
How to Deploy the Agent Using Group Policy (GPO)
This document outlines the step-by-step process to deploy the ThreatLocker agent using Group Policy (GPO). ThreatLocker Agent installation is essential to enable centralised management and policy enforcement on endpoints from the ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 01 – Installation & Deployment.
Introduction
What is GPO and Why Use It?
Group Policy Object (GPO) is a feature in Microsoft Windows that allows administrators to centrally manage and configure operating systems, applications, and user settings within an Active Directory environment.
Using GPO simplifies the deployment of software and policies across multiple computers, ensuring consistency, saving time, and improving security.
Objective To Deploy the Agent Using Group Policy (GPO)
The goal of this guide is to automate the deployment of the ThreatLocker agent to all targeted devices within the domain using GPO and an MSI installer.
Implementation
There are two main types of ThreatLocker agent installation, depending on your environment and deployment scale:
- Manual Installation – Suitable for small environments or individual machines.
- Automated Installation (RMM or Script-based) – Recommended for large-scale or remote deployments.
However, In this document, we will focus on the Manual Installation method, using the Stub EXE installer for a Microsoft Windows PC
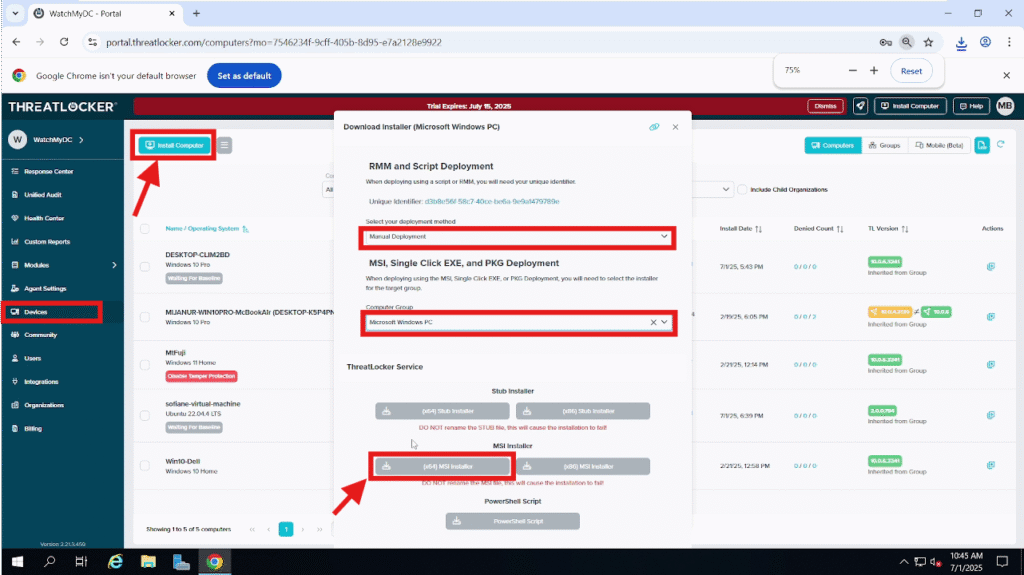
Step 1: Download the MSI Installer
After logging into the ThreatLocker Portal, navigate to the Devices section and click on Install Agent. From there, select and download the appropriate MSI installer based on your environment (32-bit or 64-bit). This step is essential to prepare for the automated deployment of the agent using Group Policy (GPO).
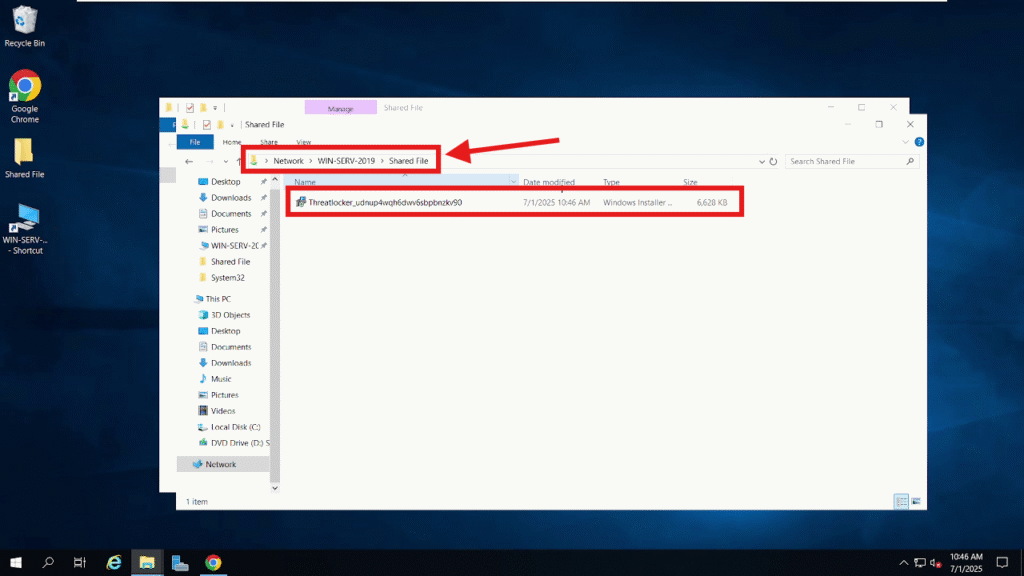
Step 2: Store the MSI Installer in a Shared Network Folder
Create a shared folder that is accessible to all target machines on your network (for example: \\WIN-SERV-2019\Shared file\). Place the downloaded MSI installer inside this folder. Ensure that all domain-joined computers have at least read access to this shared location so they can retrieve the installer during deployment.
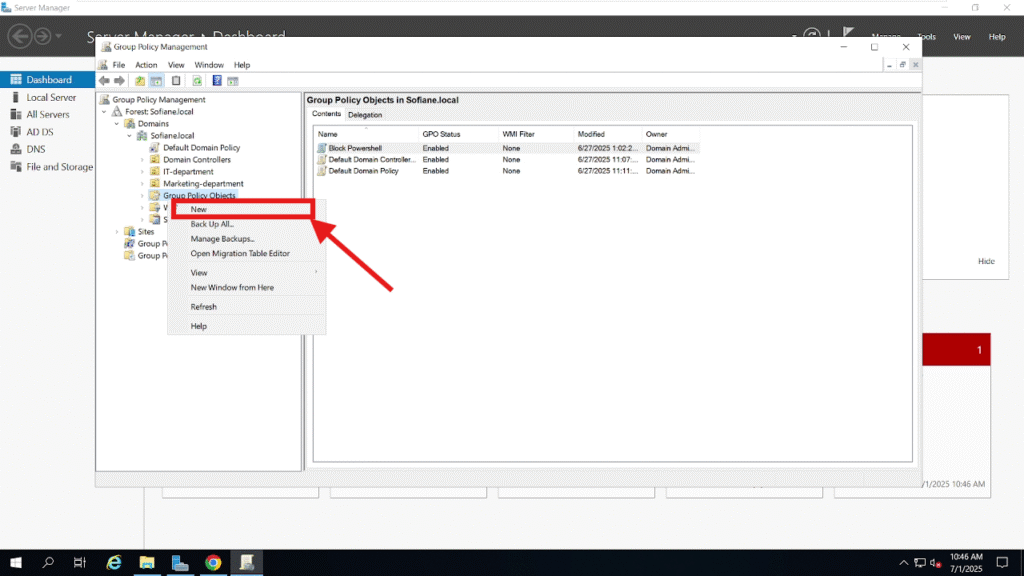
Step 3: Create a New Group Policy
Open the Group Policy Management Console on your domain controller. In the left-hand panel, right-click on Group Policy Objects, then click on New to create a new GPO.
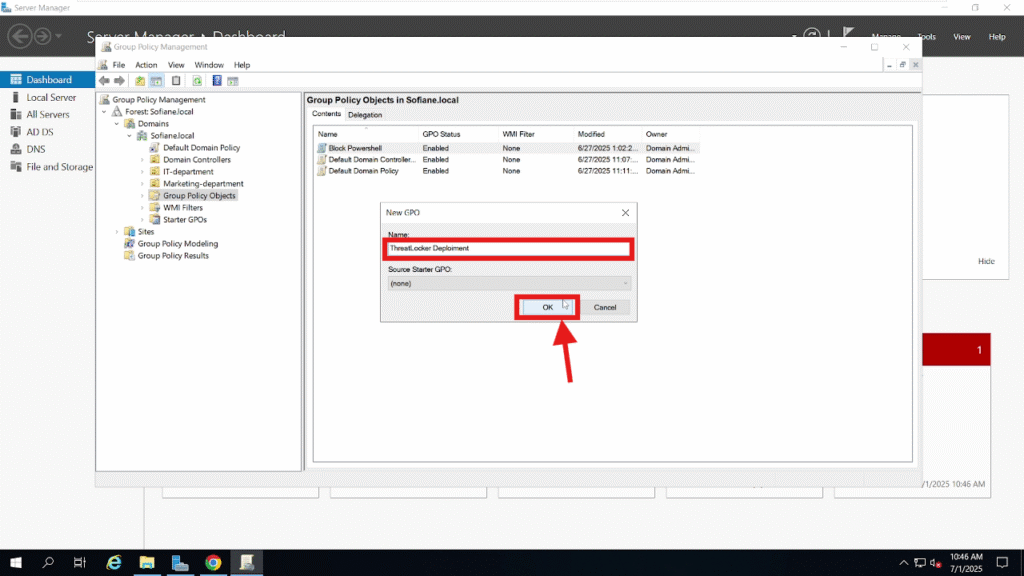
Name the policy something descriptive, such as ThreatLocker Deployment.
Step 4: Edit the GPO to Deploy the MSI
Once the GPO is created, right-click on it and select Edit:
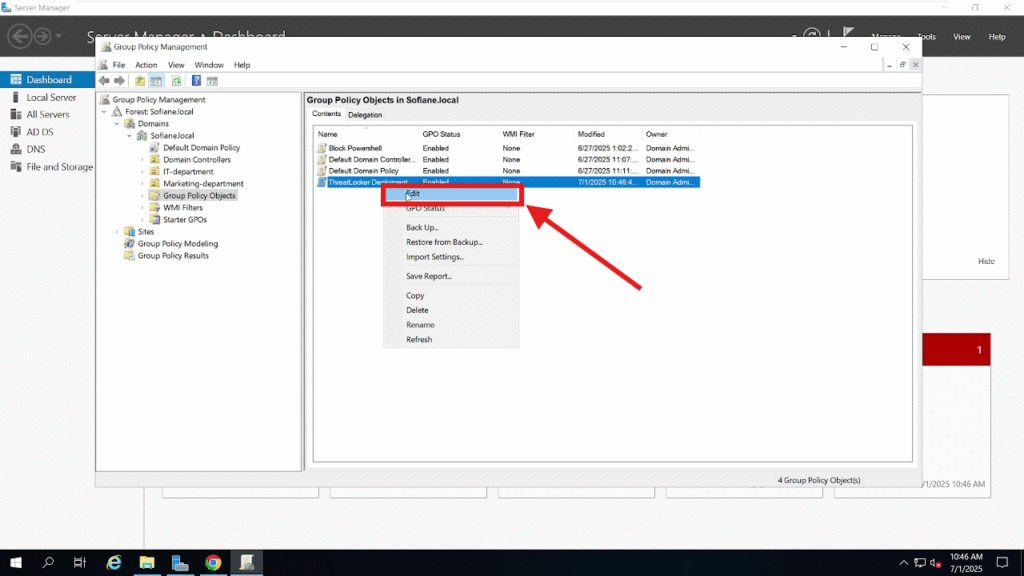
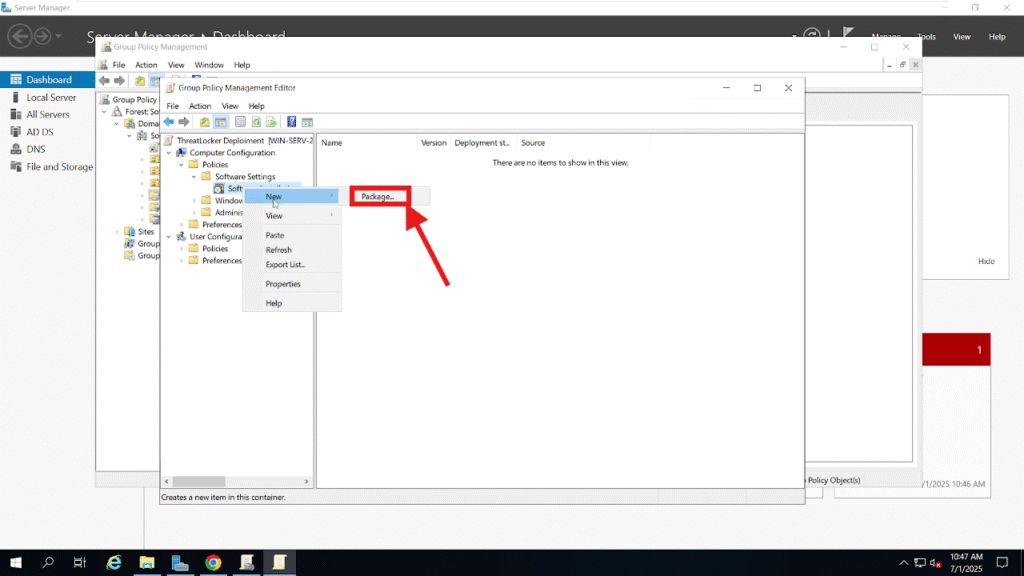
In the Group Policy Management Editor, navigate to: Computer Configuration > Policies > Software Settings > Software Installation, Right-click in the right pane and choose New > Package:
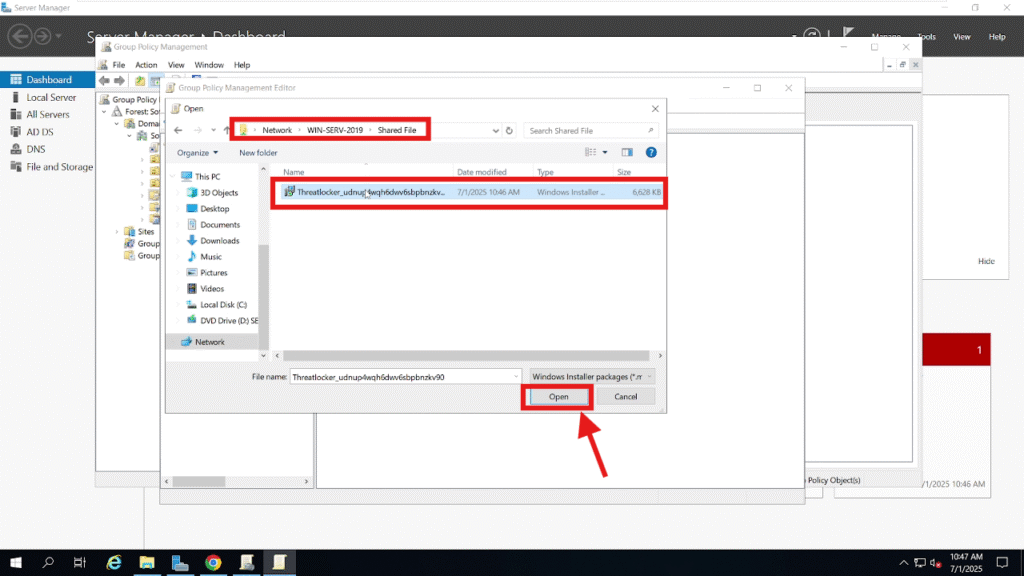
When prompted, browse to the shared folder and select the MSI installer using the UNC path (e.g., \\WIN-SERV-2019\Shared file\).
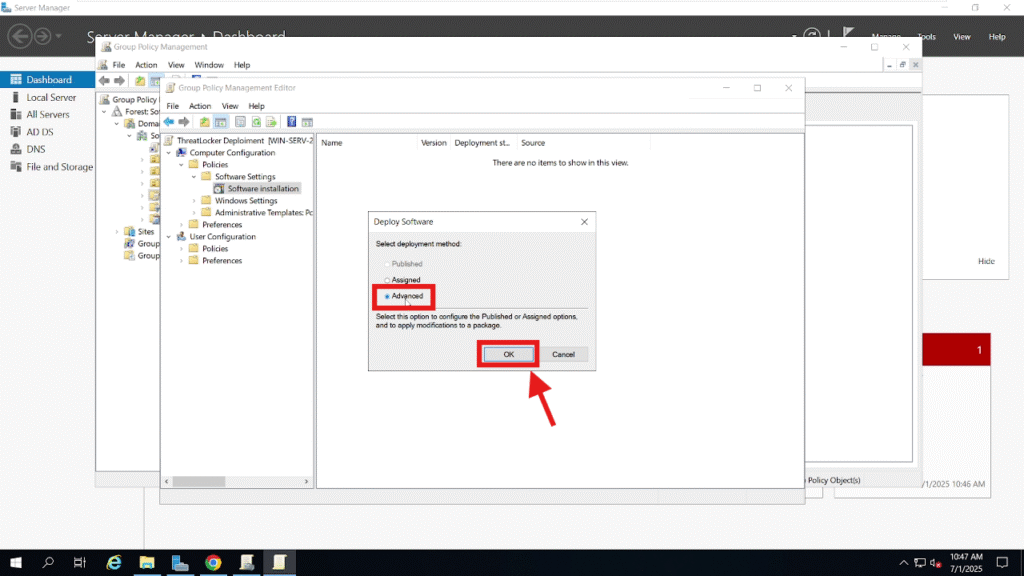
Choose the Assigned deployment method and click OK.
After this step, you should see that the ThreatLocker Deployment installer has been added to the policy.
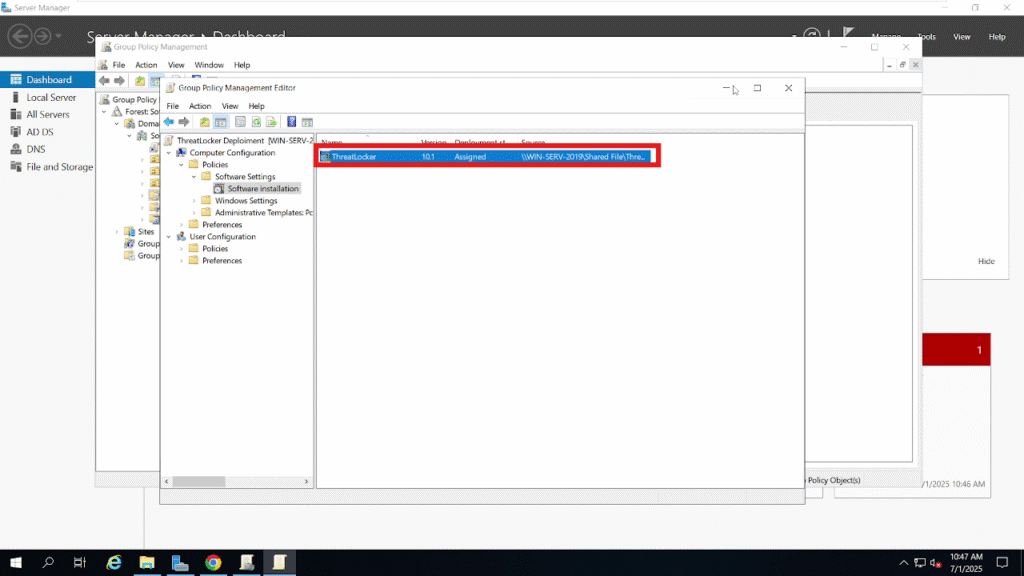
Step 5: Apply and Refresh Group Policy
Next, go to the domain or the Organizational Unit (OU) where you want to apply the policy. Right-click and select “Link an Existing GPO…”.
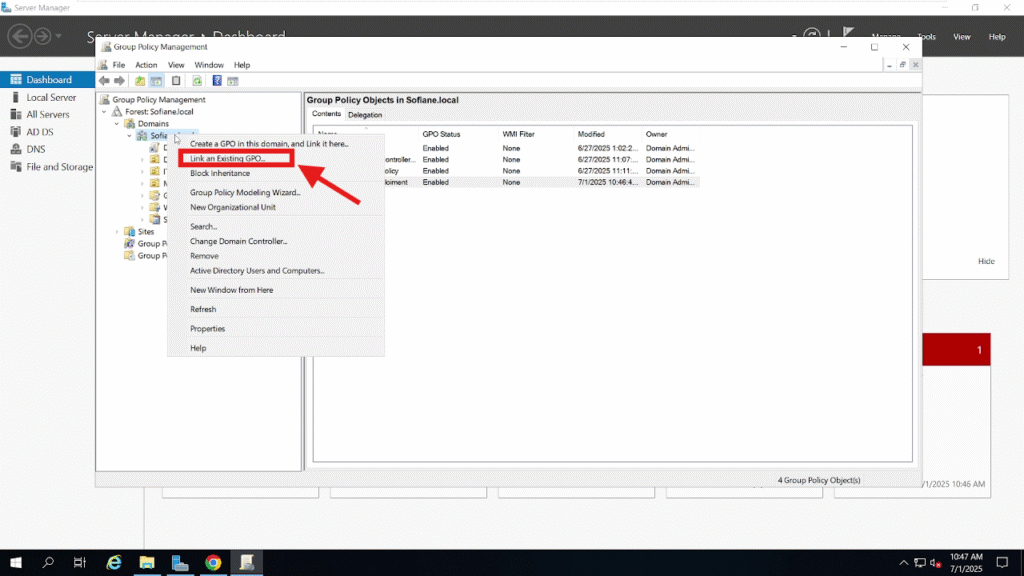
From the list, select the previously created GPO named ThreatLocker Deployment, then click OK.
Step 6: Force the Group Policy Update
To immediately apply the policy on client machines, open Command Prompt and execute the following command: gpupdate /force
Then, reboot the machines to trigger the automatic installation of the ThreatLocker agent.
Conclusion
Deploying the ThreatLocker agent through Group Policy (GPO) is a reliable and scalable method to ensure consistent installation across all domain-joined machines. By leveraging GPO, administrators can automate the deployment process, reduce manual effort, and maintain better control over the software environment. Once properly configured and linked to the appropriate organizational units, the installation occurs seamlessly on user devices during startup or refresh cycles, ensuring that all systems are protected without disrupting end users.
This method is especially useful in enterprise environments where centralized management and security compliance are critical.
