
How to create a policy for a single user?
This document outlines the step-by-step process of how to create a policy for a single user in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
ThreatLocker allows administrators to apply granular security policies, not only per device or group, but also per user.
This is especially useful when you want to restrict or allow specific applications for a single person without affecting others.This guide explains how to create an Application Control policy targeting one user only.
Implementation
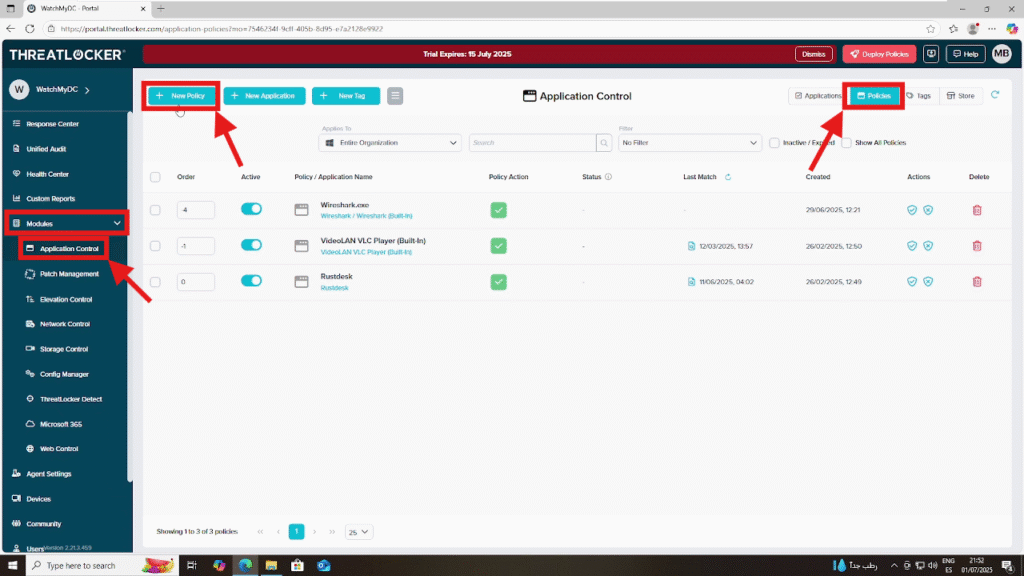
Step 1: Access the Application Control Policies
Log in to the ThreatLocker Portal, then go to: Modules > Application Control > PoliciesClick on “Create Policy” to begin configuring a new rule.
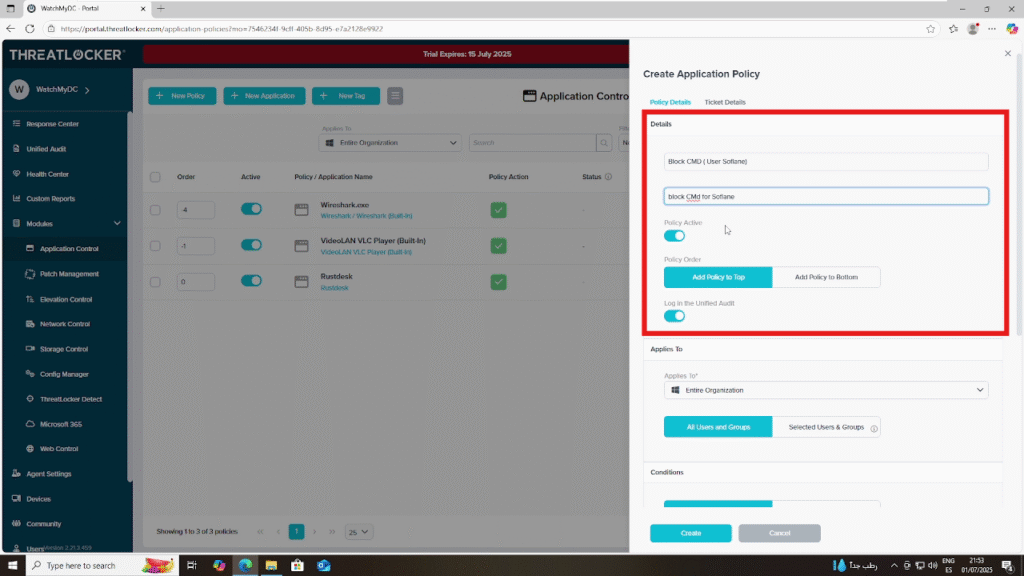
Step 2: Complete the Policy Form
Fill in the Policy Details section:
- Name: e.g., Block CMD.
Description: Add a short explanation of the policy’s purpose (e.g., Deny access to command prompt for user Sofiane)
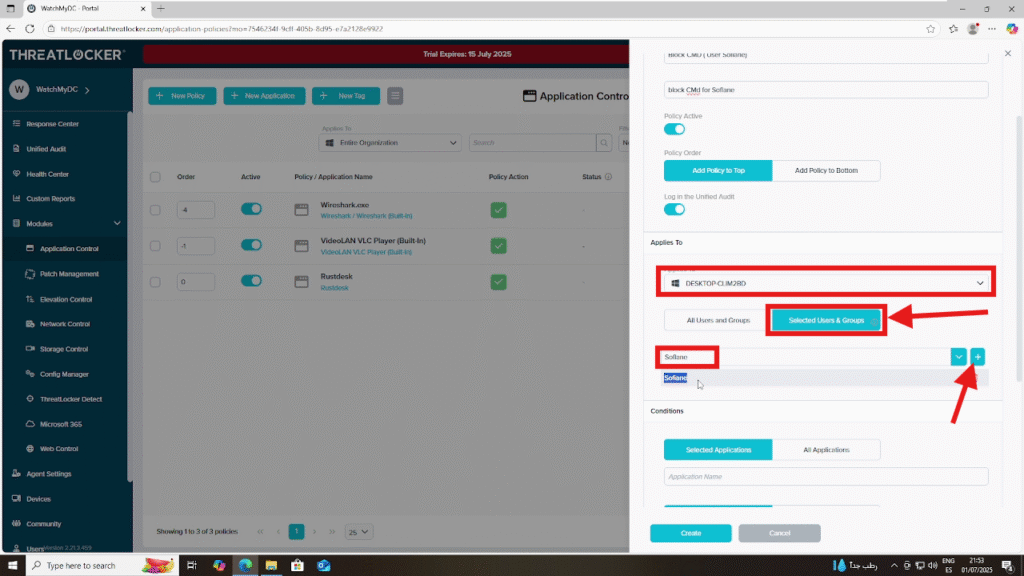
In the Apply To section:
Select the computer group where you want this policy to be applied.Then, click on “Selected User and Group” and add the target user account, in this example, Sofiane.
In the Condition section, choose the application you want to block.Then, in the Action section, select “Deny”, enable End User Experience (e.g., show notification and allow user to request access), and click “Create” to finalize the policy.
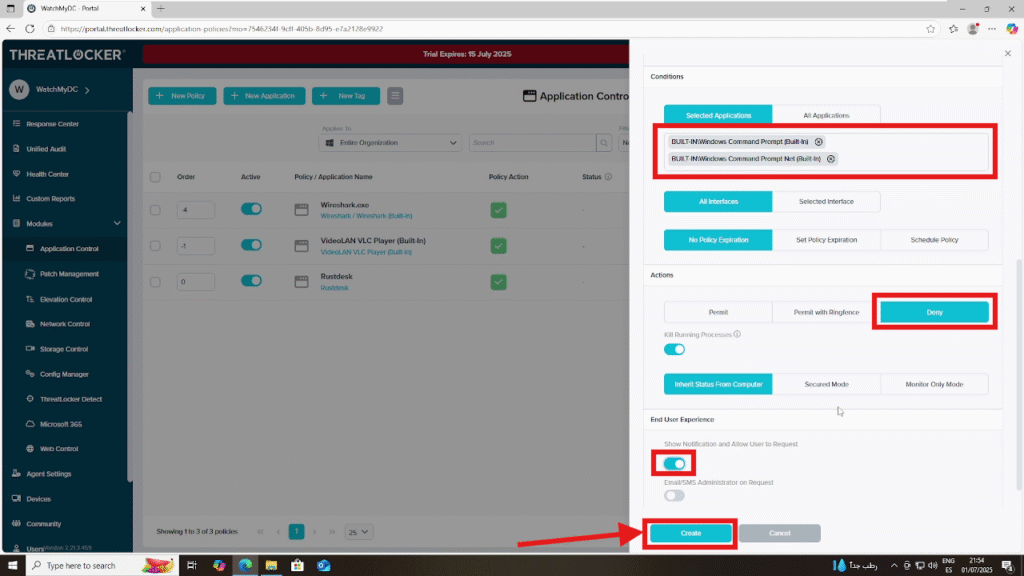
Step 3: Deploy the Policy To create for a single user
After creating the policy, click “Deploy” to apply it to the selected user and devices.
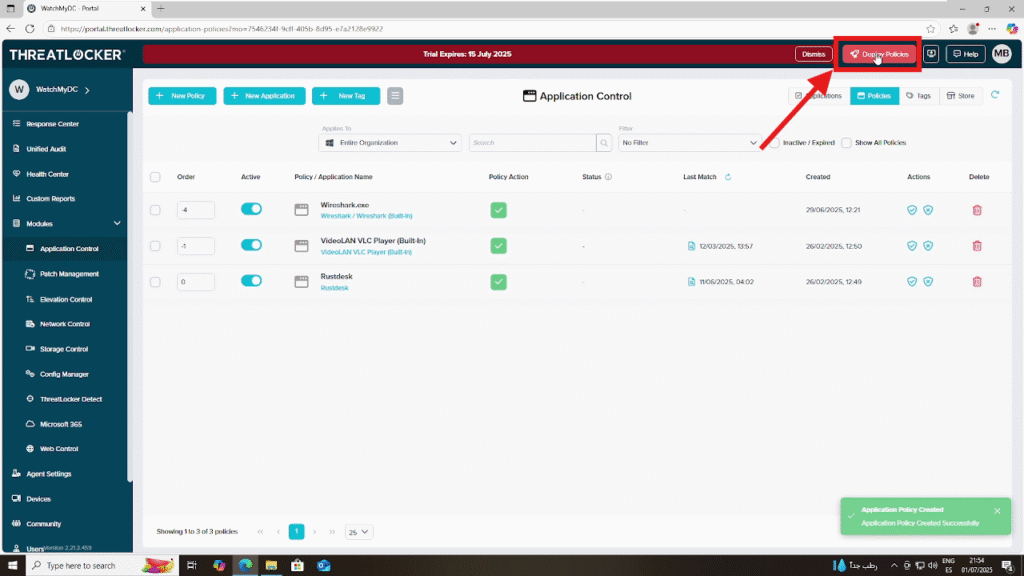
Once deployed, the policy will appear in the list of active policies.
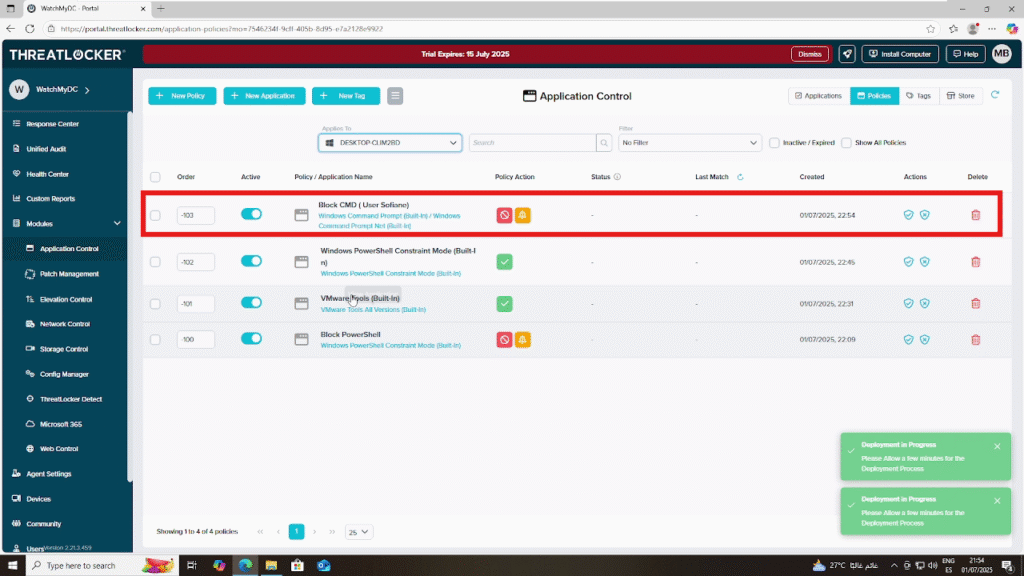
Conclusion
Creating a user-specific policy in ThreatLocker gives you precise control over application access, tailored to individual users without affecting the entire group or organization.
By targeting a single user and specifying the application and action, you strengthen your Zero Trust security posture while maintaining operational flexibility.
Once deployed, the policy takes effect immediately and ensures that only authorized users can run sensitive tools or applications.
