
How to enable application control in ThreatLocker?
This document outlines the step-by-step process of how to enable Application Control in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
Application Control in ThreatLocker allows you to define exactly which applications can or cannot run on your endpoints, enabling Zero Trust enforcement and blocking unauthorized software (e.g., PowerShell, scripting tools, etc.).
This guide explains how to locate, activate, and deploy existing Application Control policies from the ThreatLocker Portal.
Implementation
Step 1: Access the Application Control Policies
Log in to the ThreatLocker Portal and Go to Module > Application Control > Policies
Here, you will see a list of all existing policies.You can filter them by Group, Application, or Status (Active/Inactive).
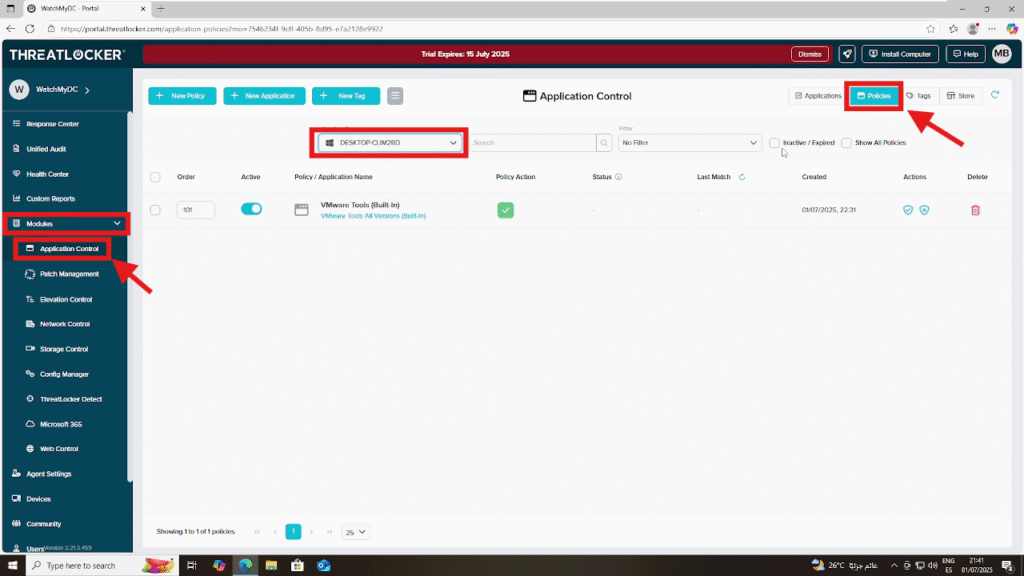
Step 2: Enable a Disabled Policy
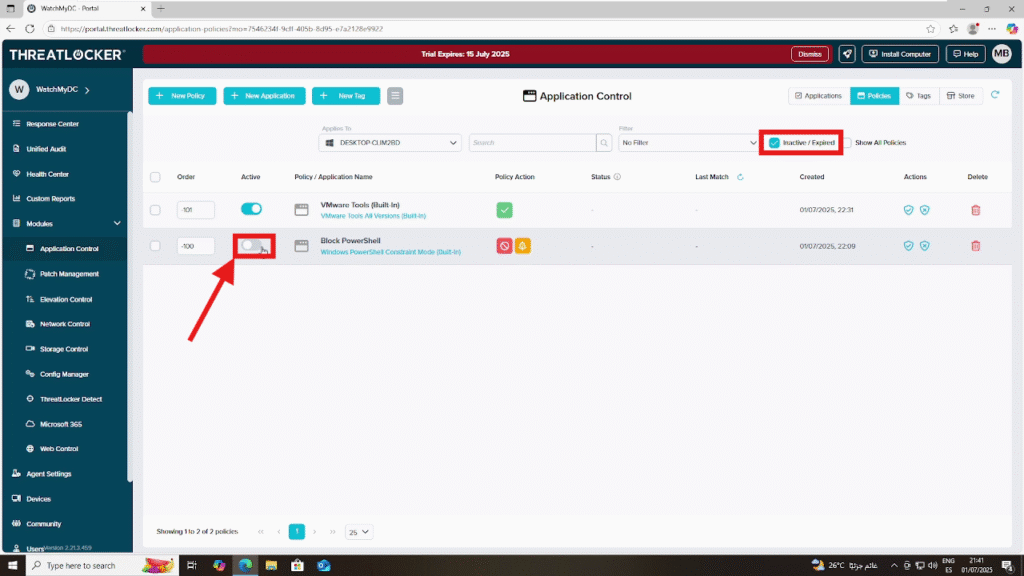
To view inactive or expired policies, click the filter icon and select “Inactive / Expired”.
Find the policy you want to enable (e.g., a policy that blocks PowerShell), then click the “Activate” button to enable it.
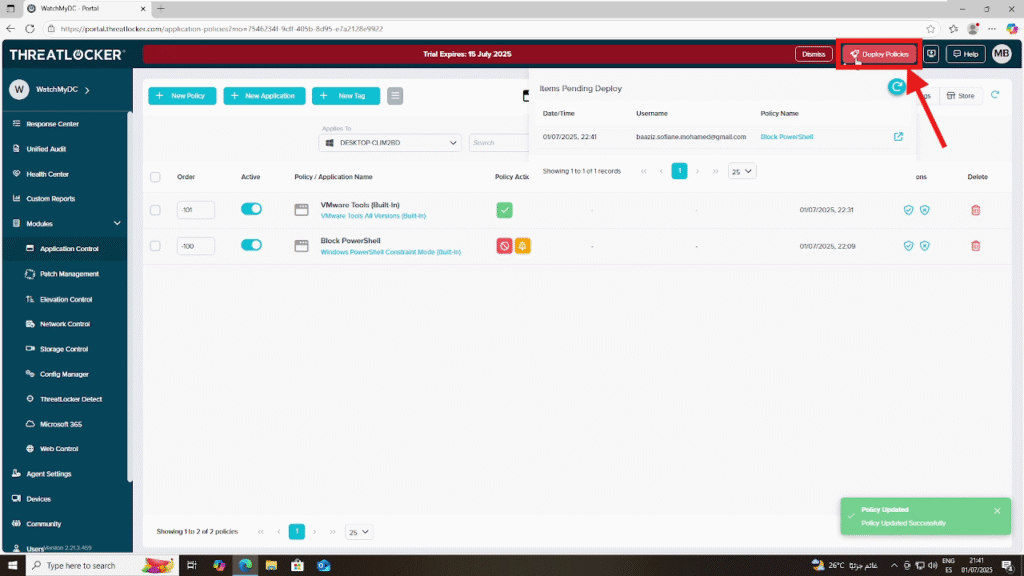
Step 3: Deploy the Policy
After activation, apply the policy immediately by clicking “Deploy”, ensuring real-time enforcement.
Conclusion
Enabling Application Control in ThreatLocker is a crucial step in implementing a Zero Trust security model.By activating and deploying predefined policies, you ensure that only approved applications can run on your endpoints, reducing the risk of malware, scripts, or unauthorized tools being executed.
With just a few clicks in the ThreatLocker Portal, your organization gains stronger control, visibility, and protection across its entire environment.
