
How to install the ThreatLocker agent on Linux?
This document outlines the step-by-step process for installing the ThreatLocker agent on a Linux machine. This installation is essential to enable centralized management and policy enforcement on endpoints.
This article is a part of our ThreatLocker How-to Guides series, Chapter 01 – Installation & Deployment.
Implementation
There are two main methods for installing the ThreatLocker agent, depending on your environment and deployment size:
- Manual Installation – Suitable for individual machines or small-scale environments.
- Automated Installation (via script or remote management tools), Recommended for large-scale or remote deployments.
In this document, we will focus on the Manual Installation method.
Manual Installation of ThreatLocker Linux Agent
This method is used for individual or small-scale installations, typically done directly on each device.
Step 1: Go to the “Devices” Section:
After logging into the ThreatLocker web portal, navigate to the “Devices” tab in the left-hand menu. This section displays all endpoints where the ThreatLocker agent is installed or can be deployed.
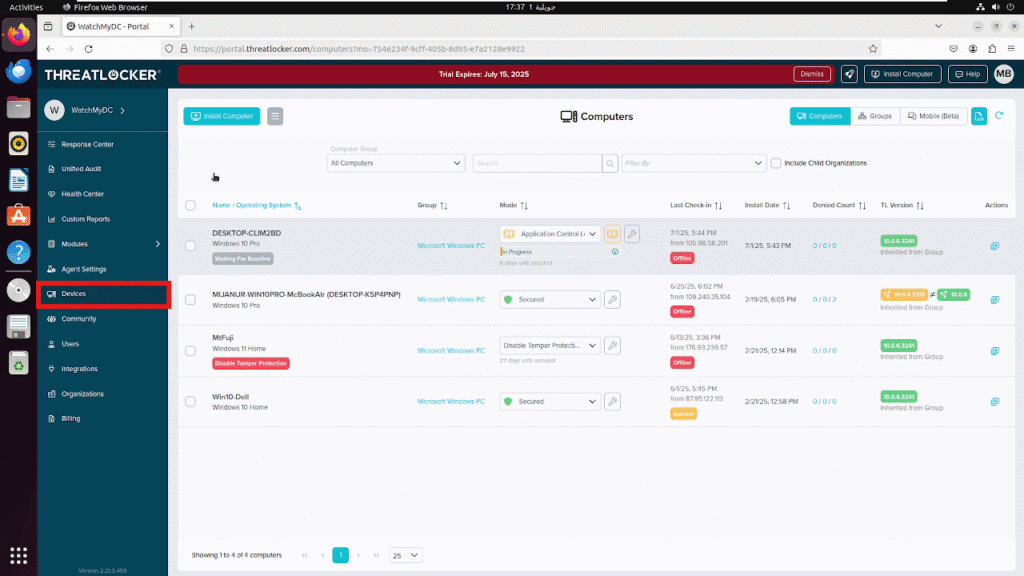
Step 2: Download the Agent Installer:
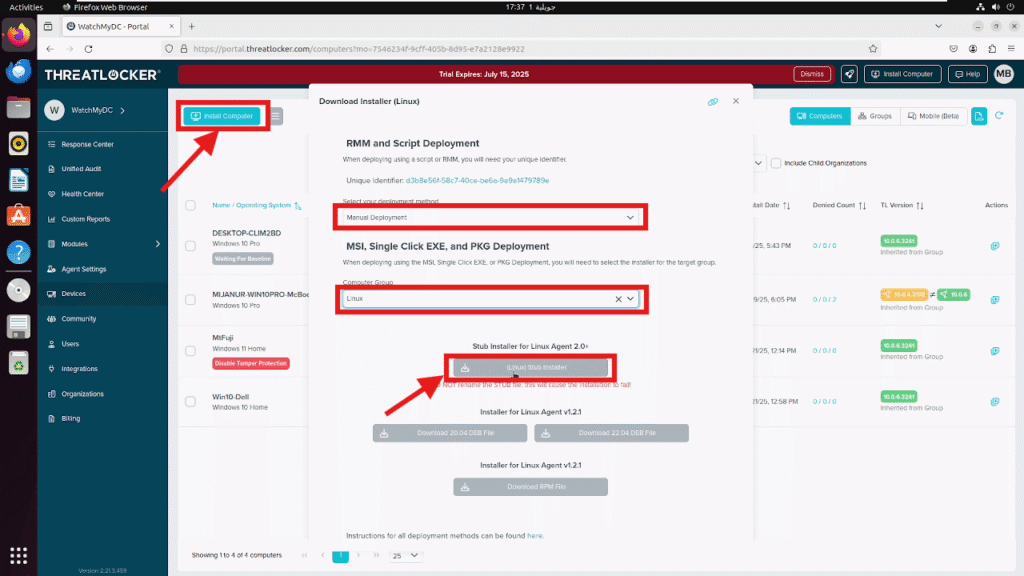
Click the “Install Computer” button at the top of the screen, this will open the Agent Installer window, where you can:
- Choose the target Computer Group (e.g., Linux Workstations, Servers, etc.)
- Select the installation method :
- Stub
- .deb (for Debian-based syste ms)
- .rpm (for Red Hat-based systems)
Note: At the top of the window, your Unique Identifier will be displayed. This is required if you choose the script-based method.
Do not rename the installer file (.deb, .rpm, or stub) — it is uniquely tied to your configuration, and renaming it will cause the installation to fail.
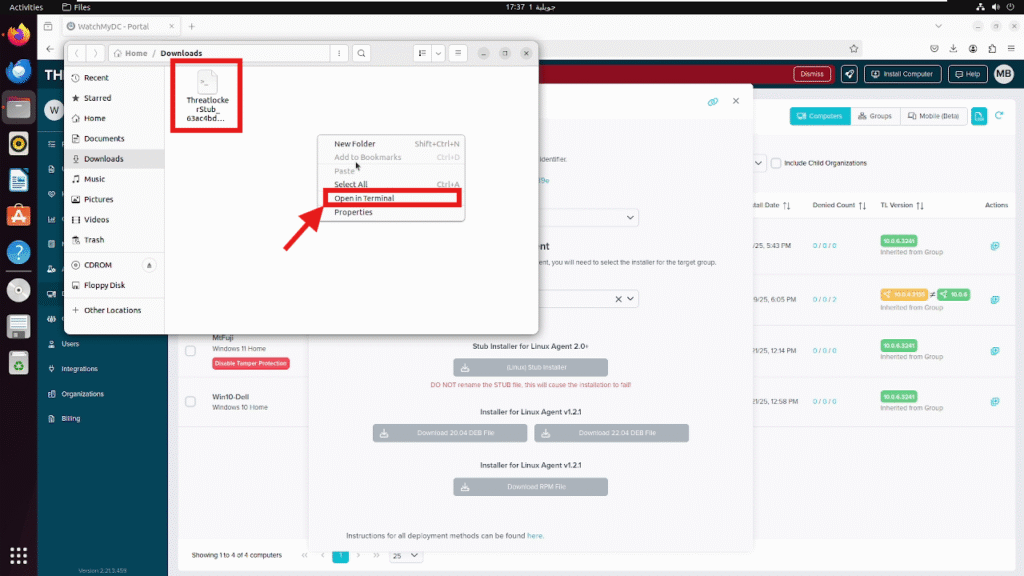
Step 3: Execute the Installer on the Linux Machine
Once the installer has been downloaded (e.g., in the Downloads folder), do the following:
- Right-click on the file
Select “Open in Terminal” from the context menu
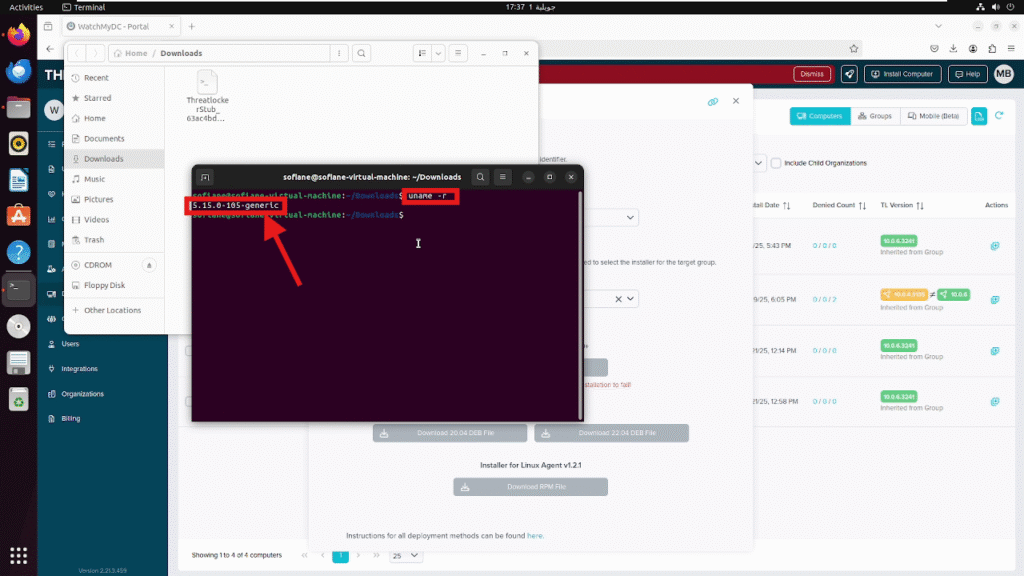
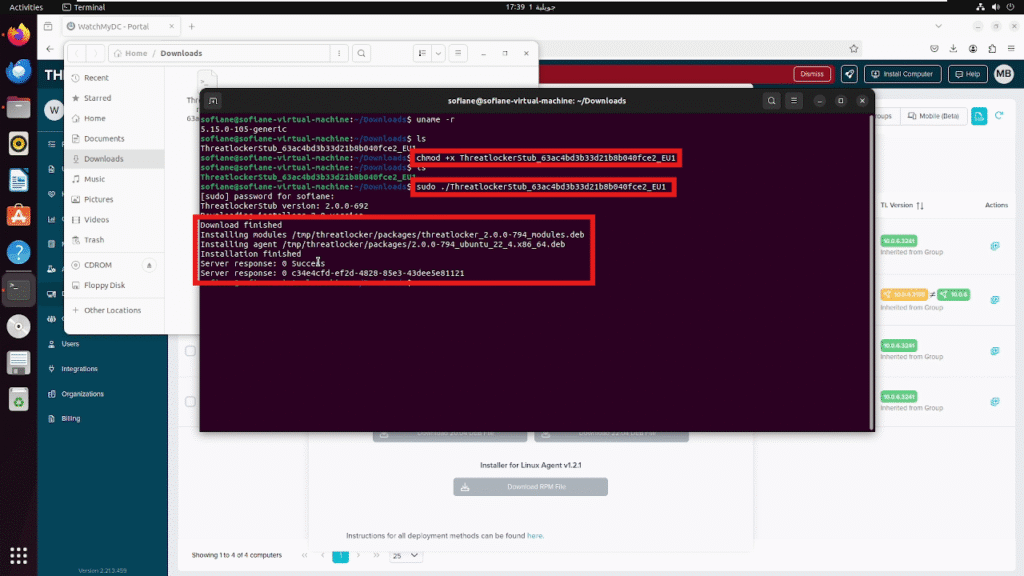
Check the Linux Kernel Version Before running the installer, verify that the Linux kernel version is compatible.
- Run this command in the terminal: uname -r
- You should see: 5.15.0-105-generic
This version is required for the ThreatLocker agent to install correctly.
- Make the Installer Executable and run the Installer with Administrative Privileges:
- Make the installer executable with the following command:
- chmod +x ThreatLockerStub…
- Then, run the installer as administrator:
- sudo ./ThreatLockerStub…
- Make the installer executable with the following command:
Once the installation is complete, you should see confirmation messages such as:
- Installation finished
- Server response: 0 Success
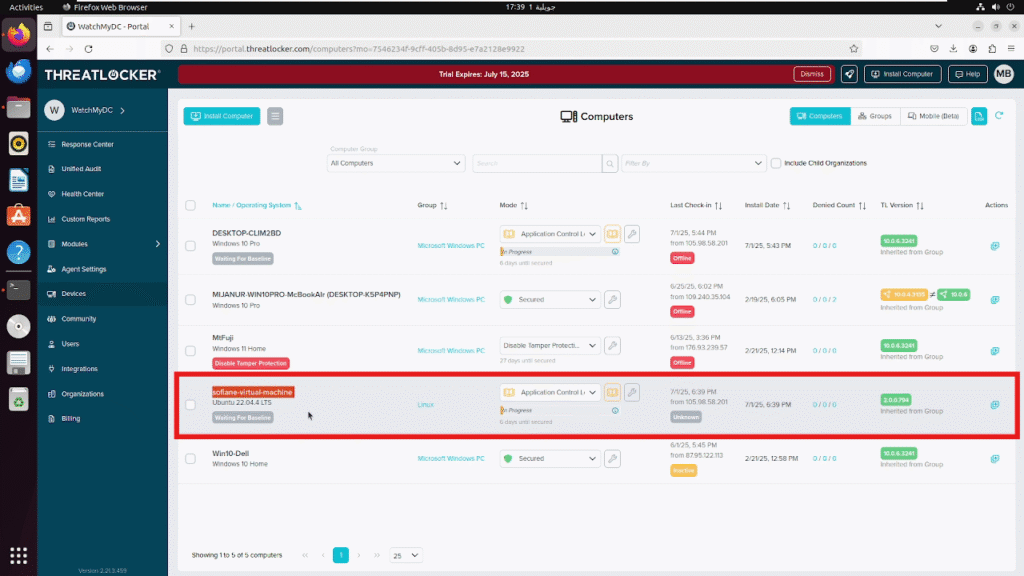
Step 5: Verify Installation in the ThreatLocker Portal.
After completing the process to install of ThreatLocker linux agent is complete:
- Return to the ThreatLocker Portal > Devices.
- Find the device by its hostname (e.g., sofiane-virtual-machine)
You should see that the device is active, with all details displayed (such as operating system, status, activity, version, etc.)
Step 5: Verify Installation in the ThreatLocker Portal.
After the installation is complete:
- Return to the ThreatLocker Portal > Devices
- Find the device by its hostname (e.g., DESKTOP-CLIM2BD).
- You should see that the device is active with all details displayed (such as operating system, status, activity, version, etc.).
This confirms that the ThreatLocker Agent has been successfully installed and is communicating with the portal.
Conclusion
The installation of the ThreatLocker Linux agent is a straightforward process that ensures your endpoints are enrolled in the security ecosystem effectively.
By following the steps outlined in this guide, you have successfully:
- Accessed the ThreatLocker Portal.
- Selected the appropriate installer for your system.
- Deployed the agent on the target machine.
- Verified that the device is active and connected.
With the agent now installed, the device will begin baseline monitoring, allowing ThreatLocker to observe normal behavior before enforcement is applied.
