
How to block USB storage devices in ThreatLocker?
This document outlines the step-by-step process of how to block USB storage devices in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 05 – Storage Control.
Introduction
USB storage devices present a significant risk to endpoint security, from data exfiltration to malware infections.
ThreatLocker’s Storage Control module provides granular control over external storage access, allowing administrators to block USB drives entirely or selectively.In this guide, we’ll walk through the step-by-step process of blocking all USB storage devices using a custom policy.
What is USB control?
USB Control helps secure your environment by limiting how and when storage devices can be accessed on endpoints. It enables policies such as read-only access, full blocking, or allowing only encrypted devices.
Objective
The goal is to prevent unauthorized data transfer and reduce the risk of malware introduced through external devices.
In this guide, we’ll walk through the step-by-step process to block USB storages by creating a policy using the ThreatLocker Storage Control module.
Implementation
Step 1: Access the Storage Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Storage Control.
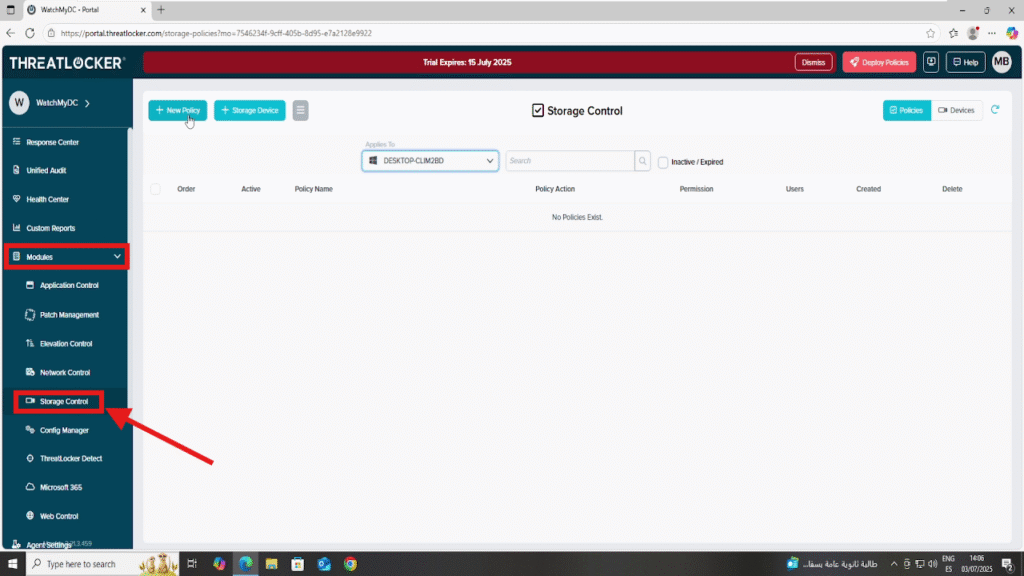
Step 2: Create or Modify a USB Blocking Policy
1. In the Storage Control module, locate the policy you want to modify:
- If a USB policy already exists, click on it to modify.
- If no such policy exists, click Create Policy to start a new one.

2. In the Policy Details section:
- Name: e.g., USB Control Policy
Description: Control USB devices.
3. In the Apply To section:
- Select the appropriate Computer Group or specific devices where the policy will be applied.

4. In the Conditions section, configure the USB access parameters:
- Access Type: Choose either
- Read or
- Read/Write depending on the level of access you want to allow.
- Interface Type:
- Select Selected Interfaces, then choose USB to specifically block USB ports.
- Program Filter:
- Leave set to All Programs, unless you need to restrict specific ones.
- Device Filter:
- Choose among:
- All Devices
- Encrypted Devices Only
- Non-Encrypted Devices Only
- Choose among:

5. In the Action section:
- Set Action to Deny
- Enable “Allow User to Request” to give users a way to submit a request for temporary access.
6. Once everything is configured:
- Click Save to save the policy.

- Then click Deploy from the policy list to apply it to the selected endpoints.

Conclusion
Blocking USB storage devices using ThreatLocker’s Storage Control ensures that only authorized peripherals can interact with your endpoints. This proactive control helps protect your environment against data leakage, malware injection, and unauthorized file transfers.
By applying a deny policy with clearly defined interface restrictions (e.g., USB) and enabling the user request option, organizations can enforce strong security while maintaining flexibility when legitimate access is needed.
This approach is an essential part of a Zero Trust strategy, reinforcing endpoint security without compromising productivity.
