
How to approve a blocked application in ThreatLocker?
This document outlines the step-by-step process of how to approve a blocked application in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
ThreatLocker provides an End User Request feature that allows users to request access to a blocked application.
This ensures that application control enforcement remains strict, while still allowing flexibility and fast response from administrators when legitimate software is blocked.In this article, we’ll walk through the steps required to approve a user’s request for a blocked application via the Response Center.
Implementation
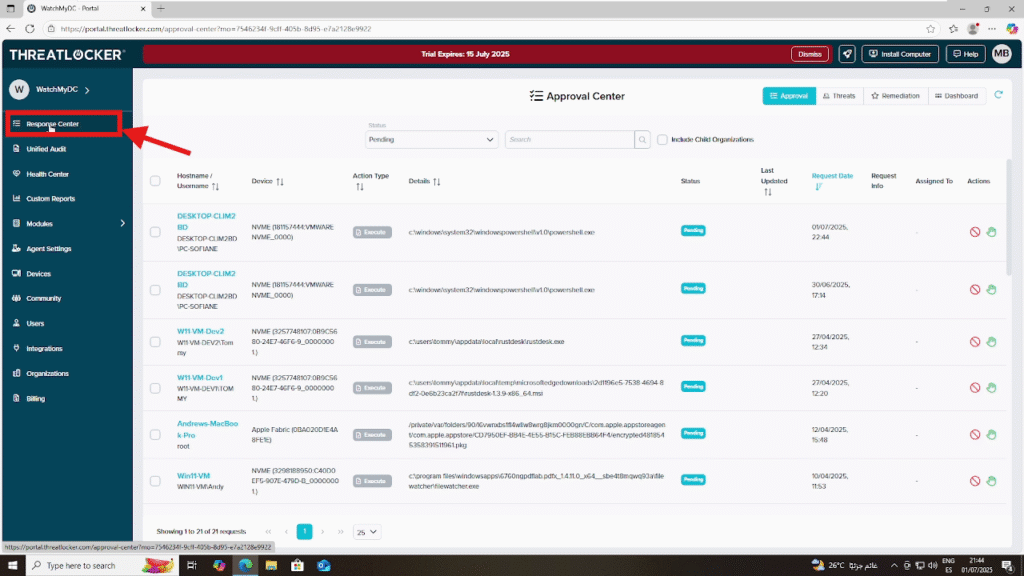
Step 1: Access the Response Center
Log in to the ThreatLocker Portal, then go to the Response Center module.
You will see a list of all recent application access requests submitted by end users.
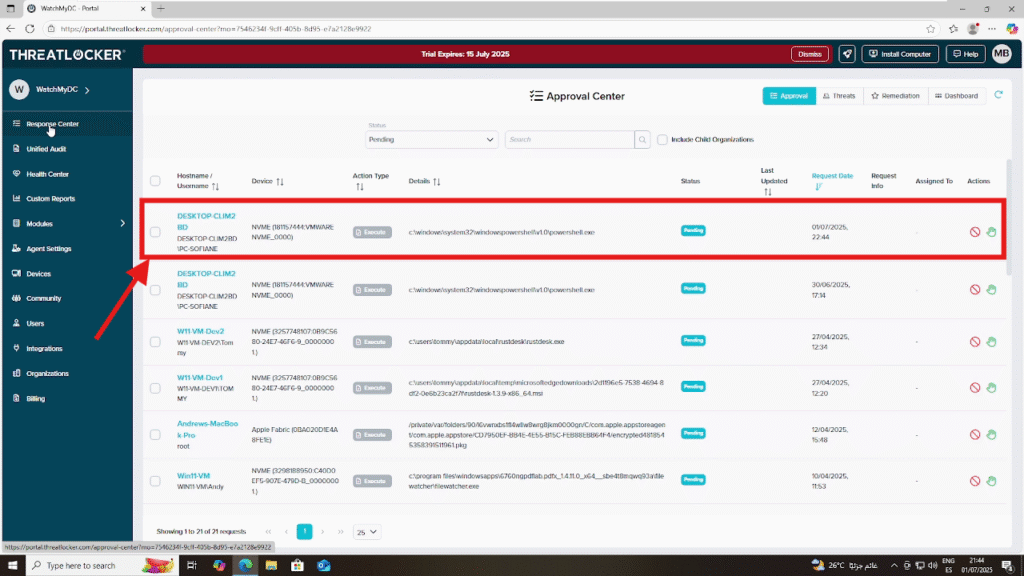
Step 2: Review the Request
Locate the request you wish to approve.
Click the request line to view application details and context (e.g., user, application name, date/time)
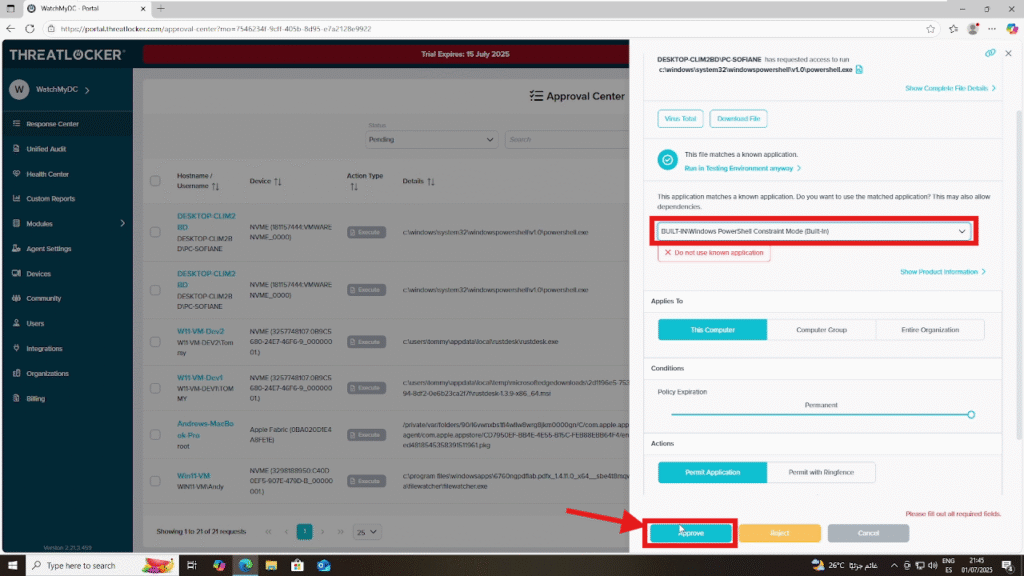
Step 3: Approve the Blocked Application in ThreatLocker
Click on the application name in the request details, then click “Approve” to authorize access.
This will allow the user to run the previously blocked application on their device.
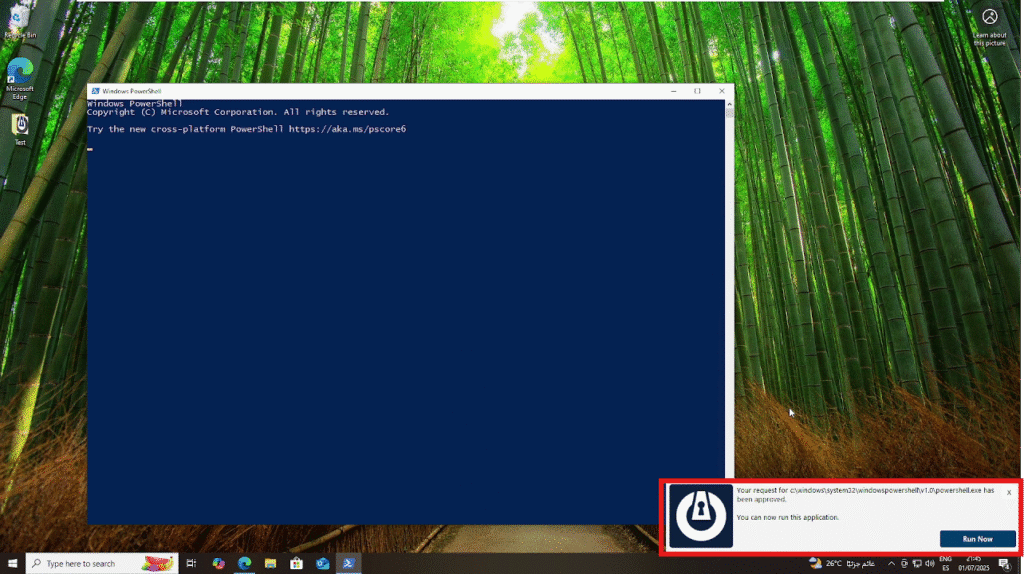
Step 4: User Confirmation
The end user will receive a ThreatLocker popup within a few minutes, confirming the request approval.The user can now click “Run now” to launch the previously blocked application.
Conclusion
Approving a blocked application through the ThreatLocker Response Center offers a secure and efficient way to respond to legitimate user requests without compromising your Zero Trust posture.
By reviewing and approving access only when necessary, administrators maintain full control over which applications are allowed to run, ensuring flexibility without sacrificing security.
