
How to install ThreatLocker on a remote workstation?
This document outlines the step-by-step process of how to install the ThreatLocker on a remote workstation.
This article is a part of our ThreatLocker How-to Guides series, Chapter 01 – Installation & Deployment.
Introduction
What is the ThreatLocker Agent?
Keeping the ThreatLocker agent up to date ensures that your endpoints benefit from the latest features, security improvements, and performance enhancements. This guide outlines the steps to update the agent on a selected device from the ThreatLocker Portal.
Why install remotely via RDP?
Remote Desktop Protocol (RDP) allows administrators to manage and install software on endpoints without being physically present.This method is especially useful for remote teams, branch offices, or during large-scale deployments.
Objective
This guide explains how to install the ThreatLocker agent remotely using RDP and ensure the remote device is properly enrolled in the ThreatLocker Portal.
Implementation
Updating the agent is done directly through the ThreatLocker Portal and requires just a few clicks. The process is simple and does not require reinstallation or manual intervention on the device itself.
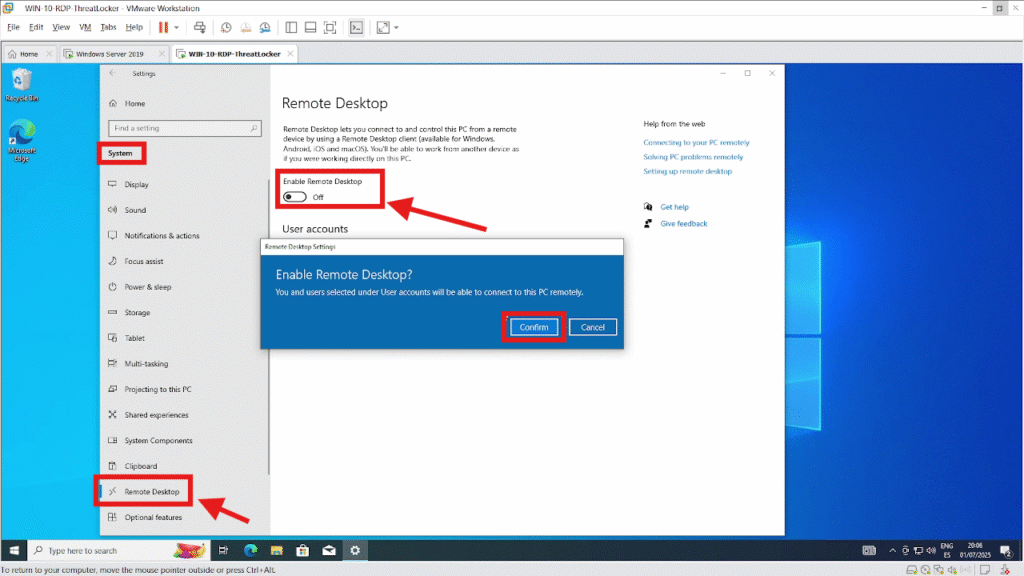
Step 1: Enable RDP on the Target Machine
On the target workstation:
- Go to Settings > System > Remote Desktop
Toggle Remote Desktop to “On”
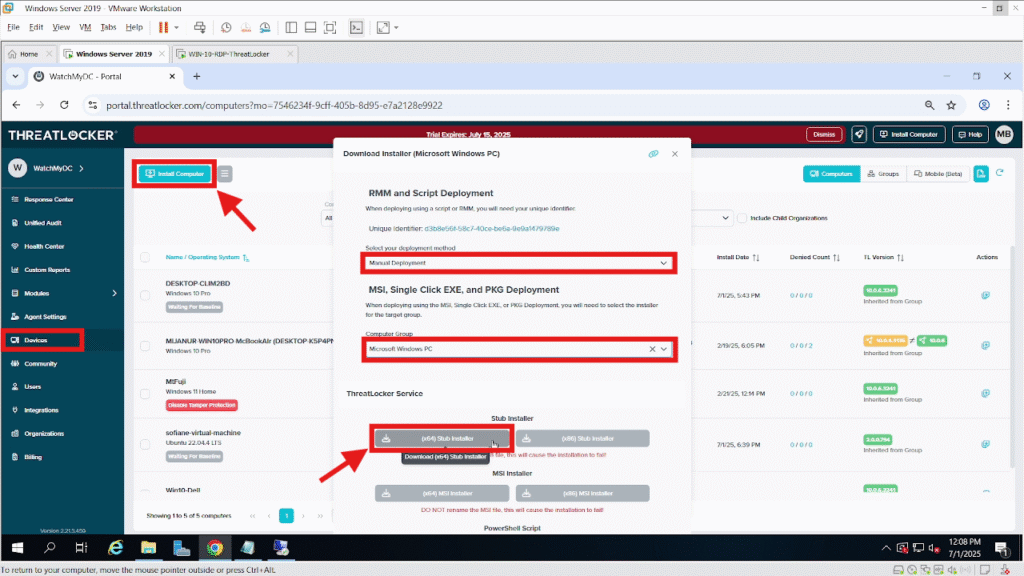
Step 2: Download the ThreatLocker Installer Stub
From your local machine, log in to the ThreatLocker Portal, then navigate to the Devices tab. Click on “Install Computer” to open the installation window. Choose the appropriate Computer Group based on the device type you’re installing the agent on. Finally, select the correct stub installer according to your system architecture either x64 or x86.
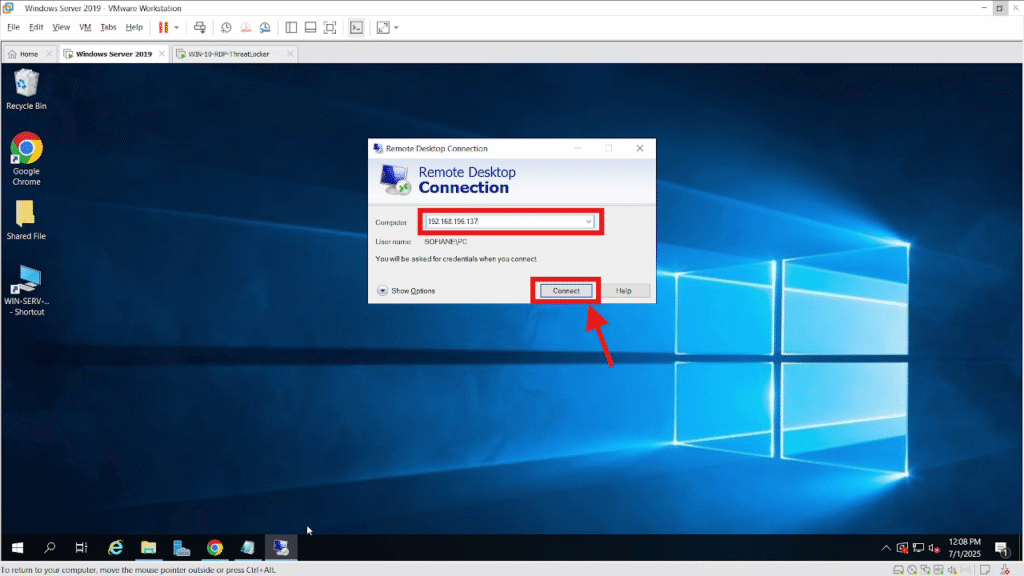
Step 3: Connect via RDP and Transfer the Installer
Connect to the remote workstation using RDP, entering the device’s IP address or hostname.
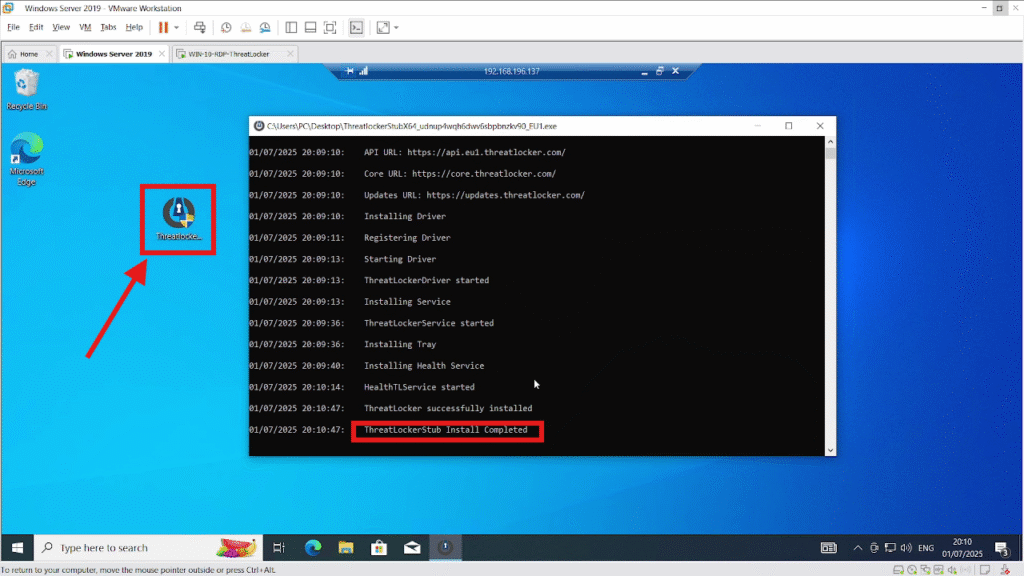
Once connected, copy the previously downloaded ThreatLocker stub EXE file to the remote machine. Then, run the installer on the remote PC with administrator privileges to begin the installation.Once the installation is complete, a message will appear confirming that ThreatLocker install Completed.
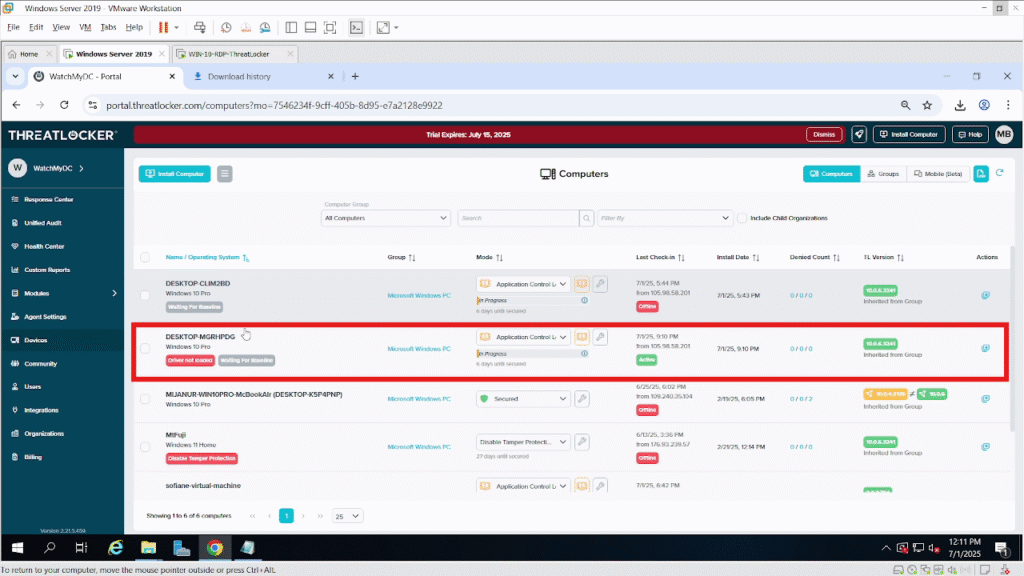
Then, return to the ThreatLocker Portal > Devices the new machine should now be visible and marked as Active in the list.
Conclusion
Installing the ThreatLocker agent via Remote Desktop is a fast and efficient method for deploying protection on remote endpoints without needing physical access. By enabling RDP, downloading the appropriate stub installer, transferring it to the target machine, and executing the installation, you ensure the device is enrolled in ThreatLocker and ready for policy enforcement.
Once completed, the new device will appear in the portal as active, confirming a successful installation.
