
How to apply temporary application policies?
This document outlines the step-by-step process of how to apply temporary application policy in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
In many operational scenarios, you may need to allow or deny access to an application for a limited period. For example: during software deployment, incident response, or short-term testing.
ThreatLocker provides a built-in Policy Expiration feature, allowing administrators to create temporary application policies that automatically expire at a specified date and time.
This ensures access is granted only when necessary and removed without requiring manual intervention.
Implementation
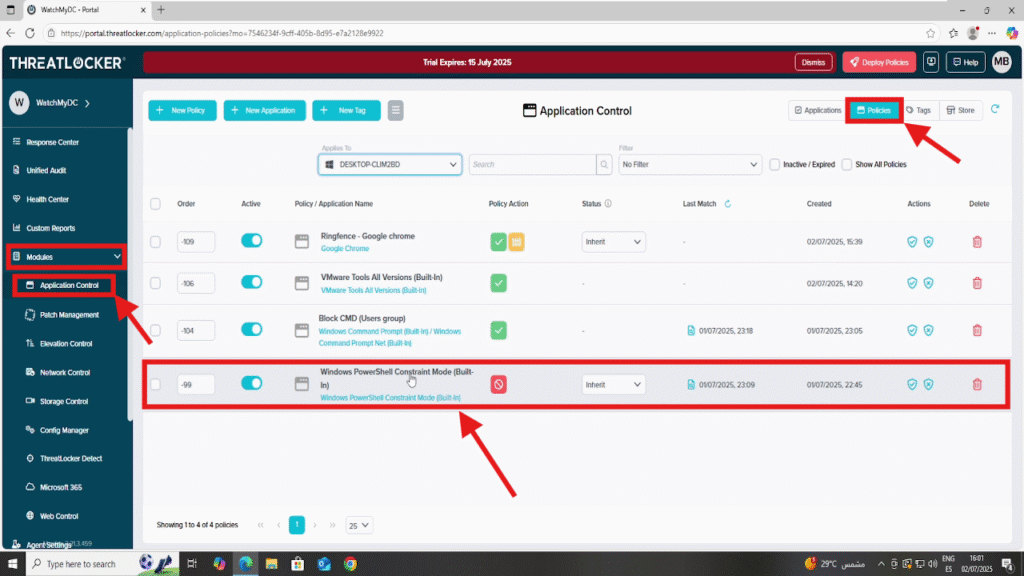
Step 1: Access the Application Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Application Control > Policies.
- Locate or create the policy where you want to apply the temporary rule.
- In this example, we’ll modify the policy for PowerShell.
- Click on the policy to open the configuration panel.
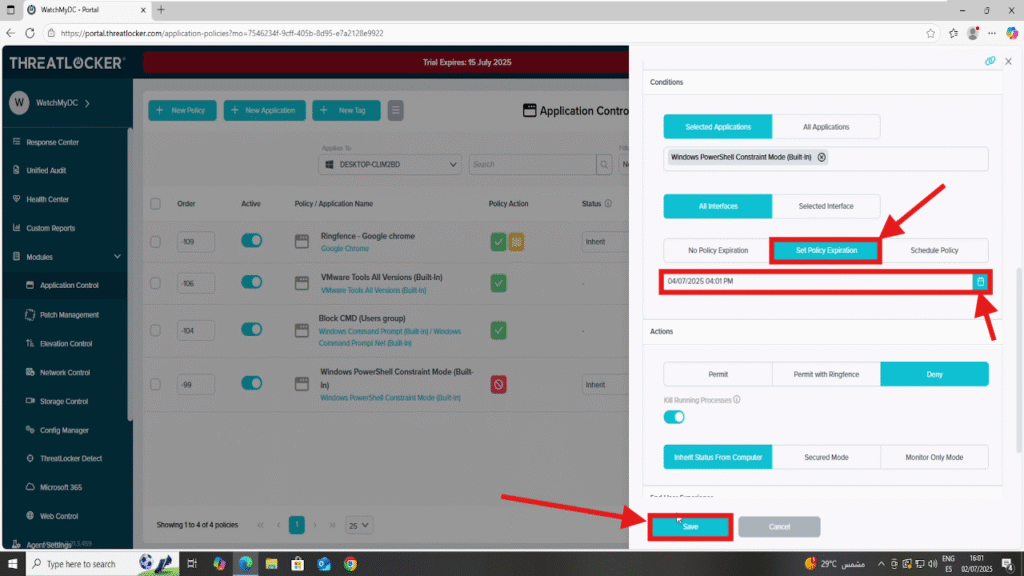
Step 2: Edit the Action Section
- Scroll to the Conditions section of the policy.
- Enable the option Set Policy Expiration.
- Select the expiration date and time when the policy should automatically deactivate.
- Click Save to apply the changes.
Step 2: Deploy to apply the temporary application policy
After making your changes, click the “Deploy” button to apply the updated policy to all relevant endpoints.
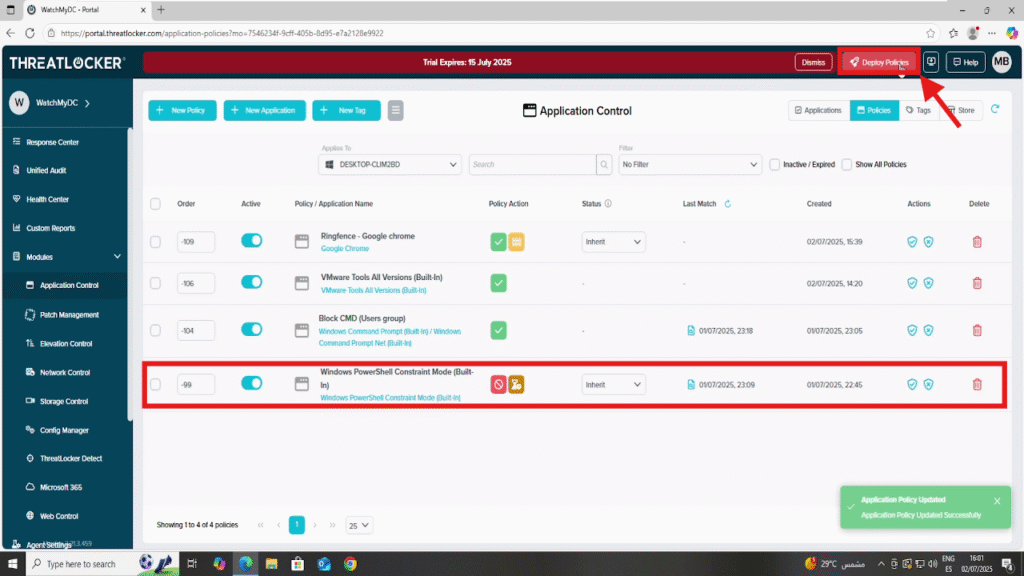
Once deployed, the policy will appear in the list of active policies.
Conclusion
Applying temporary application policies in ThreatLocker gives administrators the flexibility to allow or restrict access for a defined period without the risk of forgetting to disable the policy later.
By using the Policy Expiration feature, you maintain a strong security posture while meeting short-term operational needs, such as software installations, troubleshooting, or temporary exceptions.This automation helps enforce the principles of Zero Trust and ensures that access is always granted with control and accountability.
