
How to apply policies by device group?
This document outlines the step-by-step process of how to apply policies by device group in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
In ThreatLocker, policies can be applied not just globally, but also to specific groups of devices.
This allows administrators to tailor security rules based on department, function, or role, for example, applying stricter controls to servers and more flexible ones to user laptops.
This guide explains how to apply application policies to one or more Device Groups.
Implementation
Step 1: Access the Application Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Application Control > Policies.
- Click “Create Policy,” or locate an existing policy that you want to edit.
- In this example, we’ll modify the policy for PowerShell.
- Click on the policy to open the configuration panel.
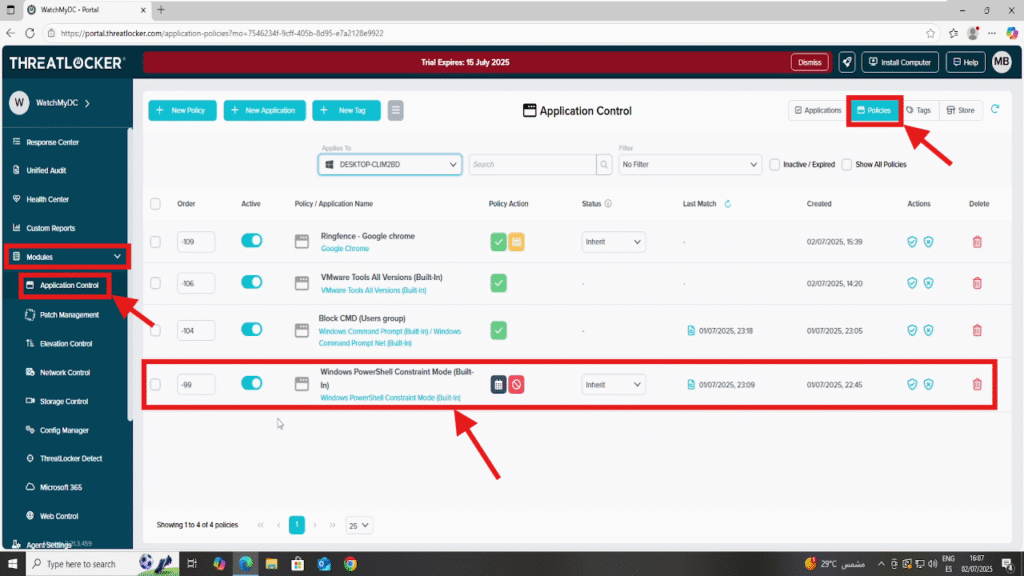
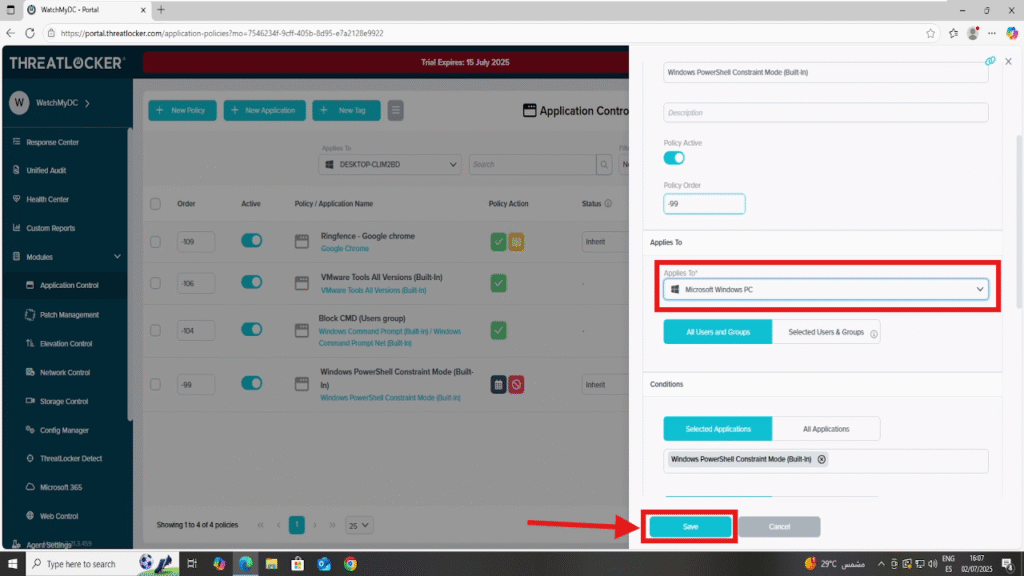
Step 2: Configure the “Apply To” Section
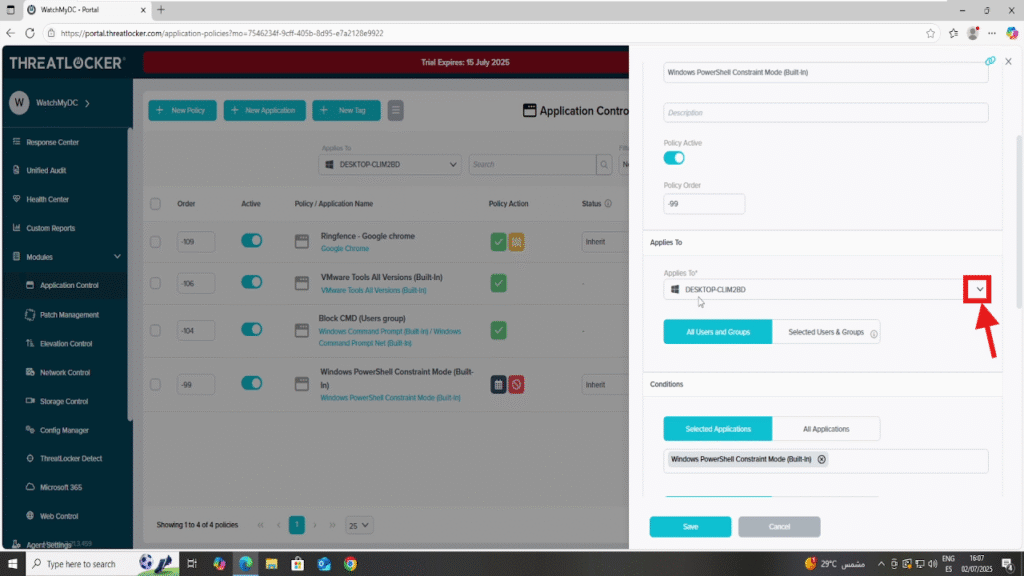
- 1. In the policy editor, click on the “Applied To” field to expand it and display all available devices and device groups.
- 2. A list of available computer groups will now appear in the selection pane.
- 3. Select the desired Computer Group (e.g., Microsoft Windows) to which you want to apply the policy.
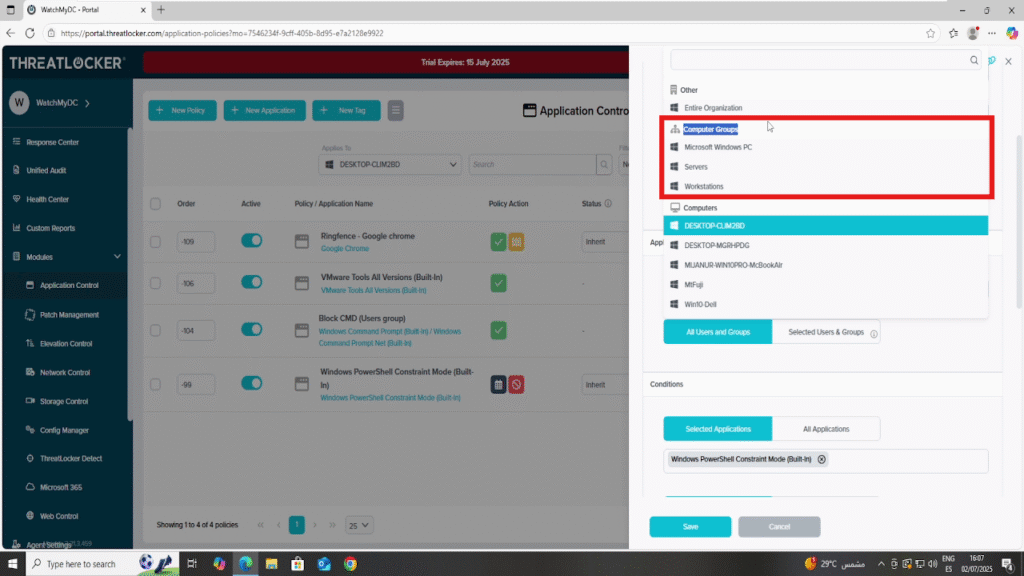
- 4. After selecting the appropriate group, click “Save” to apply your changes.
Step 2: Deploy to apply policies by device group
After making your changes, click the “Deploy” button to apply the updated policy to all relevant endpoints.
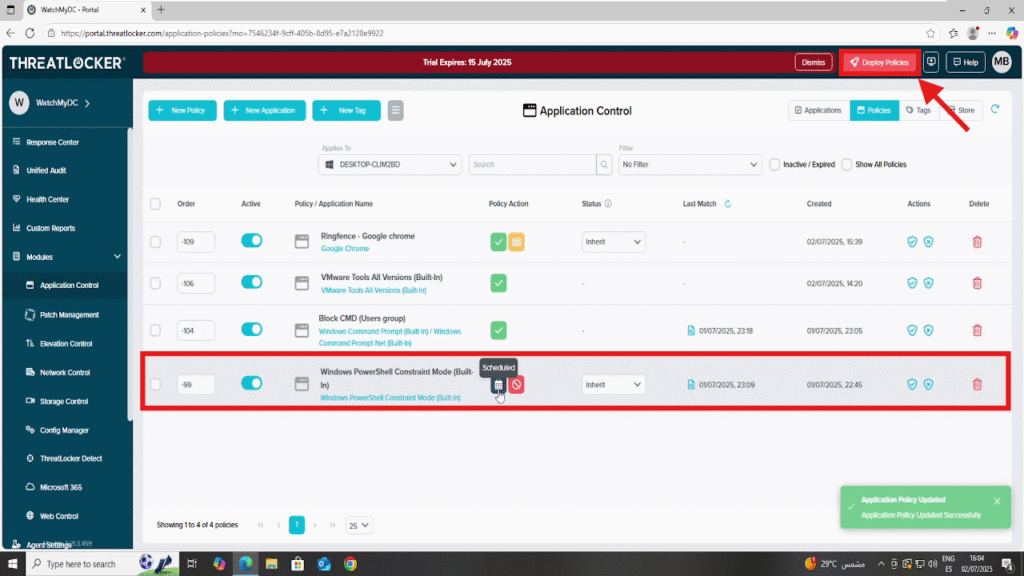
Once deployed, the policy will appear in the list of active policies.
Conclusion
Applying application control policies by device group in ThreatLocker enables precise and scalable security management.
This method ensures that only the intended machines receive the right permissions or restrictions. It enhances both administrative control and operational clarity. By grouping devices logically (e.g., by OS, role, or department) and assigning policies accordingly, you maintain a clean and efficient Zero Trust architecture.
Remember to review and adjust groups regularly as your environment evolves.
