
How to create elevation policies for installers in ThreatLocker?
This document outlines the step-by-step process of how to create elevation policies for installers in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 07 – Elevation Control (Privilege Management).
Introduction
Some applications require administrator rights to install properly. Instead of granting full admin access to end users, ThreatLocker allows you to create elevation policies that give temporary elevated privileges only for approved applications.In this guide, you’ll learn how to create an elevation policy for a specific installer based on its activity in Unified Audit.
Implementation
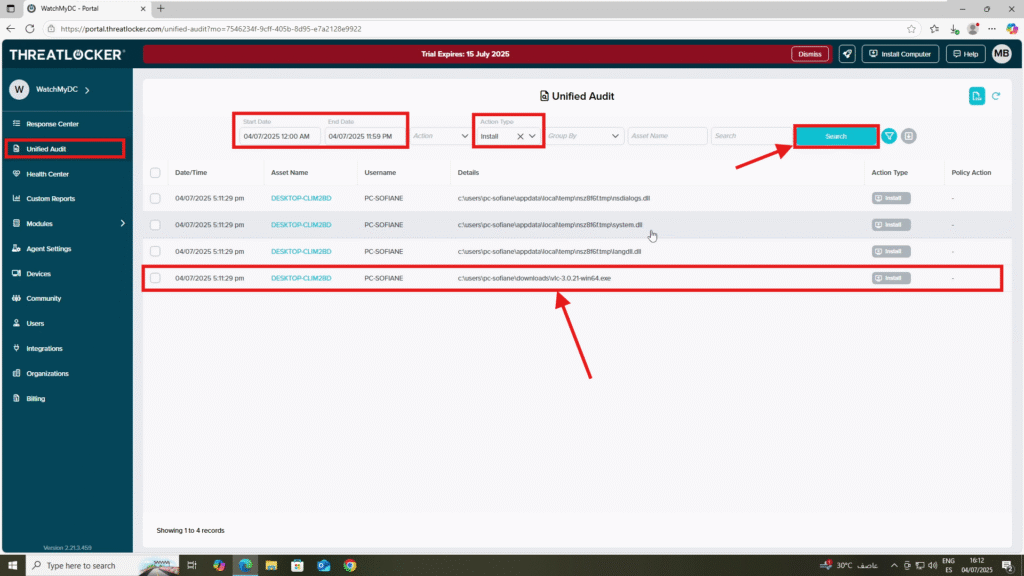
Step 1: Locate the Installer Activity in Unified Audit
- Log in to the Unified Audit.
- Navigate to Modules > Application Control
- In the filter section, configure the following:
- Date Range: Set the start and end date
- Action Type: Select Install
- Click Search, then locate the relevant log entry for the installer
- Click on the log to open the details window
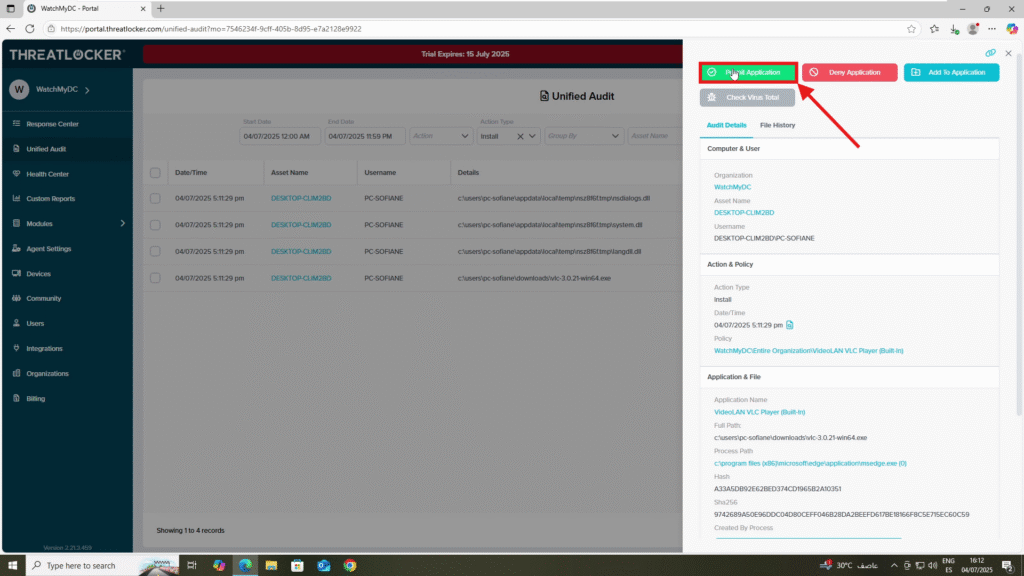
Step 2: Approve the Installer as an Elevated Application
- In the Details window, click Permit Application
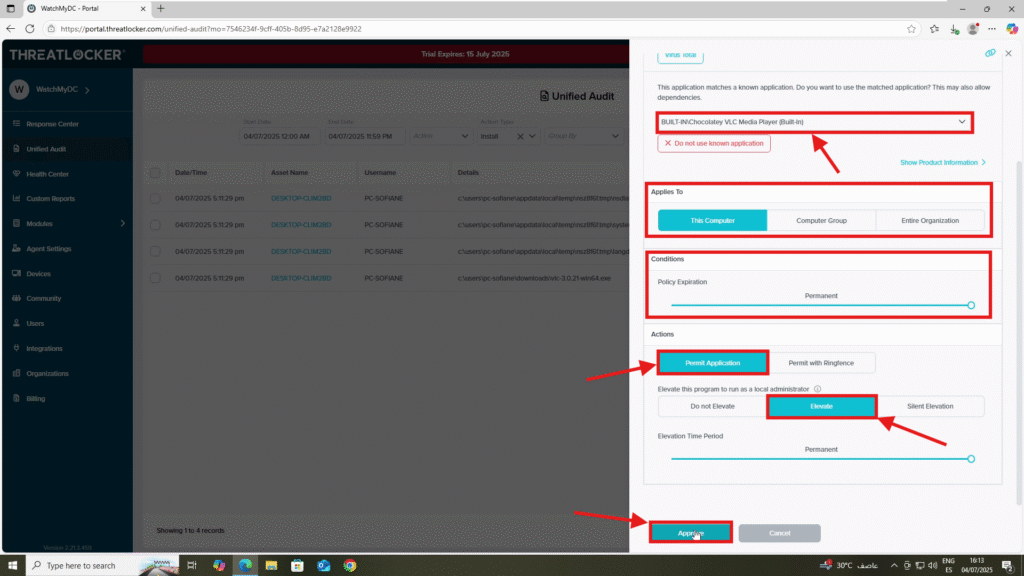
2. Fill the policy form:
- Name: Enter the name of the application or installer
- Applied To: Choose the scope of the policy (This computer, a group of computers, or the entire organization)
- Condition section: Select No Policy Expiration
- Action section:
- Select Permit Application
- Under “Elevate this program to run as a local administrator”, select the option Elevate to allow the program to run with admin privileges.
- Set the elevation time period (e.g., 1 hour)
3. Click Approve to finalize the policy
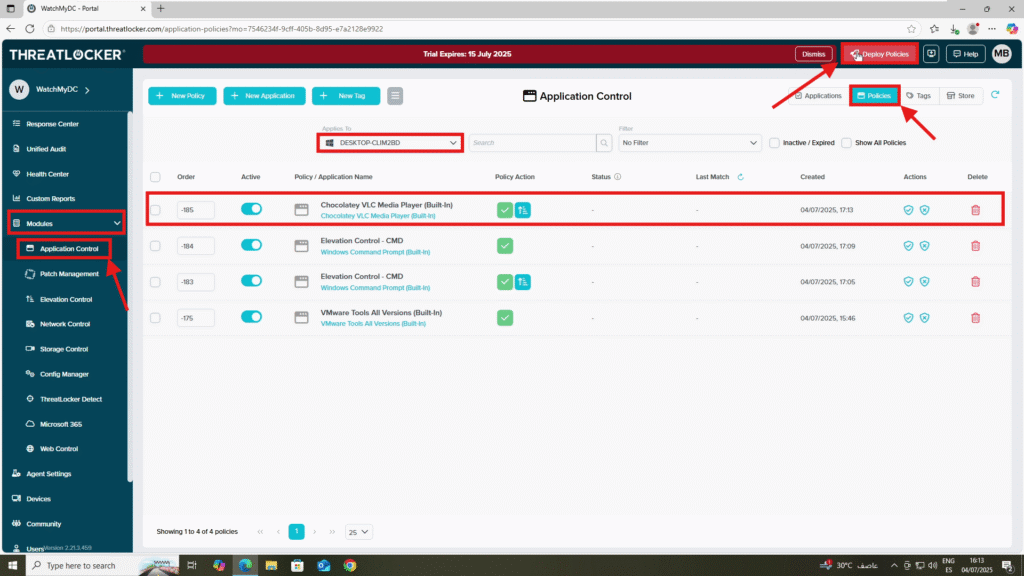
Step 3: Deploy the Policy to create elevation policies for installers in ThreatLocker
- Navigate to Modules > Application Control > Policies
- Verify that the policy has been created and is listed under the correct computer or group
- Click Deploy to enforce the policy
Conclusion
By creating elevation policies for installers through ThreatLocker, strong control can be maintained over what can run with administrator rights.
This approach helps to:
- Avoid giving permanent admin access to users
- Limit elevation to only trusted, approved applications
- Enforce Zero Trust without slowing down installation workflows
Using Unified Audit ensures that policies are based on real activity, giving you both security and flexibility.
