
How to allow specific USB devices in ThreatLocker?
This document outlines the step-by-step process of how to allow specific USB devices in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 05 – Storage Control.
Introduction
USB storage devices present a significant risk to endpoint security, from data exfiltration to malware infections.
ThreatLocker’s Storage Control module provides granular control over external storage access, allowing administrators to block USB drives entirely or selectively. In this guide, we’ll walk through the step-by-step process of blocking all USB storage devices using a custom policy.
Implementation
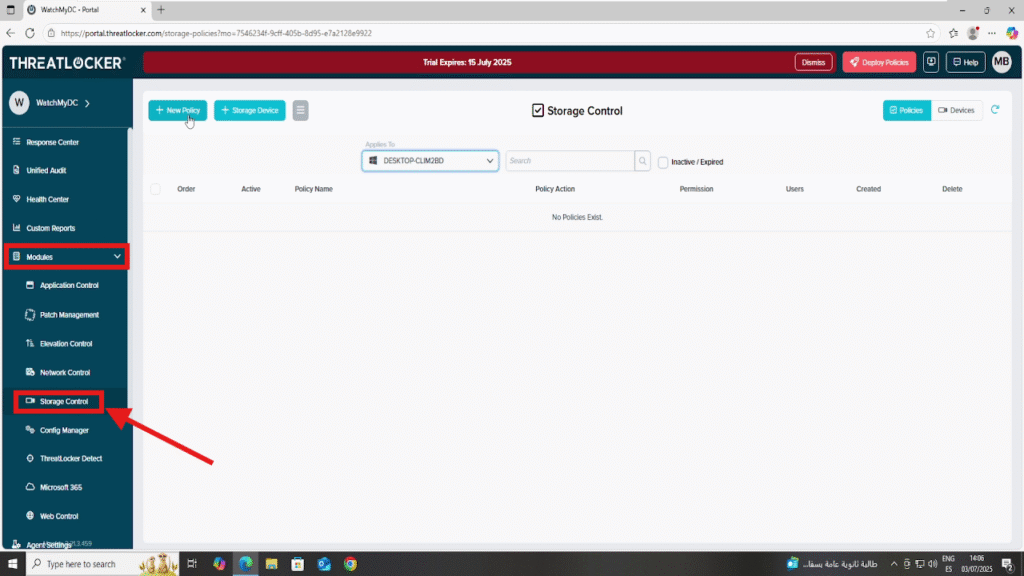
Step 1: Access the Storage Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Storage Control.
If no deny policy exists, you will need to create one.
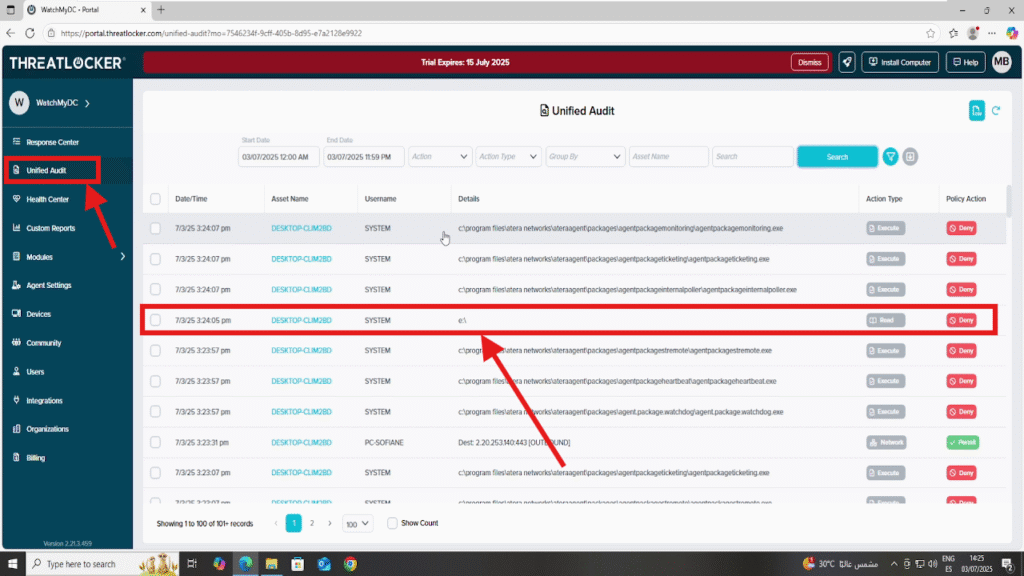
Step 2: Plug In the USB Device & Use Unified Audit
- Insert the USB device into a target computer
- Go to Unified Audit in the ThreatLocker Portal
- Filter the events by Storage to locate the USB access attempt
- Click on the event to view the full details
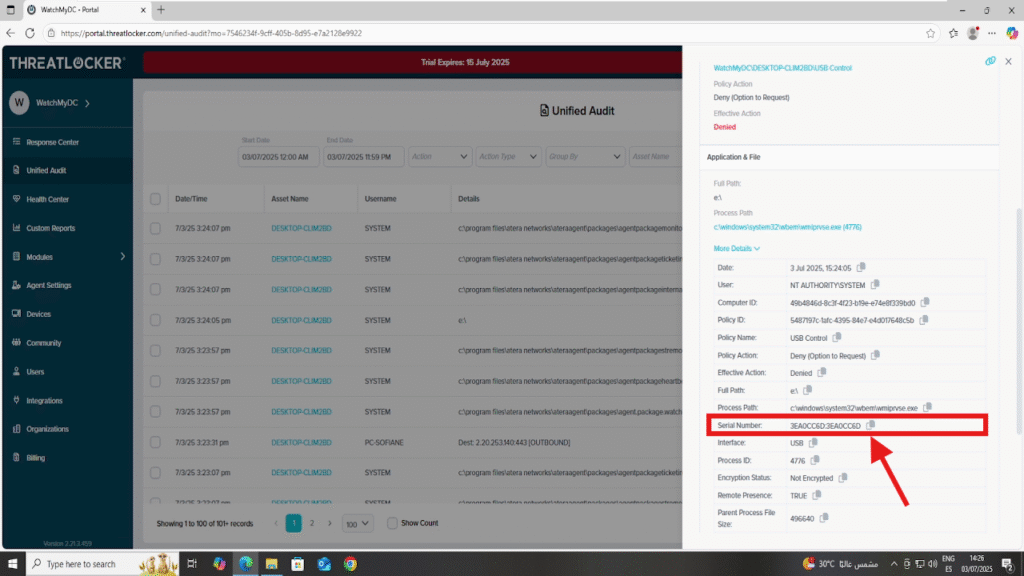
5. Locate and copy the USB serial number from the device details
Step 3: Add the USB Device in Storage Control
- Return to Storage Control
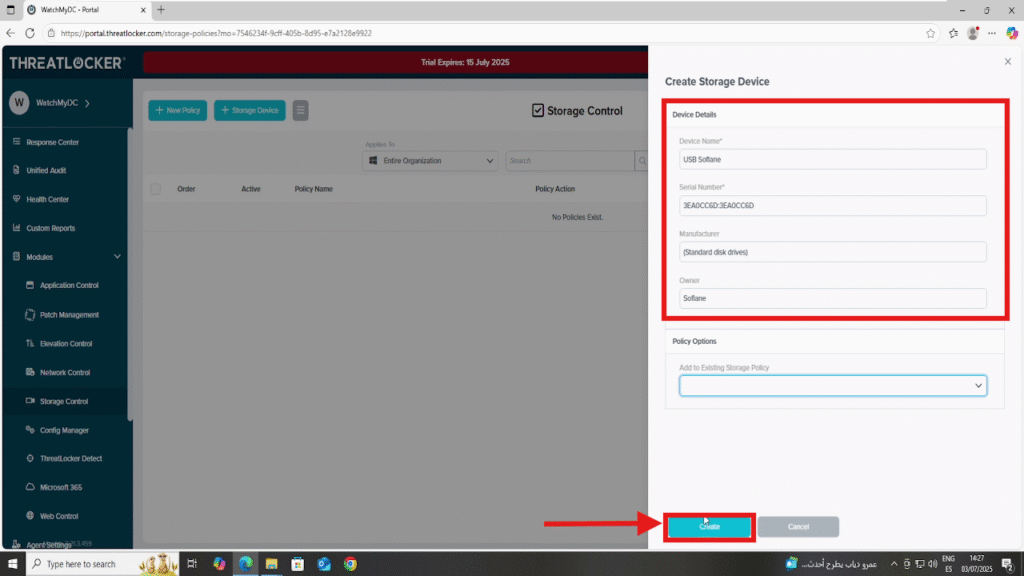
- Click + Storage Device to add a new USB device
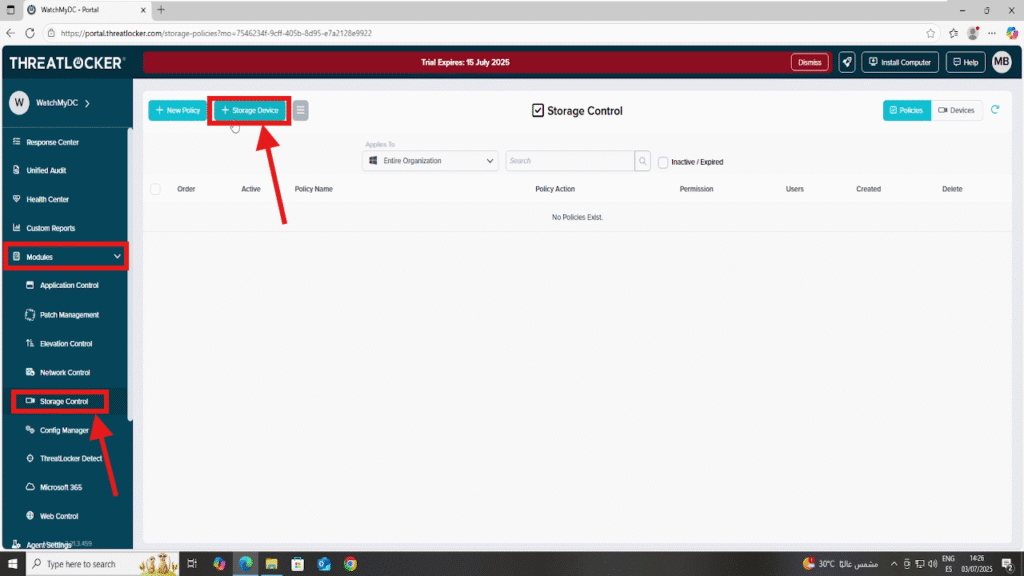
3. Fill in the following fields:
- Device Name: e.g., USB Sofiane
- Serial Number: paste the serial number from the Unified Audit
- Manufacturer (optional)
- Owner (optional)
4. Create
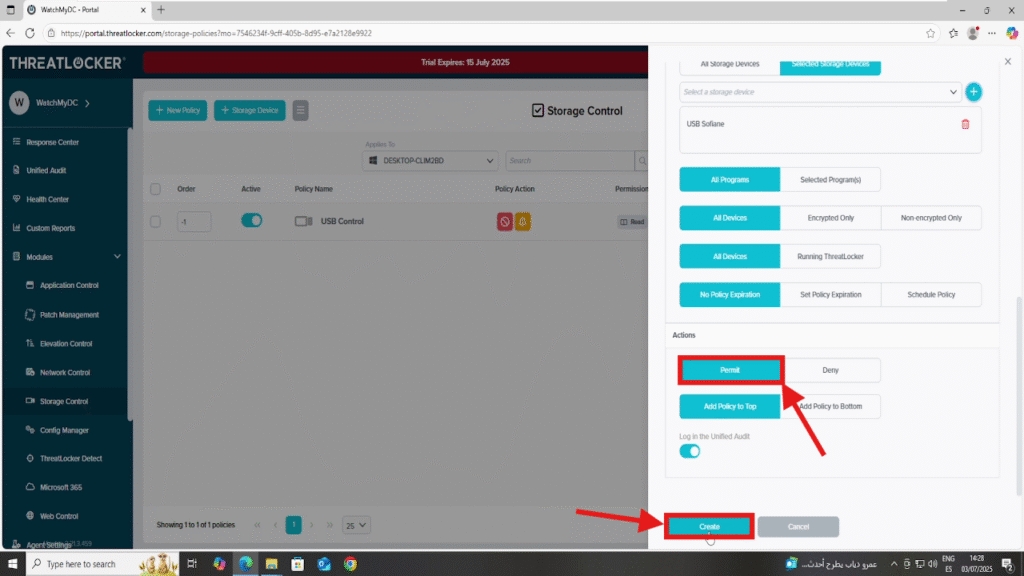
Step 4: Create a Policy to allow specific USB devices in ThreatLocker
1. Click Create Policy
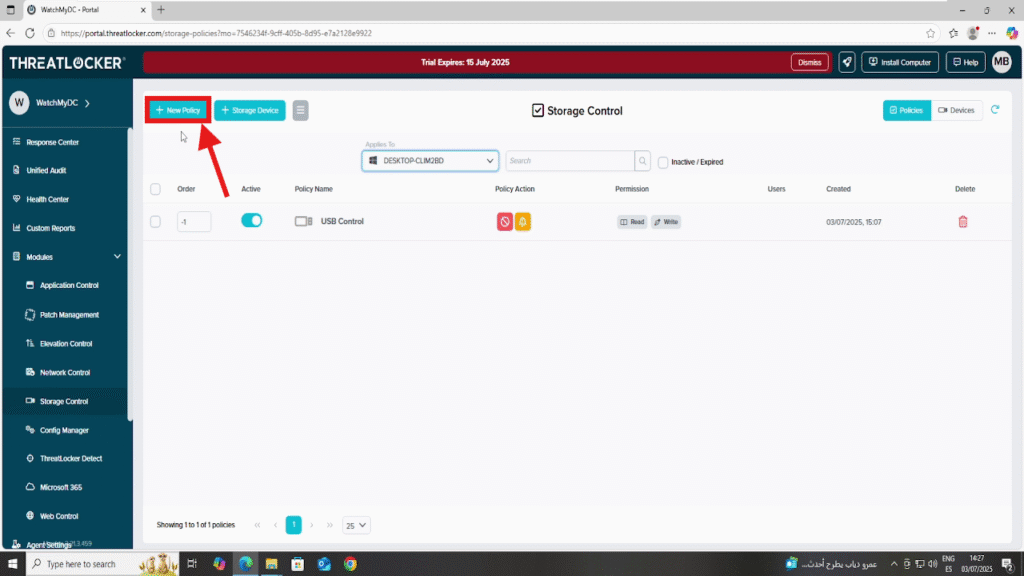
2. Fill in the policy form:
- Name: e.g., Allow USB Sofiane
- Description: Permit USB Sofiane
- Applied To: Choose the computer or group where this policy will be applied
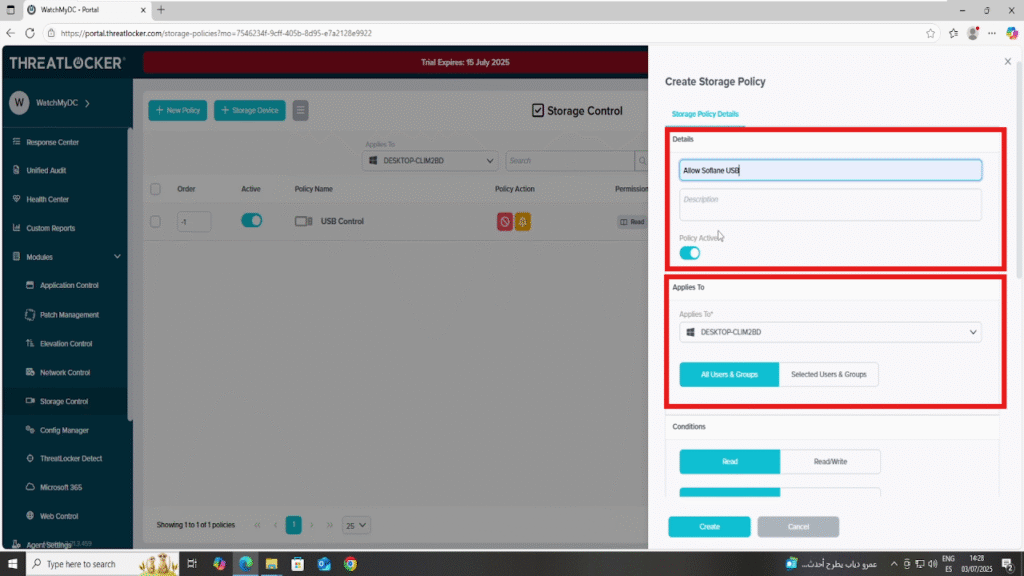
- Condition section :
- Select Selected Devices
- Choose the target USB device from the list (e.g., USB Sofiane)
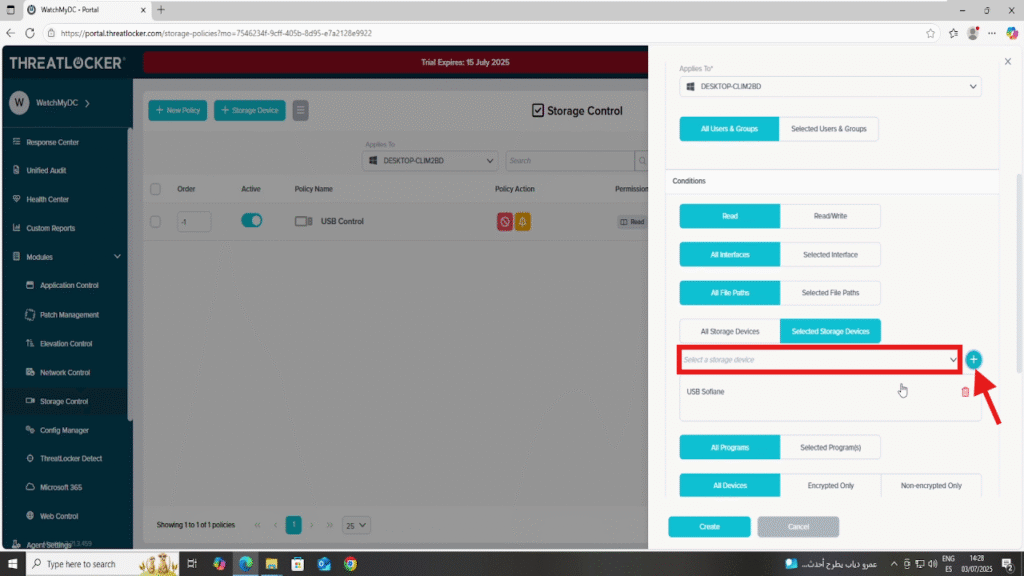
- Action section:
- Set Action to Permit
- Click Create to save the policy
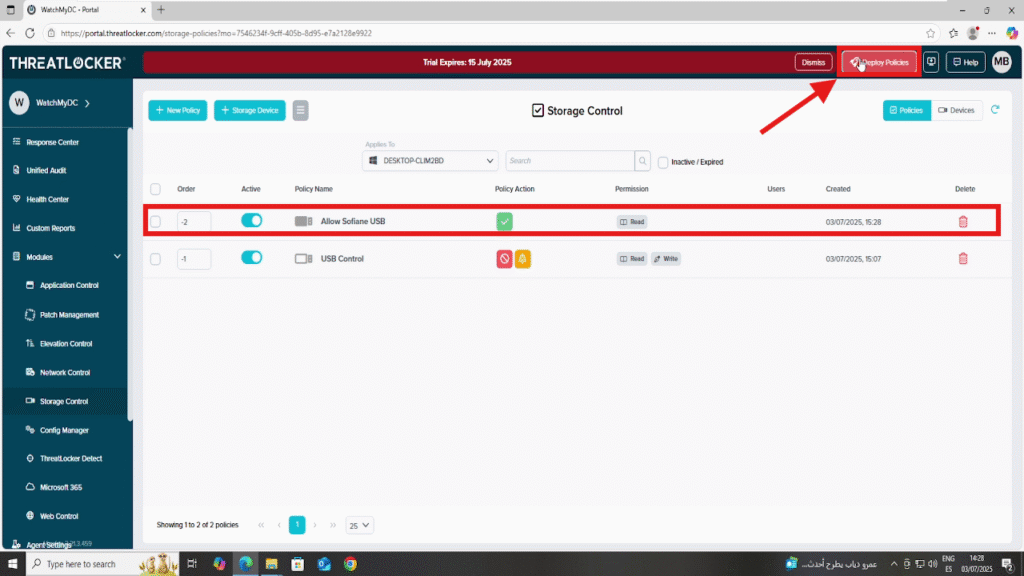
- Once the policy is created, return to the Policies list and click Deploy to allow specific USB devices in ThreatLocker.
Conclusion
Allowing a specific USB device through ThreatLocker’s Storage Control gives you precise control over external storage while maintaining strong security.
By first enforcing a default deny policy and then using the Unified Audit to authorize a specific device, you ensure that only trusted USBs can access your environment.
This approach:
- Prevents unauthorized USB usage
- Reduces the risk of data exfiltration and malware
- Aligns with Zero Trust best practices
With ThreatLocker, you can confidently balance security and operational needs allowing what is necessary and blocking everything else.
