
How to audit ringfencing activity in ThreatLocker?
This document outlines the step-by-step process of how to audit ringfencing activity in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 06 – Network Control & Ringfencing.
Introduction
Ringfencing is a powerful feature in ThreatLocker that restricts how applications interact with files, the registry, the network, and other applications. To ensure your policies are working as intended and to detect potential threats, you can audit ringfencing activity using the Unified Audit module.
This guide explains how to review all events related to ringfencing policies in your environment.
Implementation
Step 1: Access Unified Audit
- Log in to the ThreatLocker Portal.
- Navigate to Unified Audit
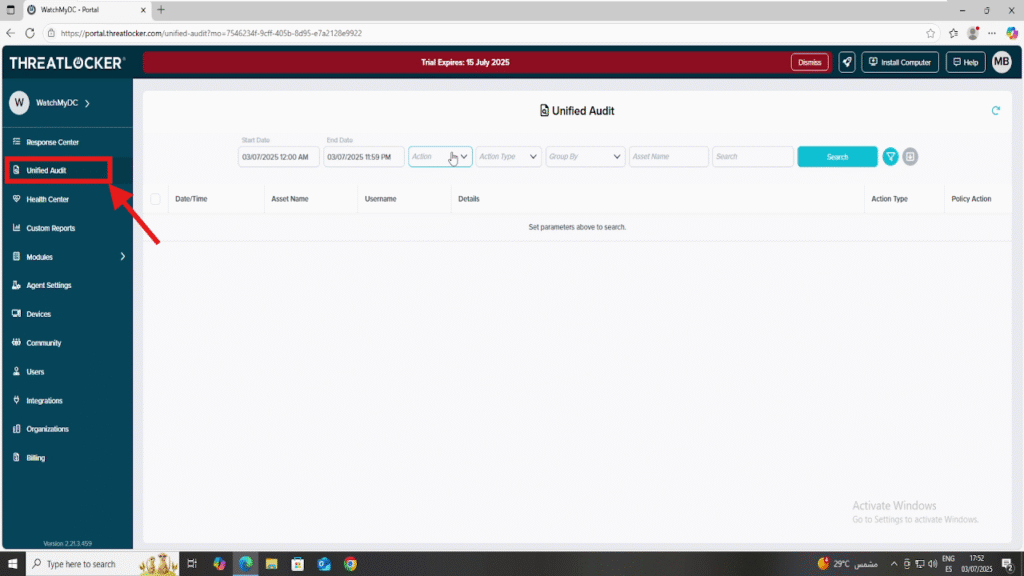
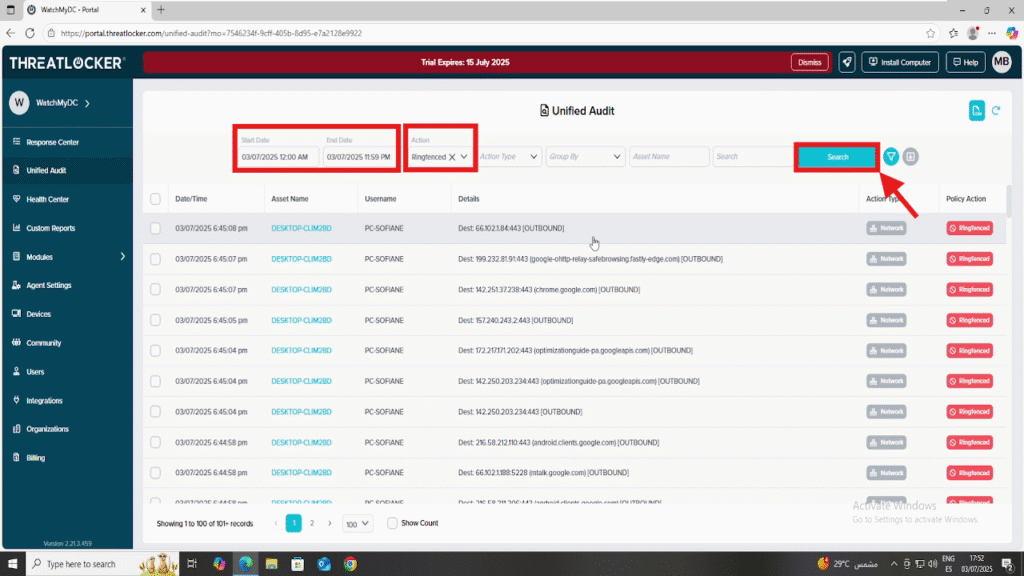
3. In the filter fields, configure the following:
- Date Range: Select a start and end date to define the time period
- Action: Set to Ringfenced
- Click Search to display the logs
- A list of events can be seen with detailed information, including Date/Time, Asset Name, Username, Details, Action Type, and Policy Action.
Conclusion
Auditing ringfencing activity gives you visibility into blocked actions and application behavior that violates your security rules.
By regularly checking these logs, you can:
- Detect unusual or malicious activity
- Validate that your ringfencing policies are effective
- Improve your Zero Trust strategy through data-driven decisions
ThreatLocker Unified Audit makes it easy to monitor and investigate all ringfencing events across your environment.
