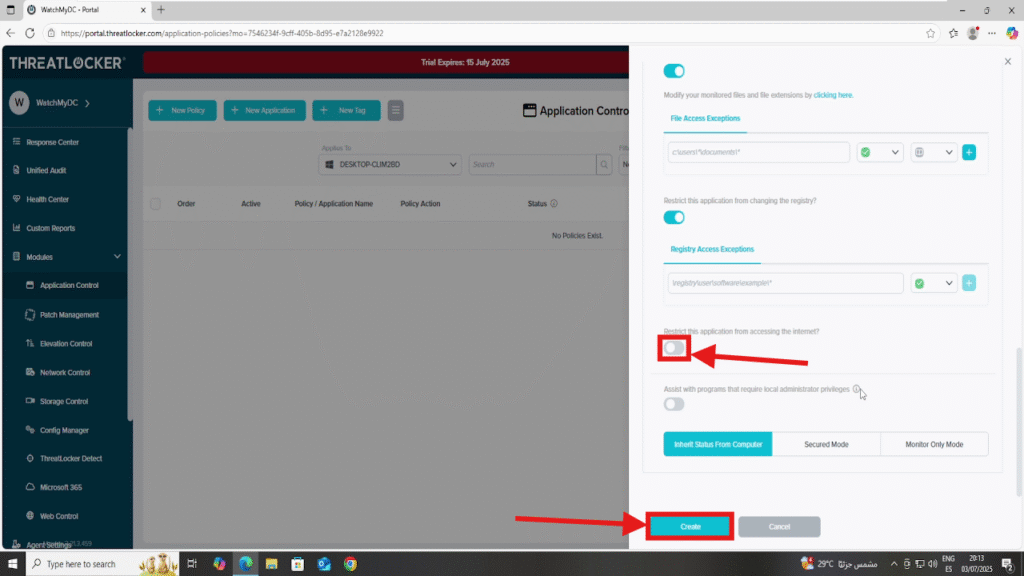
- Make sure to disable this setting:
- Restrict this application from accessing the internet
2. After all fields are completed, click Create to save the policy
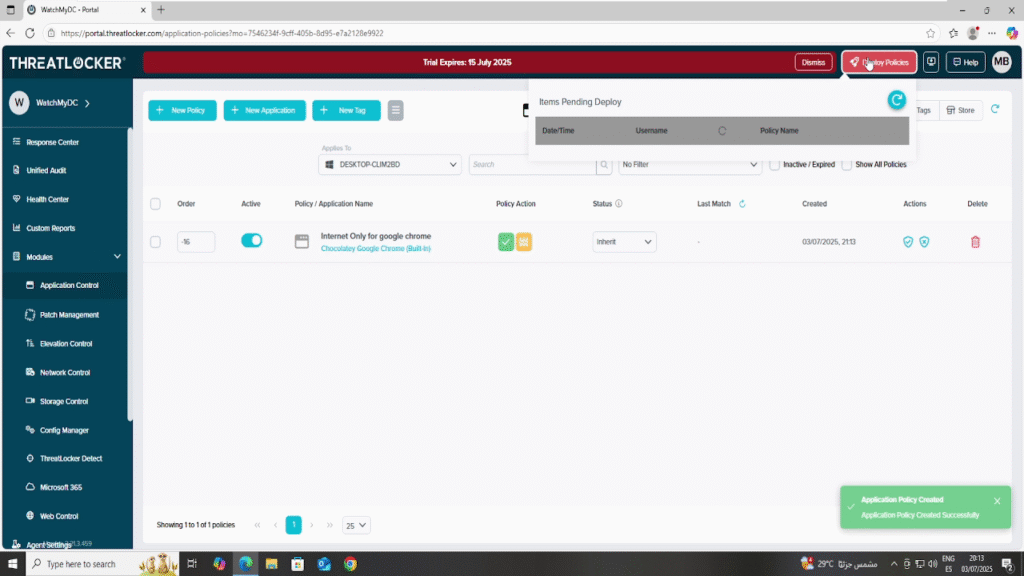
Step 3: Deploy the policy to allow internet-only access for apps
Deploy the policy to enforce it on the selected devices
Conclusion
This setup ensures that applications like Chrome can access external resources on the internet, while being blocked from interacting with internal systems and local files.
It’s an effective method to apply Zero Trust principles and reduce the risk of lateral movement or data leaks from potentially exposed applications.
ThreatLocker allows you to enforce strict, application-specific network boundaries with just a few clicks.
