
How to deny elevation for specific processes in ThreatLocker?
This document outlines the step-by-step process of how to deny elevation for specific processes in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 07 – Elevation Control (Privilege Management).
Introduction
To reduce the risk of privilege abuse, you can explicitly deny elevation for certain processes that should never run with administrator rights. With ThreatLocker, it’s easy to detect elevation attempts and create policies that block them from being elevated.This guide explains how to deny elevation for a specific process using Unified Audit and Application Control.
Implementation
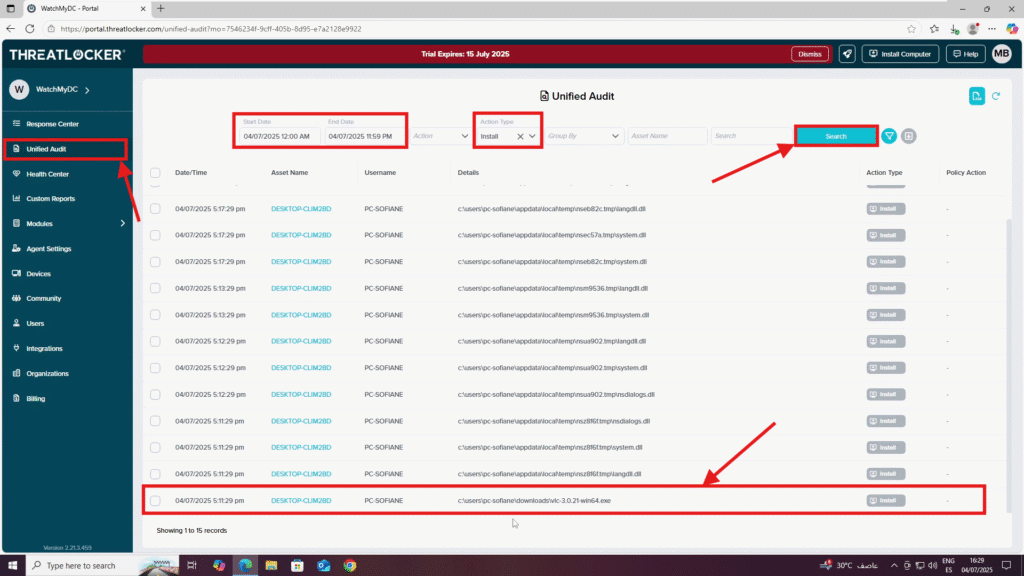
Step 1: Locate the Installer Activity in Unified Audit
- Log in to the Unified Audit.
- Navigate to Modules > Application Control
- In the filter section, configure the following:
- Date Range: Set the start and end date
- Action Type: Choose the relevant process type (e.g., Elevate, Network, etc.)
- Click Search, then locate the relevant log entry for the installer
- Click on the log to open the details window
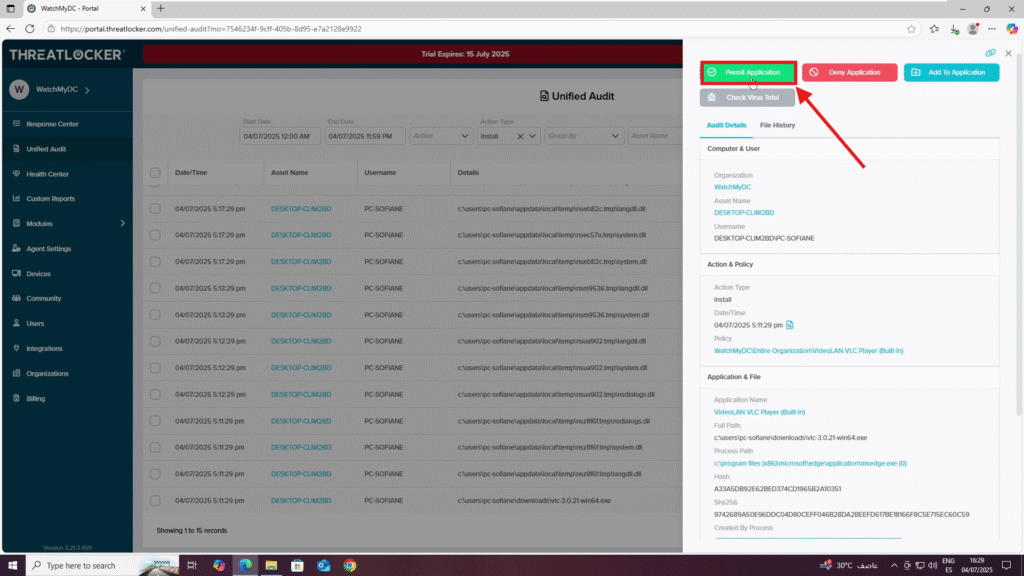
Step 2: Deny Elevation for the Process
- In the Details window, click Permit Application
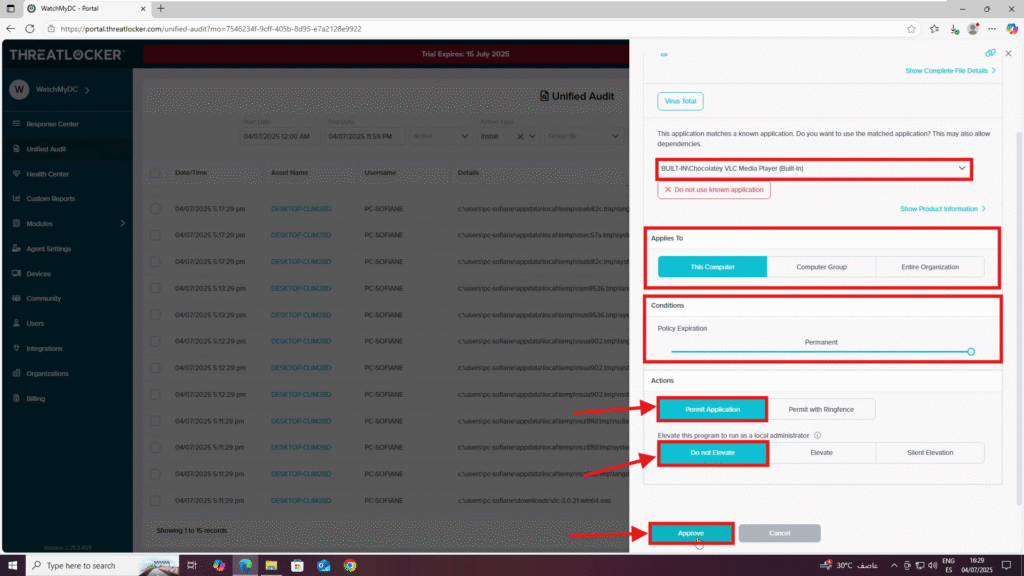
2. Complete the approval form:
- Name: Enter the name of the application or installer
- Applied To: Choose the scope of the policy (This computer, a group of computers, or the entire organization)
- Condition section: Select No Policy Expiration
- Action section:
- Select Permit Application
- Under “Elevate this program to run as a local administrator”, select Do Not Elevate to block elevation.
3. Click Approve to finalize the policy
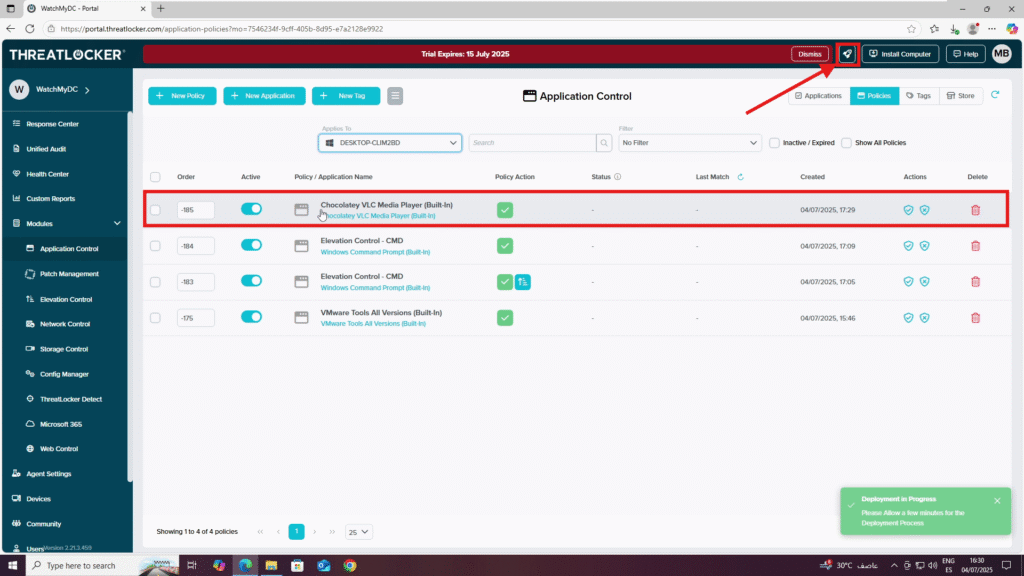
Step 3: Verify and Deploy the Policy to deny elevation for specific processes in ThreatLocker
- Navigate to Modules > Application Control > Policies
- Verify that the policy has been created and is listed under the correct computer or group
- Click Deploy to enforce the policy
Conclusion
Blocking elevation for specific processes helps you enforce the principle of least privilege and reduce the attack surface.
By using ThreatLocker’s Unified Audit and Application Control, you can easily identify risky elevation attempts and stop them with a targeted policy, without impacting trusted applications.
