
How to deny software based on Publisher?
This document outlines the step-by-step process of how to deny software based on publisher in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
ThreatLocker’s Application Control module allows administrators to block or allow software using various criteria such as file name, path, hash, certificate, or publisher. Blocking software based on the publisher is especially useful when you want to prevent entire suites of applications, for example, all programs signed by “Google LLC” or “TeamViewer GmbH”, without needing to block each executable file individually.
Implementation
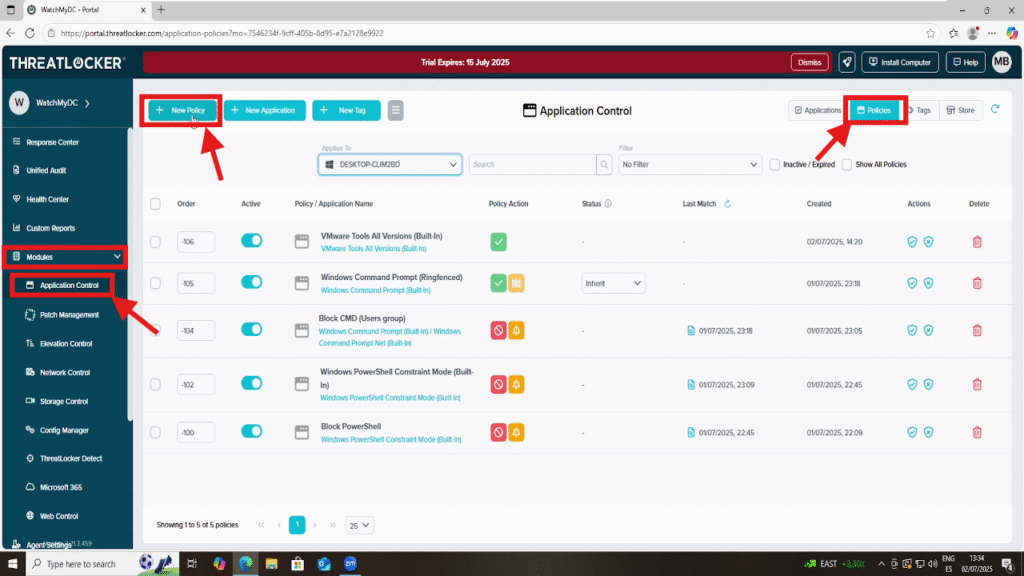
Step 1: Access the Application Control Policy Section
Log in to the ThreatLocker Portal, then go to Module > Application Control > Policies, and click Create Policy.
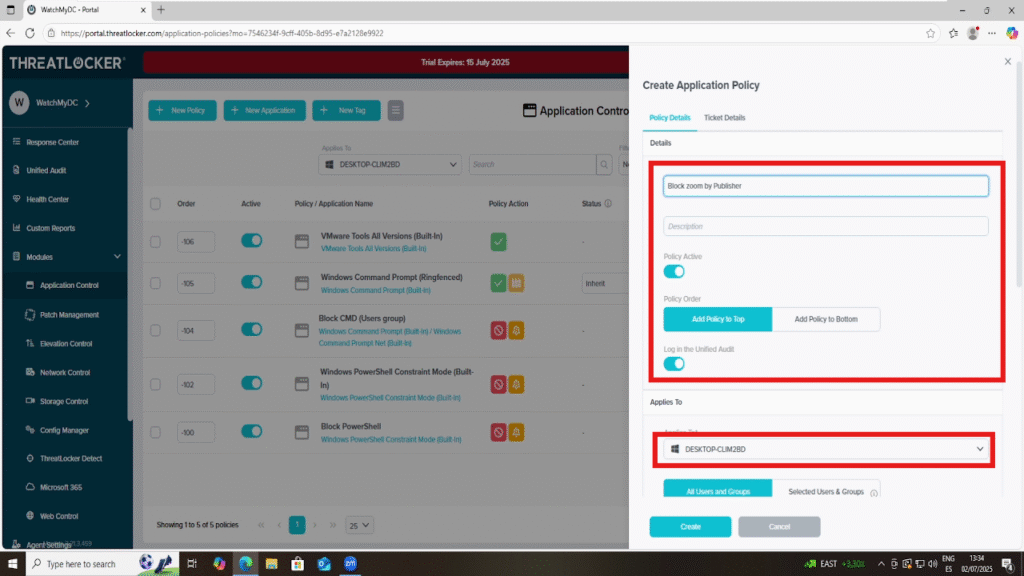
Step 2: Complete the Policy Form
In the Policy Details section:
- Name: Give the policy a clear name.
Example: Block Zoom by Publisher
- Description: Write a short explanation of what this policy does.
Example: This policy blocks all applications signed by Zoom Video Communications, Inc.
In the Apply To section:
- Choose the appropriate Computer Group or User Group where this policy should be enforced.
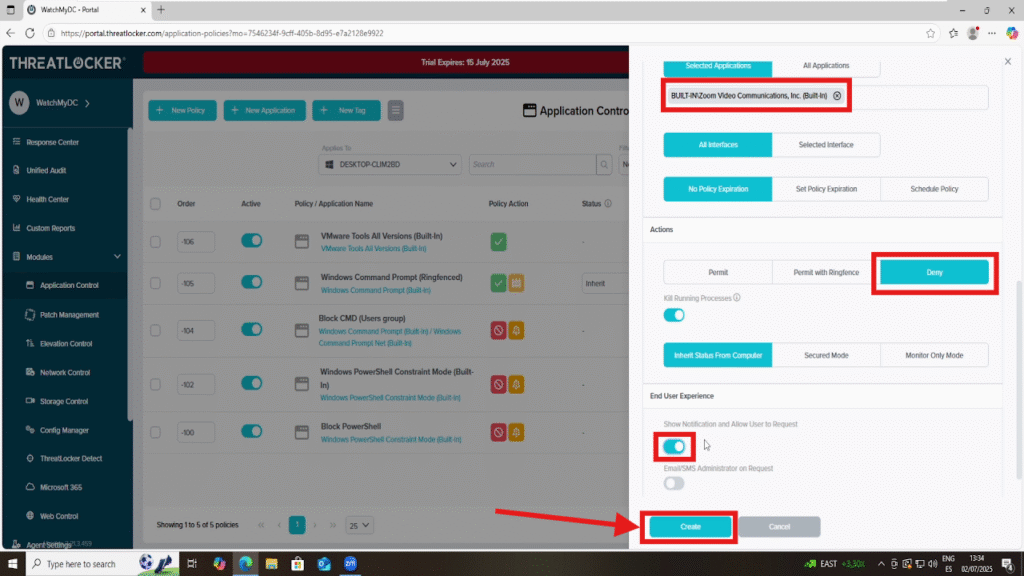
At Condition section:
- Input the exact Publisher Name as it appears in the Unified Audit.
- Example: Zoom Video Communications, Inc.
Now in the Action section:
- Set the Action to: Deny
- Enable End User Experience, (show notification and allow user to request)
Finally, click Create to save and Deploy to apply the policy.
Conclusion
Blocking software by publisher in ThreatLocker gives administrators the ability to efficiently restrict entire software families with a single policy.This method is especially valuable for limiting tools like TeamViewer, Zoom, or Google Chrome, which are signed under consistent publisher certificates.
Once deployed, the policy is immediately enforced across all selected users, ensuring that only authorized personnel can access sensitive or restricted tools.
