
How to enforce encryption on removable storage in threatLocker?
This document outlines the step-by-step process of how to enforce encryption on removable storage in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 05 – Storage Control.
Introduction
Allowing only encrypted USB devices is a powerful way to reduce the risk of data theft, loss, or unauthorized transfer.
With ThreatLocker Storage Control, you can block all USB devices by default and then create a policy that permits only encrypted storage.This guide shows how to enforce encryption by combining a deny-all USB policy with a secondary policy that allows only encrypted devices.
Implementation
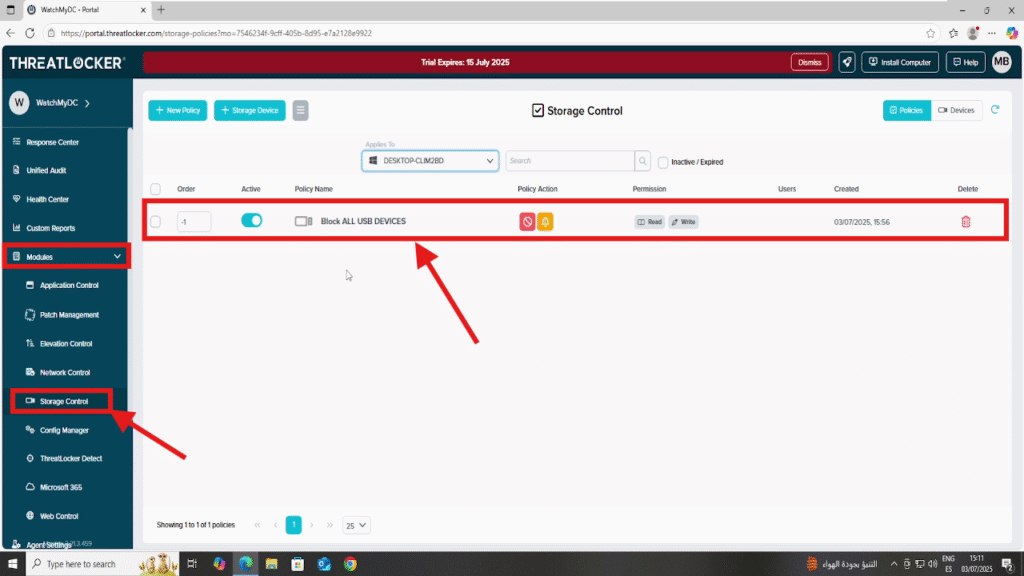
Step 1: Ensure a Deny-All USB Policy Exists
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Storage Control
- Ensure that a policy such as “Block All USB Devices” is active and correctly applied to the target machines.
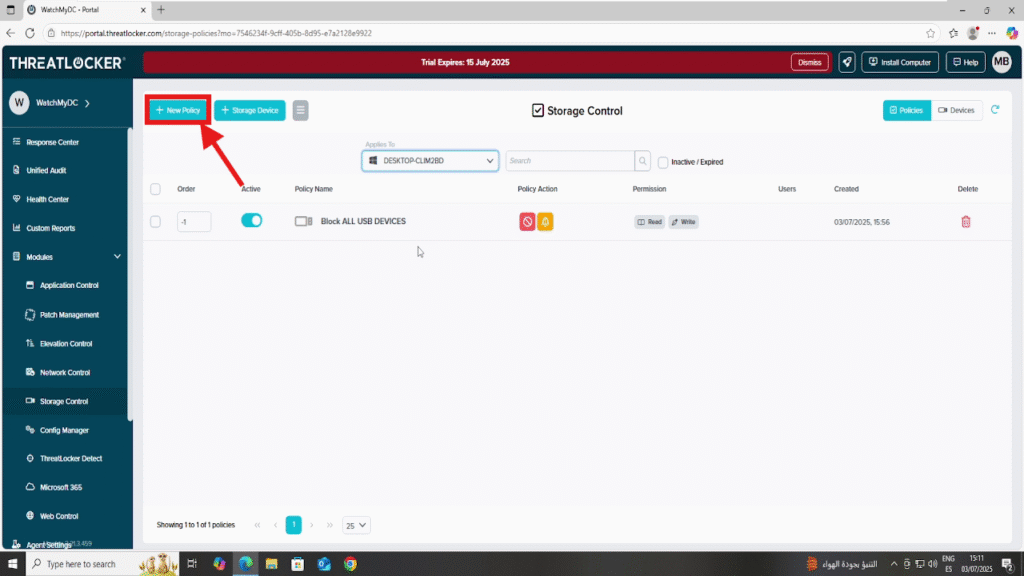
Step 2: Create a Policy to Allow Encrypted USB Devices
- Click Create Policy in the Storage Control module
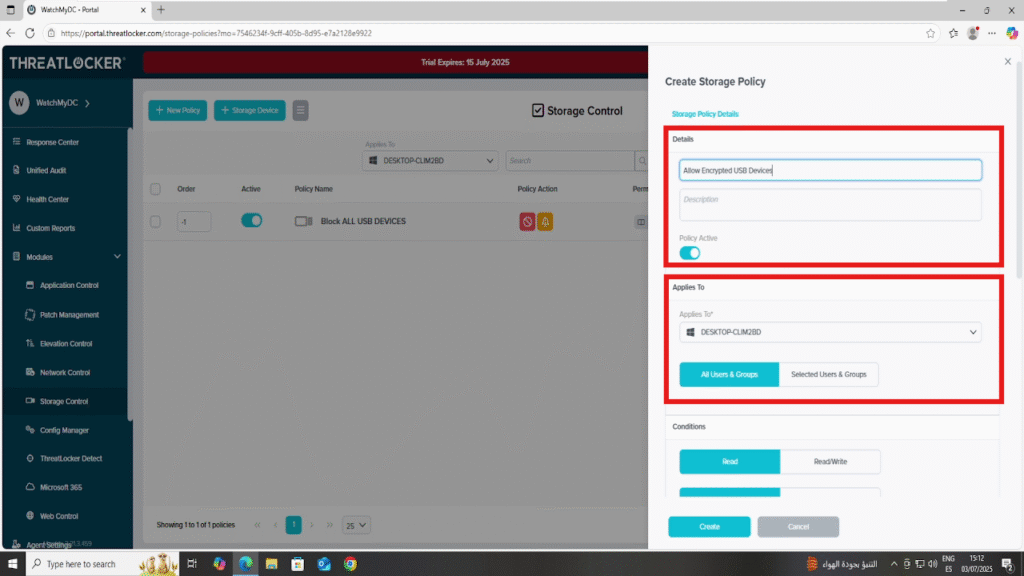
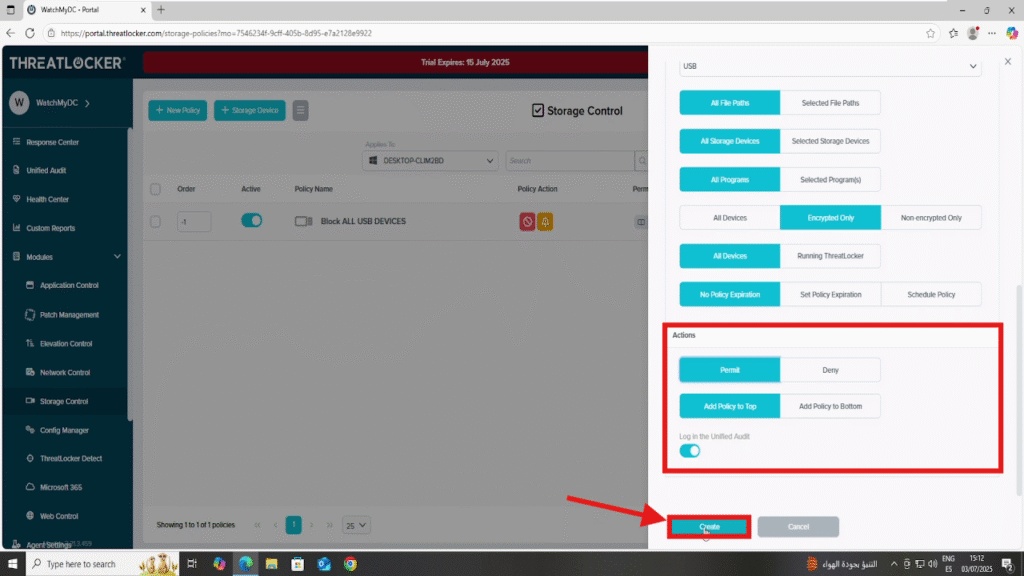
2. Fill in the Policy Form:
- In the Details section:
- Name: Allow Encrypted USB Devices
- Description: Permit access only to encrypted removable storage
- In the Applied To section:
Select the target computer or computer group
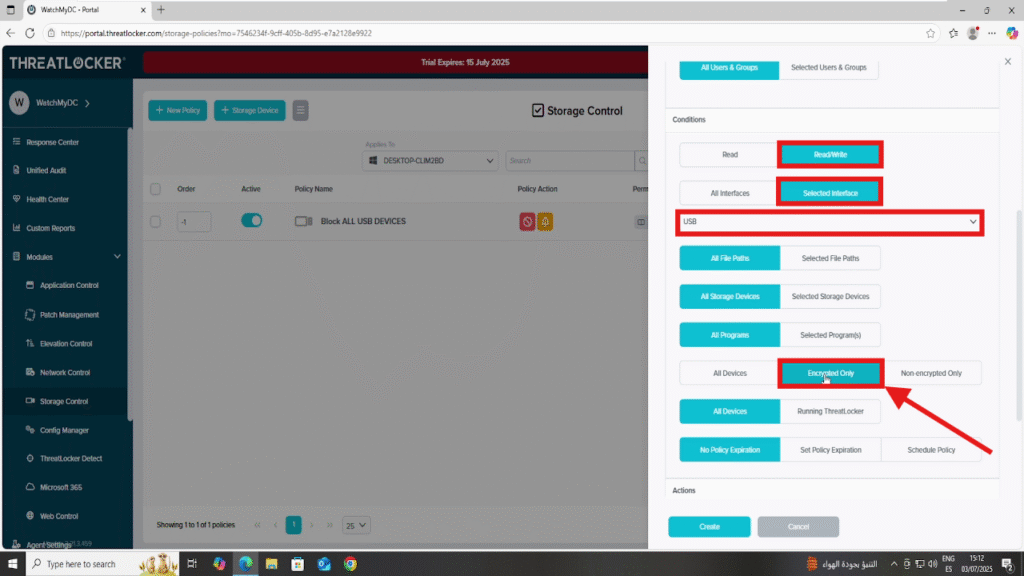
- In the Condition section:
- Access Type: Read/Write
- Interface Type: Select Selected Interfaces
- Choose USB
- Select Encrypted Only
- In the Action section:
- Set the Action to “Permit”
- Add the policy to the top of the policy list to ensure it takes priority over the “Block All USB Devices” policy
Once all fields are configured, click Create to save the policy
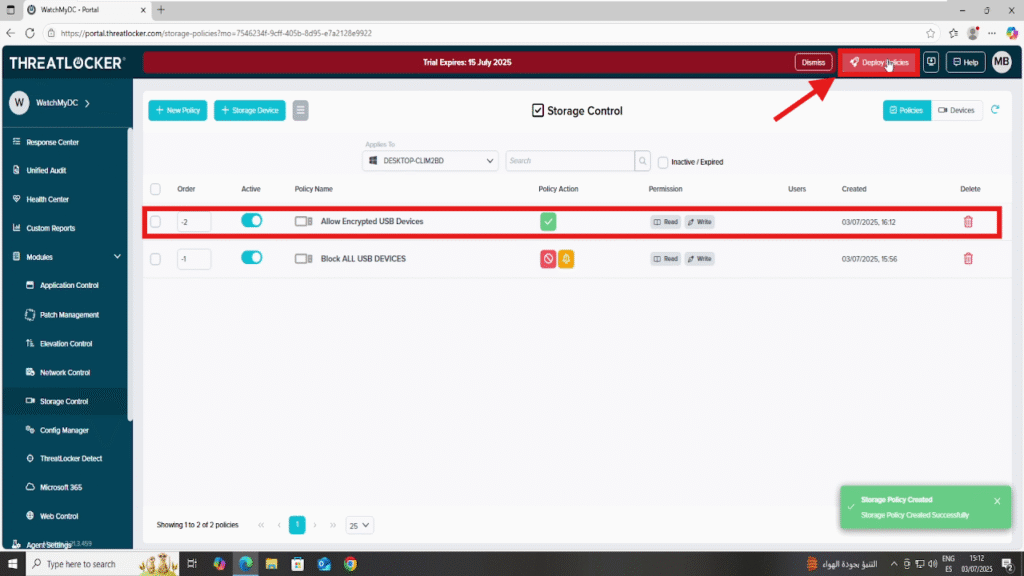
Step 3: Apply the Policy to enforce encryption on removable storage
Go back to the Policies list
- Click Deploy to activate the policy on the selected machines
Conclusion
Enforcing encryption on removable storage ensures that only trusted, secure USB devices are allowed to operate in your environment.
By combining a default deny USB policy with a permit policy for encrypted devices, you can:
- Prevent unauthorized or unsecured USB usage
- Reduce the risk of data leakage and loss
- Enforce regulatory compliance and internal security standards
- Align with Zero Trust principles by allowing only explicitly authorized, encrypted media
With ThreatLocker’s granular Storage Control, you can implement strong, automated protection without disrupting productivity.
