
How to allow software by path?
This document outlines the step-by-step process of how to create a allow a software by path in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
ThreatLocker lets administrators allow applications based on various conditions, including file path.
This is especially useful for internal tools or applications not signed by a publisher, or when the file hash changes frequently.In this guide, we will allow an application (e.g., Zoom) by its full path, using the audit-based approval method.
Implementation
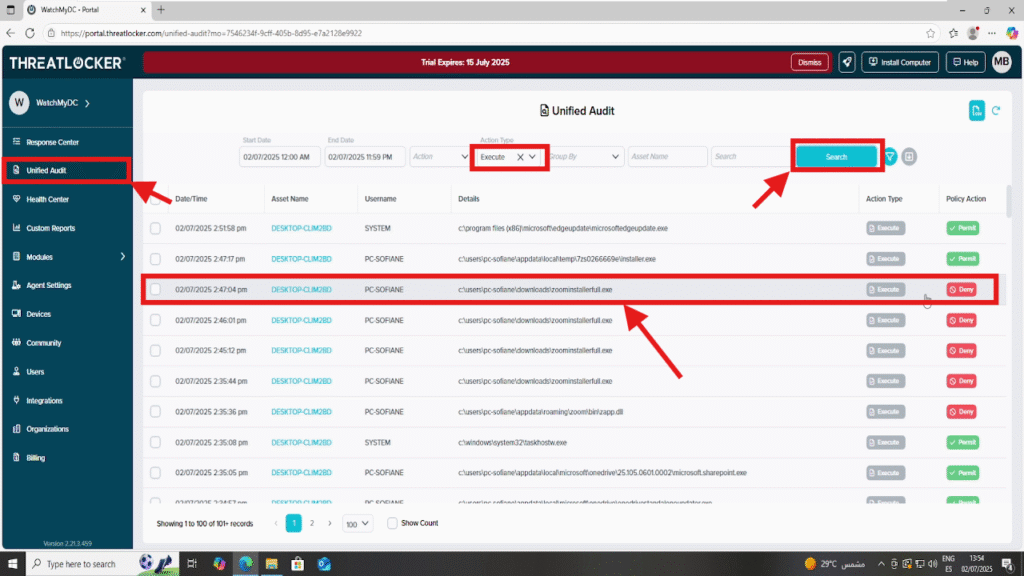
Step 1: Locate the Executable in Unified Audit
- Log in to the ThreatLocker Portal
- Go to Unified Audit
- In the filters, set Action Type to Execute, then click Search
- Locate the application you want to allow (e.g., Zoom.exe) and click on its entry
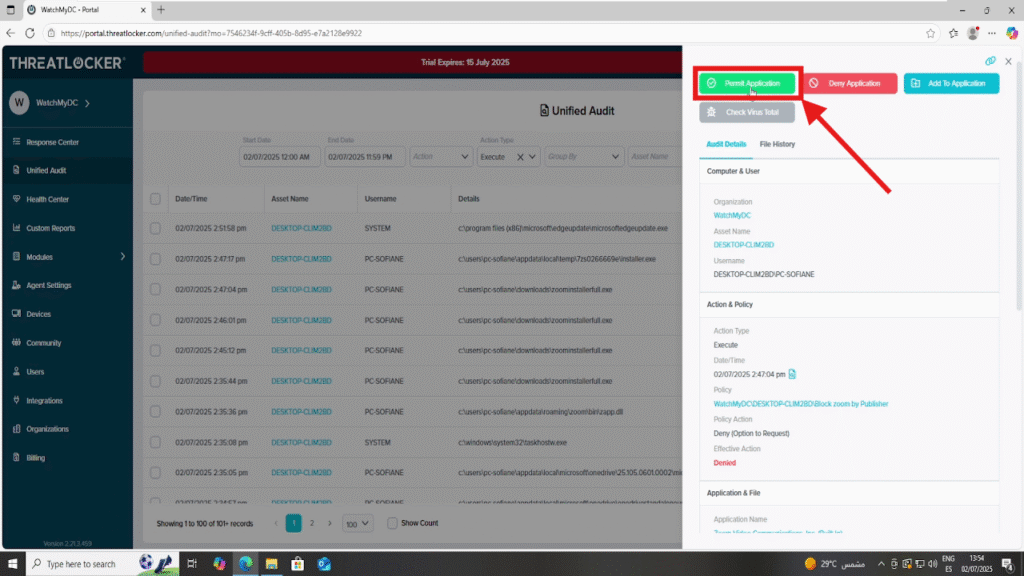
Step 2: Open the Application Approval Window
- After clicking the entry, a details window will open
- Click the Permit Application button at the bottom
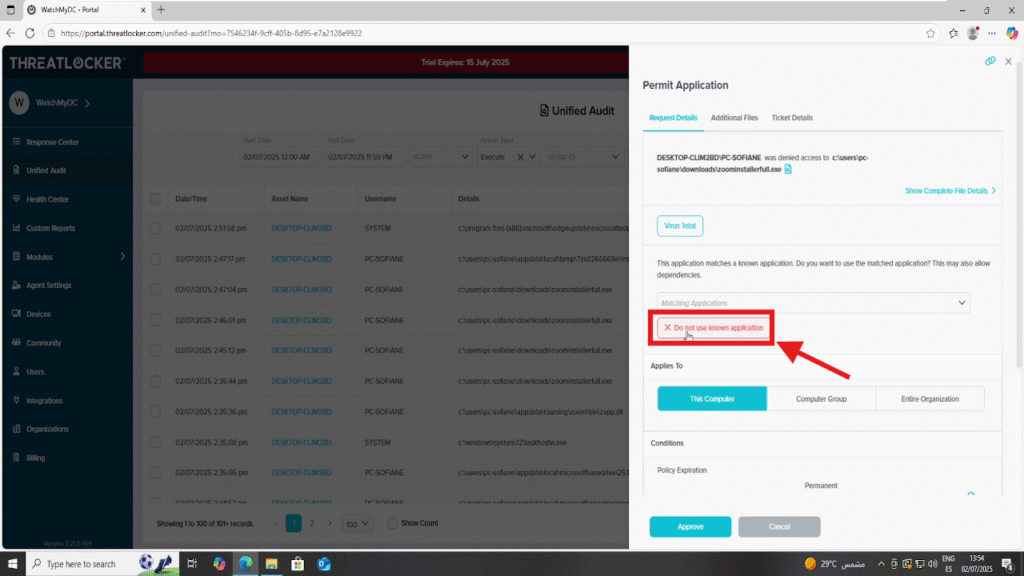
Step 3: Choose Custom Approval Method
- In the “Permit Application” window, look for the Application Choice section
Click “Do not use known application” to reveal other conditions
This allows you to select alternative methods like Path, Hash, or Publisher
Step 4: Set the Condition to Full Path
From the list of available conditions, select Full Path.
In the path field, enter the exact full path of the executable you wish to allow.
In this example: C:\Users\pc-sofiane\Downloads\ZoomInstaller.exeMake sure the path is exact and case-consistent. This will ensure the policy applies only to that specific file at that specific location.
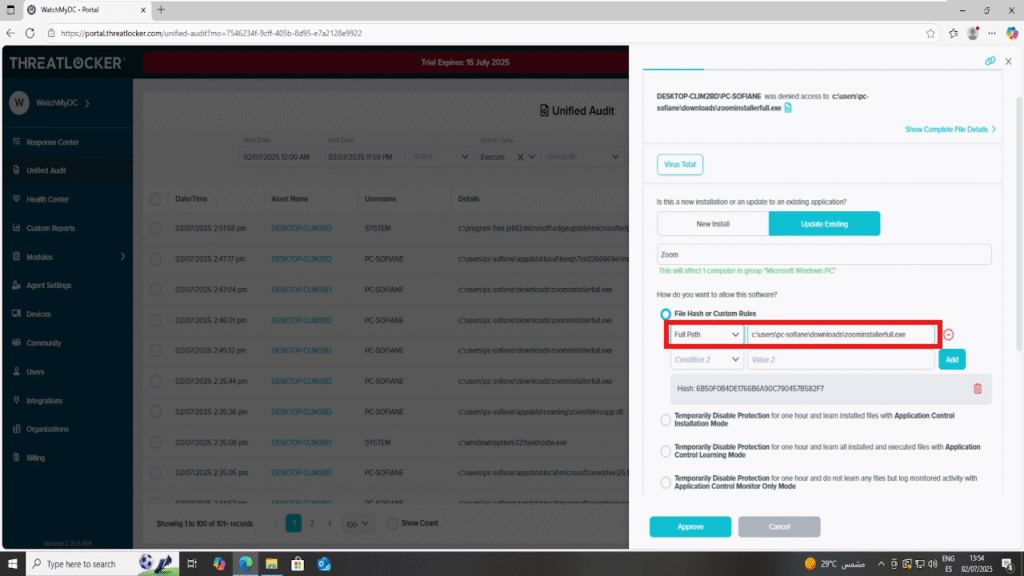
In the Apply To section, select the appropriate computer or computer group where the policy should be enforced for example, This Computer, if you only want to allow it on the current device.
Once everything is reviewed and correct, click the Approve button to finalize and deploy the policy.
Conclusion
Approving software by full path in ThreatLocker provides a flexible and secure way to allow specific applications without compromising your Zero Trust model.
This method is ideal for internal tools, unsigned installers, or one-off utilities located in trusted directories. By specifying the exact path, you minimize the risk of unauthorized variants being executed elsewhere.
As always, review audit logs carefully before approving, and ensure the file path is accurate to avoid misconfigurations.
