
How to audit existing policies in ThreatLocker?
This document outlines the step-by-step process of how to audit existing policies in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 08 – Policy Management.
Introduction
Auditing your current policies helps ensure they’re working as intended and allows you to review how policies are being applied across your endpoints.ThreatLocker’s Unified Audit provides full visibility into all policy activity, including which policies allowed or blocked actions.
Implementation
Step 1: Access Unified Audit
- Log in to the ThreatLocker Portal.
- Navigate to Unified Audit
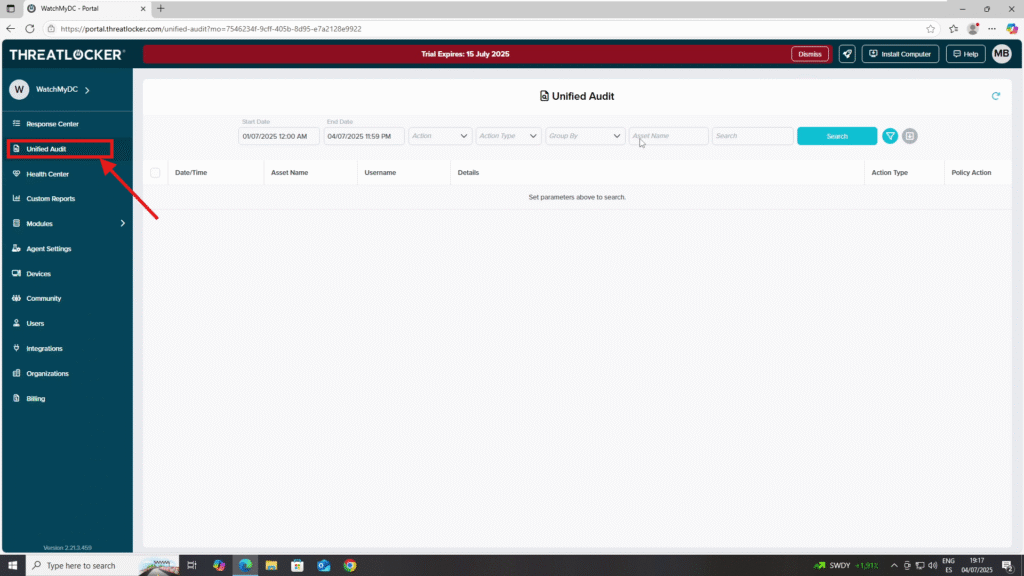
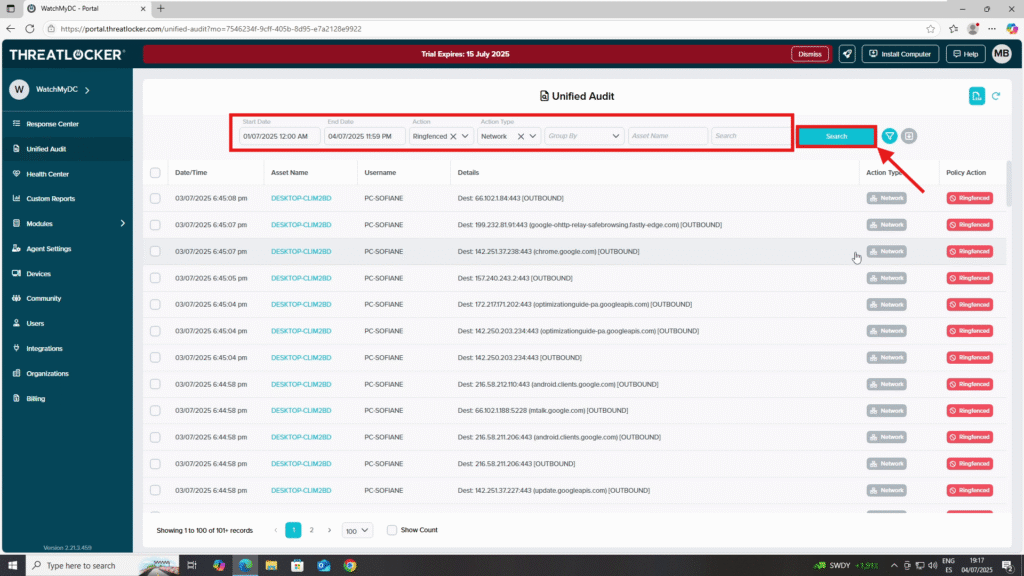
Step 2: Configure the Filters to Review Policy Actions
- In the filter section, set your criteria:
- Date Range: Select a start and end date to define the audit period
- Action: Filter by the action result, such as Deny, Permit, or Ringfenced
- Action Type: Choose the relevant module you want to audit (e.g., Application, Storage, Elevation, Network)
- Click Search to view the results
- You’ll see detailed logs including:
- Date/Time
- Asset Name
- Username
- Details
- Action Type
- Policy Action
Conclusion
By using the Unified Audit, you gain insight into which policies are actively enforcing controls, and how users interact with them.
This allows you to:
- Validate policy effectiveness
- Identify unnecessary or outdated rules
- Support compliance reporting
- Investigate security events quickly
Regular auditing is a key part of maintaining a strong Zero Trust security model with ThreatLocker.
