
How to Convert Learning Events to Policies?
This document outlines the step-by-step process of how to convert learning events to policies in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 04 – Learning and Training Mode.
Introduction
During Learning Mode, ThreatLocker logs all application activity on endpoints without enforcing restrictions. These observed events are invaluable for building precise, context-aware Application Control policies.
By reviewing and converting these events into allow or deny rules, administrators can ensure a smooth transition from learning to enforcement mode minimizing user disruption while strengthening security.
In this article, we’ll walk through the steps to convert learning events into enforceable policies directly from the ThreatLocker Unified Audit logs.
Implementation
Step 1: Access the Unified Audit Log
- 1. Log in to the ThreatLocker Portal.
- 2. Navigate to Unified Audit from the left-hand menu.
- 3. Apply filters to refine the audit results:
- Action Type: Select Execute to focus on application execution events.
- Time Range: Set the start and end dates to match the period during which Learning Mode was active.
- Search by Asset: Enter the target device name to isolate logs for a specific endpoint.
Once filters are applied, click Search to display the relevant events captured during Learning Mode.
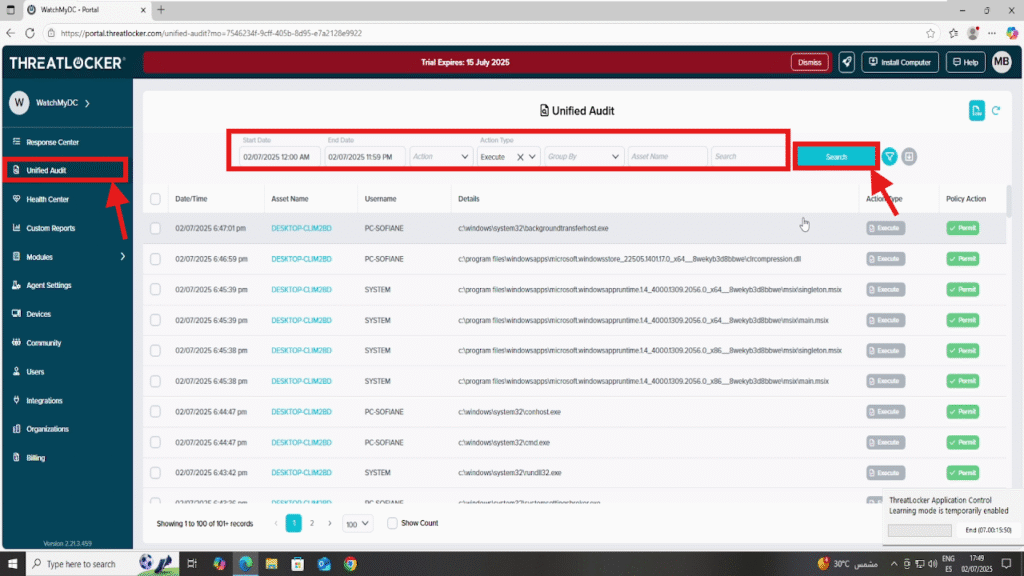
Step 2: Review and Convert Learning Events into Policies
1. From the filtered audit log results, locate the event you want to convert into a policy (e.g., in this example, cmd.exe).
2. Click on the event to open the detailed view.
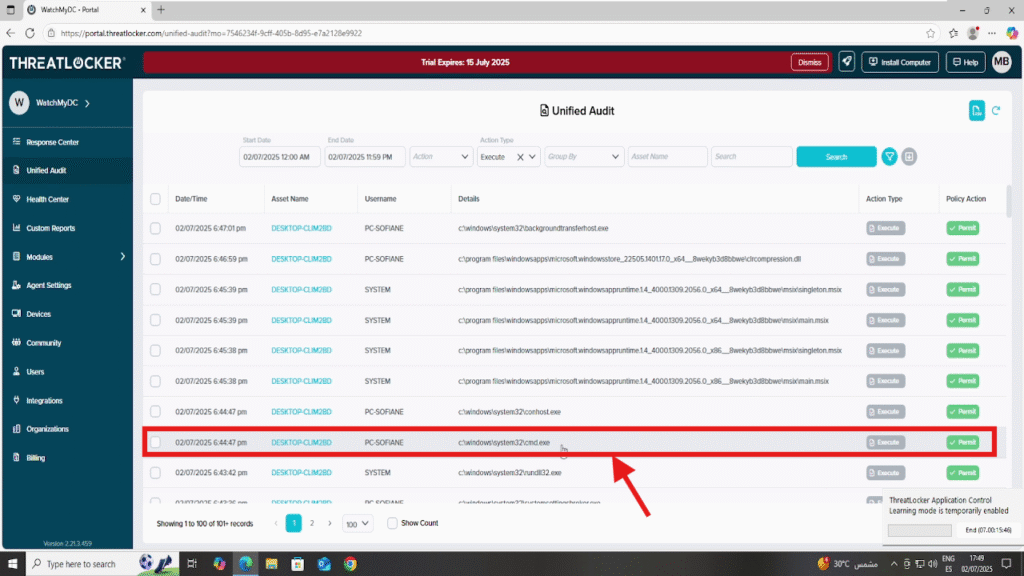
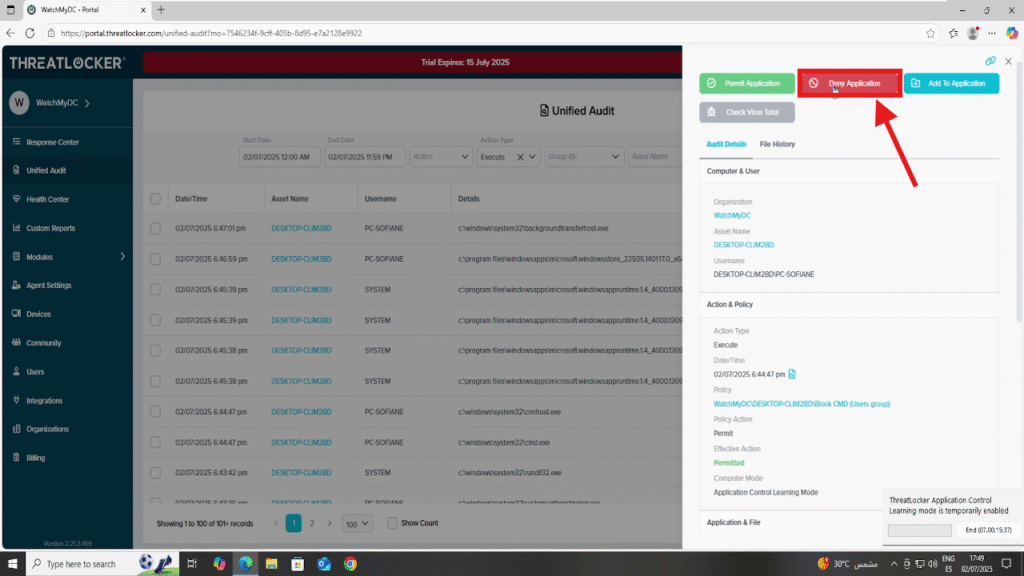
3. In the event details panel, click Permit Application or Deny Application, depending on your intent. In this case, we’re going to block cmd.exe, so we click Deny Application.
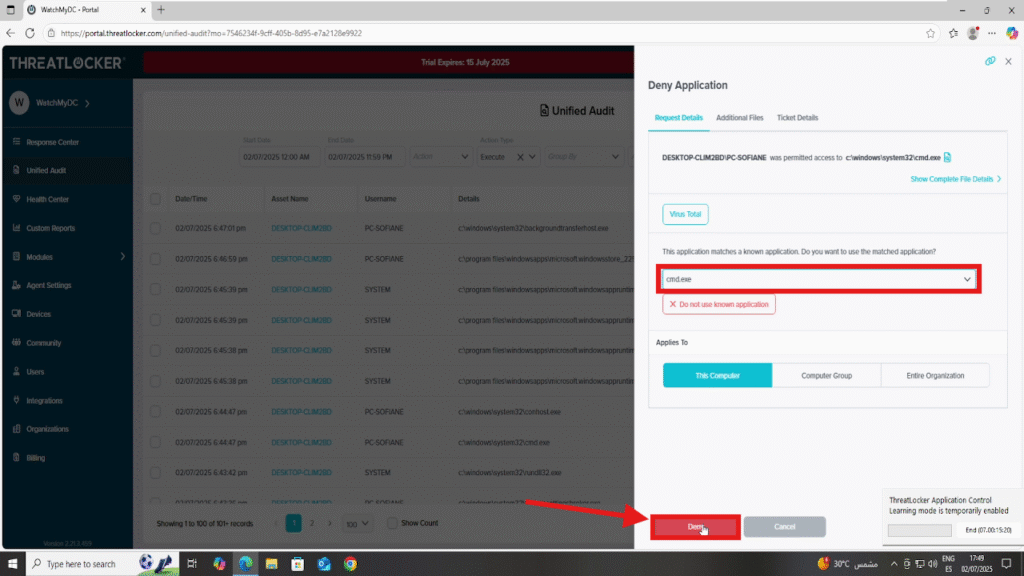
4. The policy creation form will open automatically. Verify the application name, then click ‘Deny’ to finalize the policy creation.
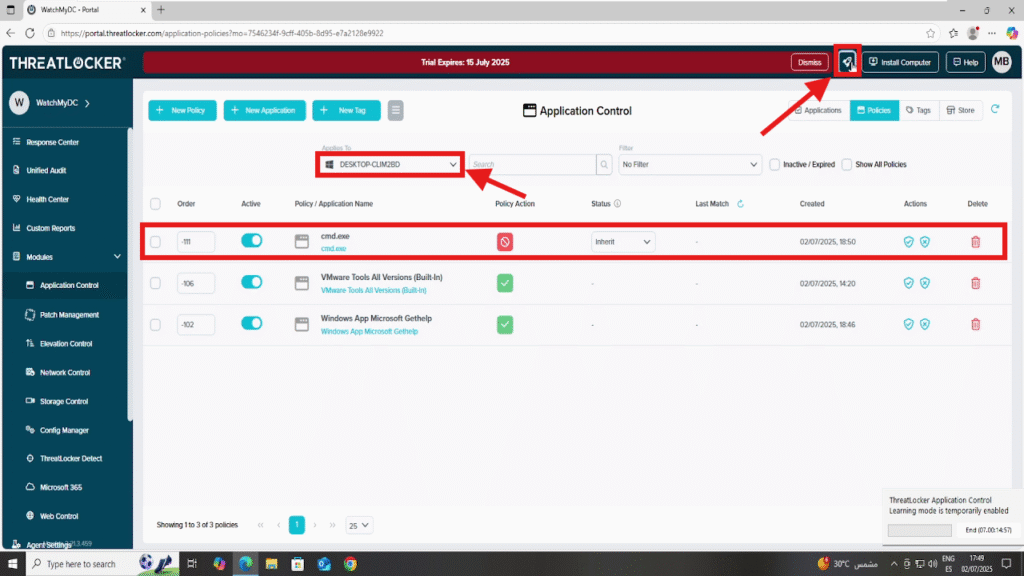
To confirm that the policy has been successfully created:
- Navigate to Modules > Application Control > Policies.
- Use filters to find the device group where the policy was applied.
- You should now see the newly created policy listed and ready for deployment
Conclusion
Converting Learning Mode events into policies is a crucial step in transitioning from observation to enforcement in ThreatLocker.
By carefully reviewing activity logs and selectively approving or denying applications, administrators can build a precise Zero Trust environment tailored to their organization’s needs.
This method ensures that only verified software is allowed while minimizing disruptions, making it easier to maintain both productivity and security as enforcement is rolled out.
