
How to generate usage reports in ThreatLocker?
This document outlines the step-by-step process of how to generate usage reports in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 10 – Monitoring, Logs and Reports.
Introduction
ThreatLocker provides a Custom Reports feature that allows you to create tailored reports based on audit logs, computer details, or both. These reports help in monitoring activity, tracking overrides, and reviewing system usage across your organization.
Implementation
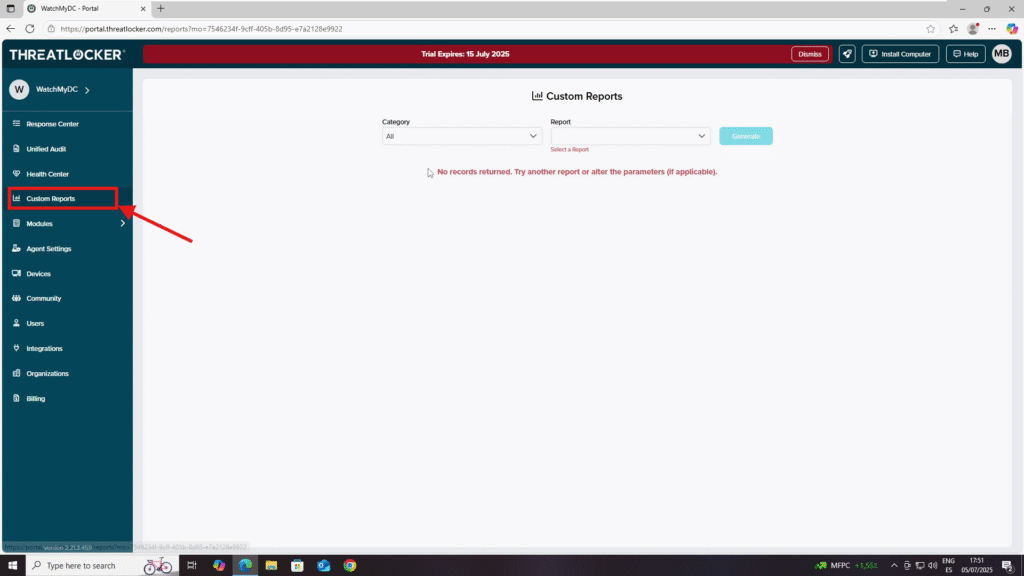
Step 1: Access the Custom Reports Section
- Log in to the ThreatLocker Portal.
- Navigate to Custom Reports from the left-hand menu.
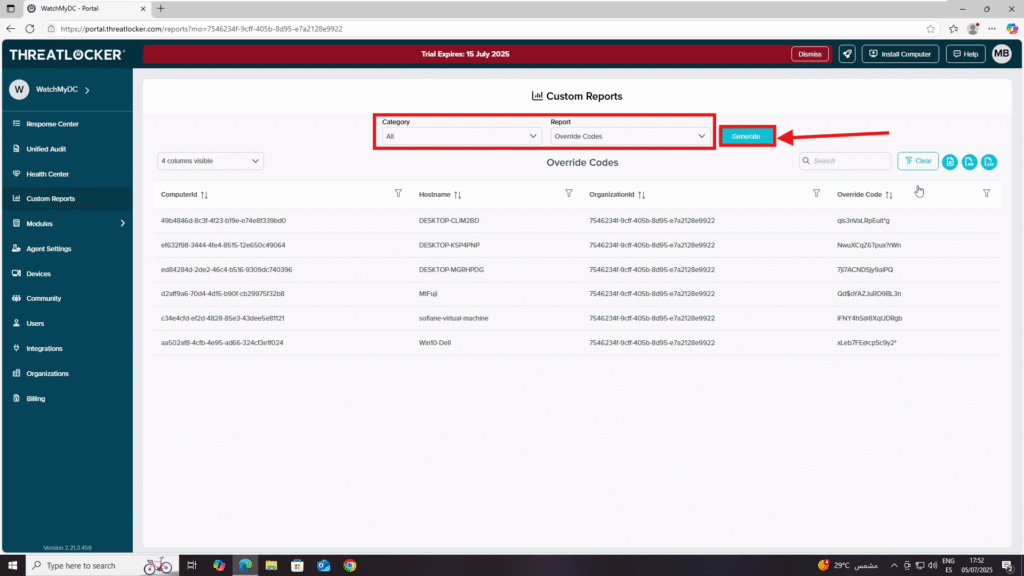
Step 2: Generating a Report
- In the Custom Reports section, choose a Report Category:
- Audit – For logs of actions and events.
- Computers – For device-specific information
- All – For combined data.
- In the Report field, select the type of report you want. Examples include:
- Override Code
- Override Use (Including Child Organizations)
- If you choose an Audit report, set a Start Date and End Date to define your search period.
- Once all parameters are set, click Generate.
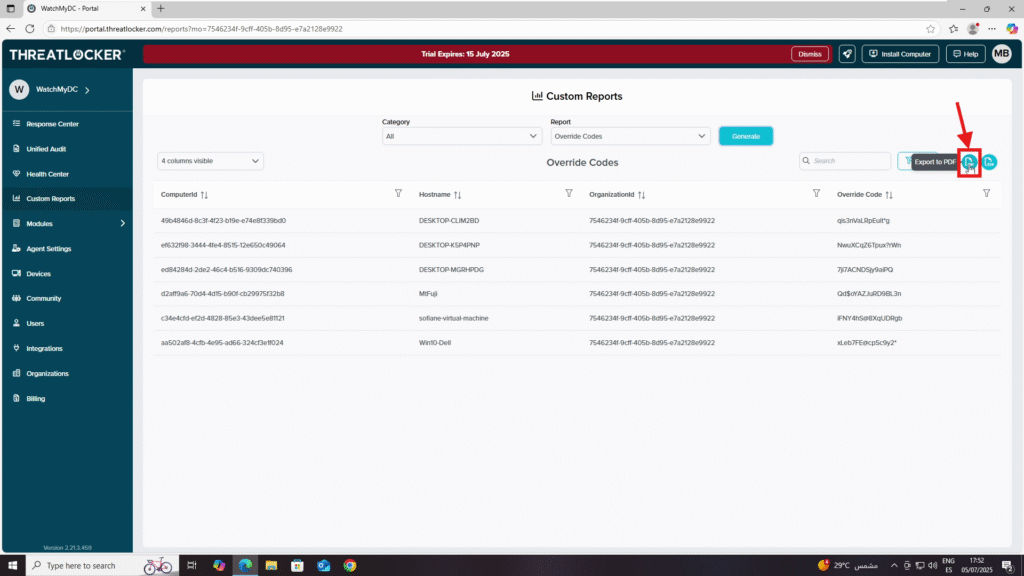
Step 3: Exporting the Report
- After the results appear, you can export the report in PDF, CSV, or Excel format.
- For example, to export the report in PDF format:
- Next, Click the PDF export button to download the file.
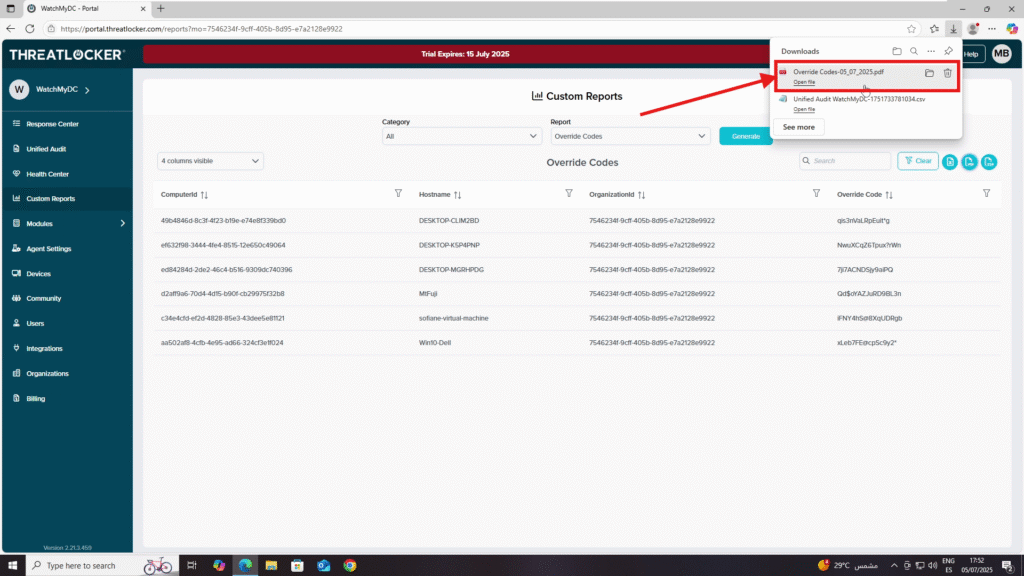
The PDF will automatically download to your device.
Conclusion
Exporting logs from the Unified Audit in ThreatLocker is quick and straightforward. This feature ensures you can easily share, archive, or analyze security events outside the ThreatLocker platform.
