
How to enable USB control in ThreatLocker?
This document outlines the step-by-step process of how to enable USB control in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 05 – Storage Control.
Introduction
USB Control in ThreatLocker is part of the Storage Control module, which allows administrators to manage and restrict the use of removable storage devices such as USB flash drives, external hard drives, and other media.
What is USB control?
USB Control helps secure your environment by limiting how and when storage devices can be accessed on endpoints. It enables policies such as read-only access, full blocking, or allowing only encrypted devices.
Objective
The goal is to prevent unauthorized data transfer and reduce the risk of malware introduced through external devices.
In this guide, we’ll walk through the step-by-step process to enable USB control by creating a policy using the ThreatLocker Storage Control module.
Implementation
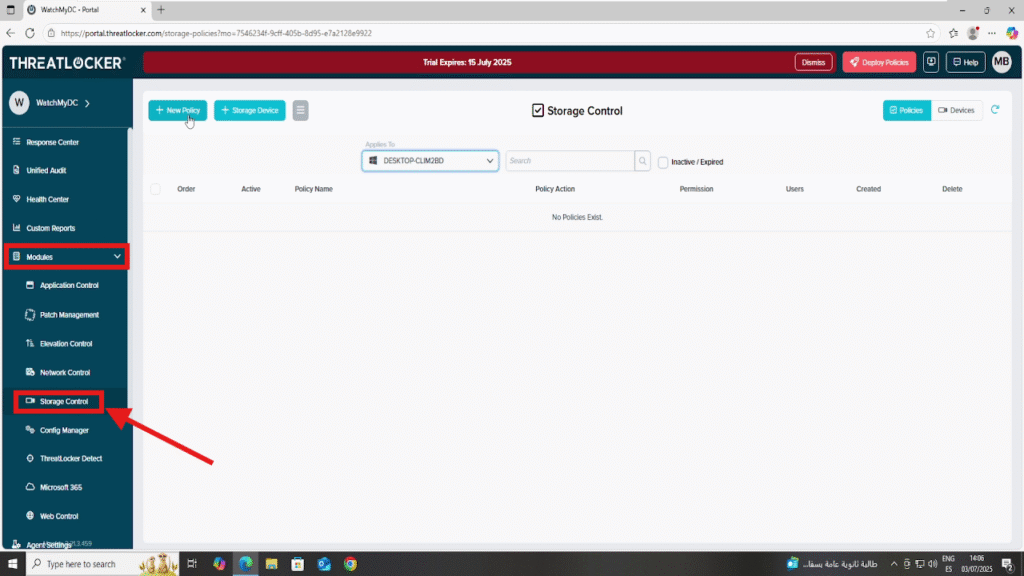
Step 1: Access the Storage Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Storage Control.
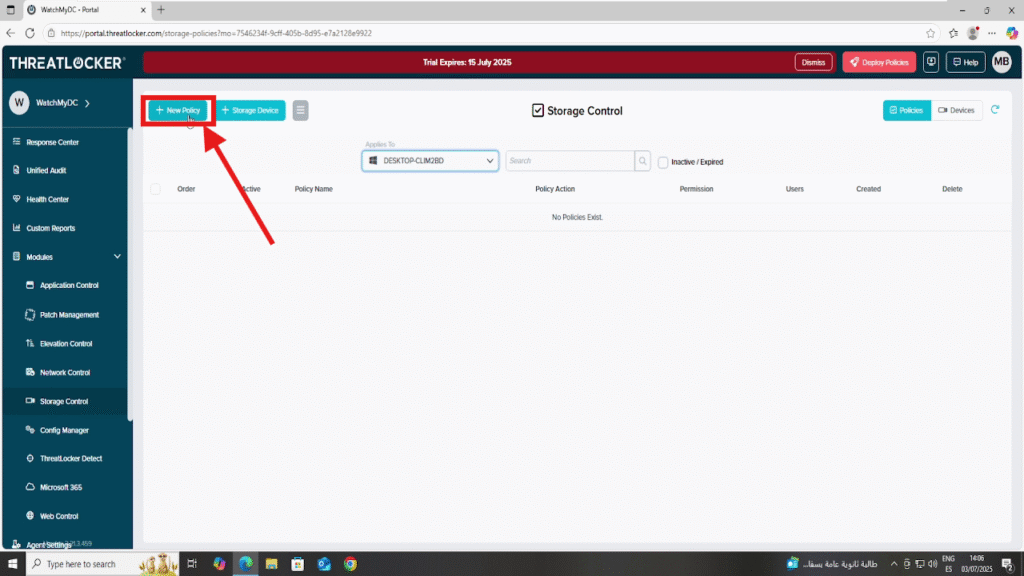
Step 2: Create and Configure the USB Control Policy
1. Click on Create Policy to begin.
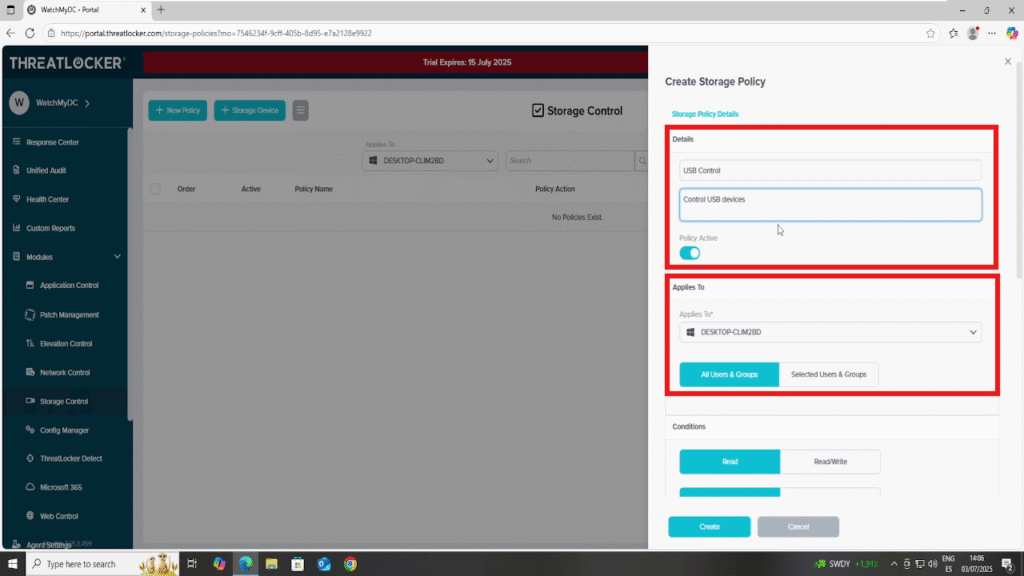
2. In the Policy Details section:
- Name: e.g., USB Control Policy
Description: e.g., Restrict USB storage access to selected devices
3. In the Apply To section:
- Select the target computer or device group where this policy should apply.
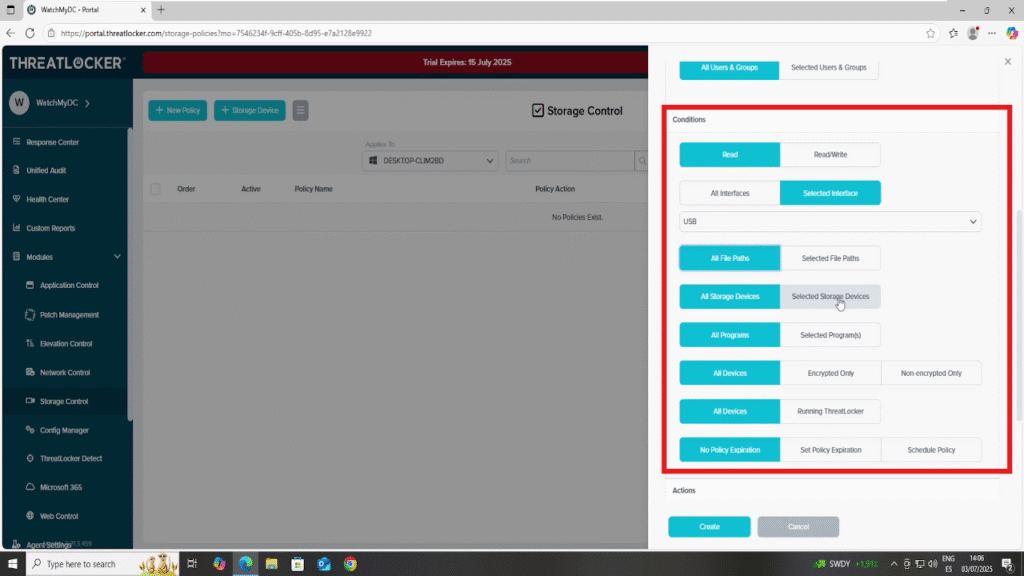
4. In the Conditions section, configure the USB access parameters:
- Access Type:
- Choose either Read or Read/Write depending on the level of access you want to allow.
- Interface Type:
- Select USB to apply the policy specifically to USB ports.
- Program Filter:
- Choose All programs, or specify particular programs the policy will apply to.
- Device Filter:
- Choose among:
- All Devices
- Encrypted Devices Only
- Non-Encrypted Devices Only
- Choose among:
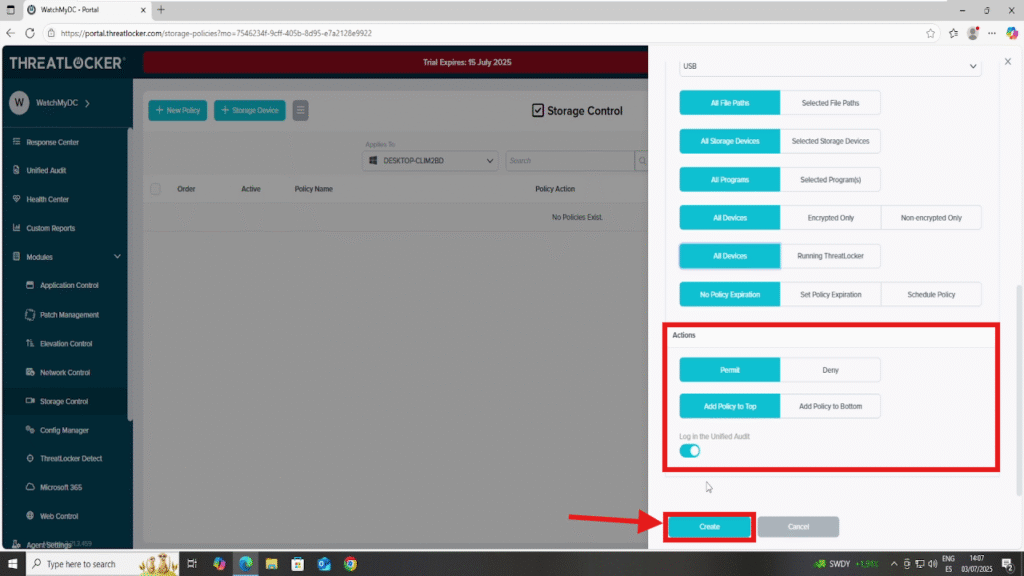
5. In the Action section:
- Choose whether to Permit or Deny USB access based on the defined conditions.
- Ensure Unified Audit is enabled to track USB activity related to this policy.
- Add the policy by clicking the Add Policy button, available at the top or bottom of the page.
- The button position determines the priority of the policy higher policies take precedence.
6. Once everything is configured:
- Click Create to save the policy.
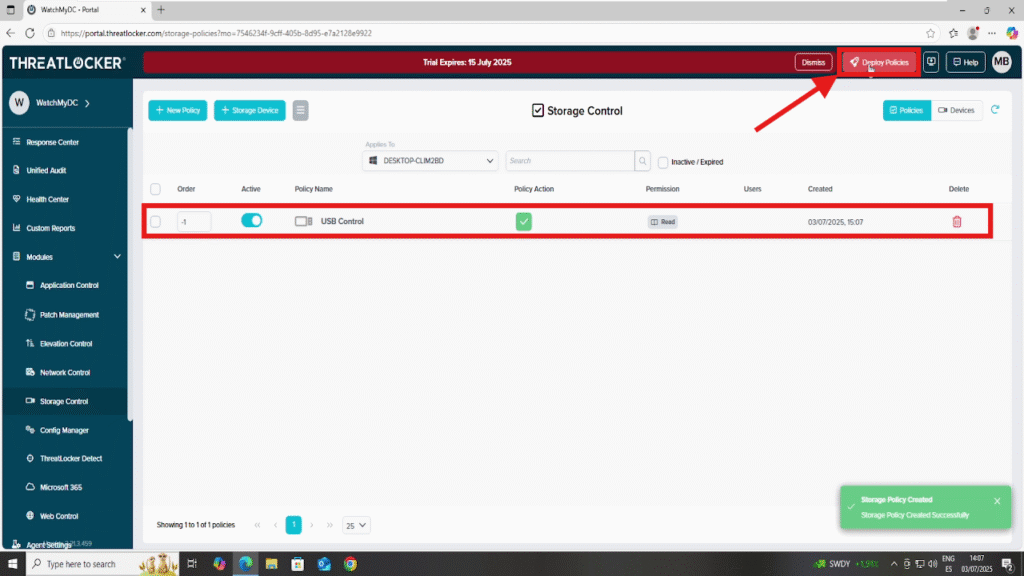
- Then click Deploy from the policy list to apply it to the selected endpoints.
Conclusion
Enabling USB control in ThreatLocker enhances your organization’s data protection by managing which devices can connect to your endpoints. With flexible options such as permitting or denying access by interface type, encryption status, or program-specific rules, administrators can tailor USB usage to their exact security requirements.
Combined with Unified Audit, this ensures complete visibility into external device usage, which is a crucial component of a Zero Trust strategy.
For best results, regularly review USB policies and logs to adjust to evolving operational needs or emerging threats.
