
How to Integrate Splunk with ThreatLocker?
This document outlines the step-by-step process of how to use ThreatLocker with Splunk.
This article is a part of our ThreatLocker How-to Guides series, Chapter 12 – Integration & Third-party Tools.
Introduction
What is Splunk?
Splunk is a Security Information and Event Management (SIEM) platform used to collect, monitor, and analyze machine data for security and operational insights.
Objective
Integrate ThreatLocker with Splunk so that ThreatLocker alerts and logs are automatically sent to Splunk for centralized monitoring and analysis.
Implementation
Step 1: Configure the HTTP Event Collector (HEC) in Splunk
- Log in to Splunk.
- In Settings, search for HTTP Event Collector and click it.
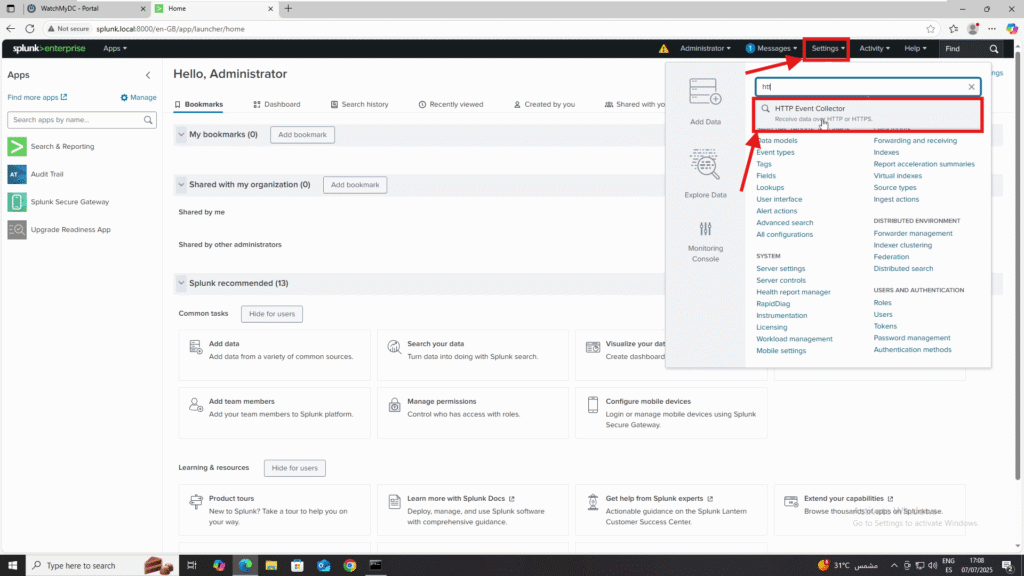
3. Click Create New Token.
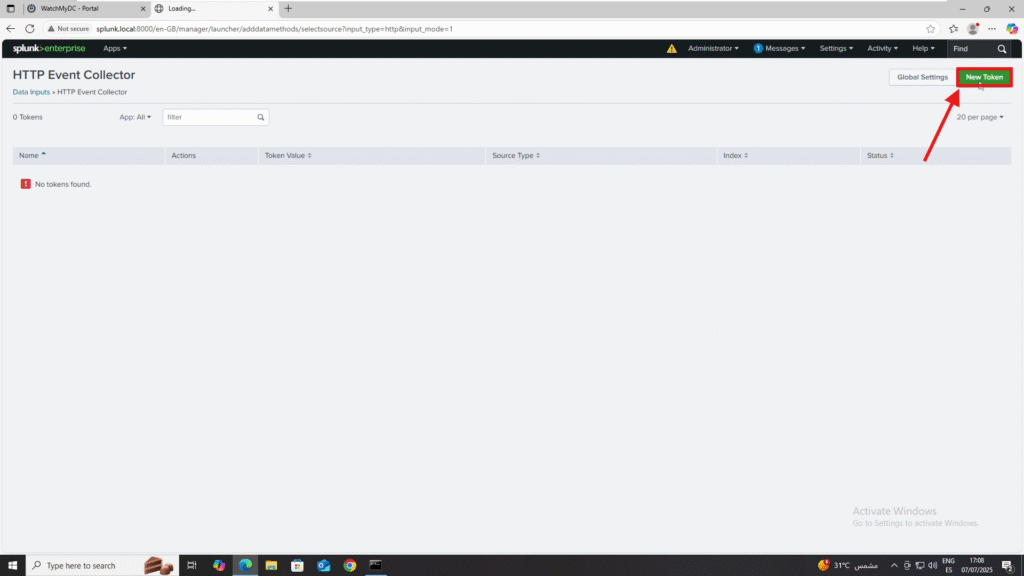
4. Complete the token creation form:
- Name: e.g., ThreatLocker
- Source Name Override: Optional
- Description: Optional
- Output Group: Optional
- Click Next.
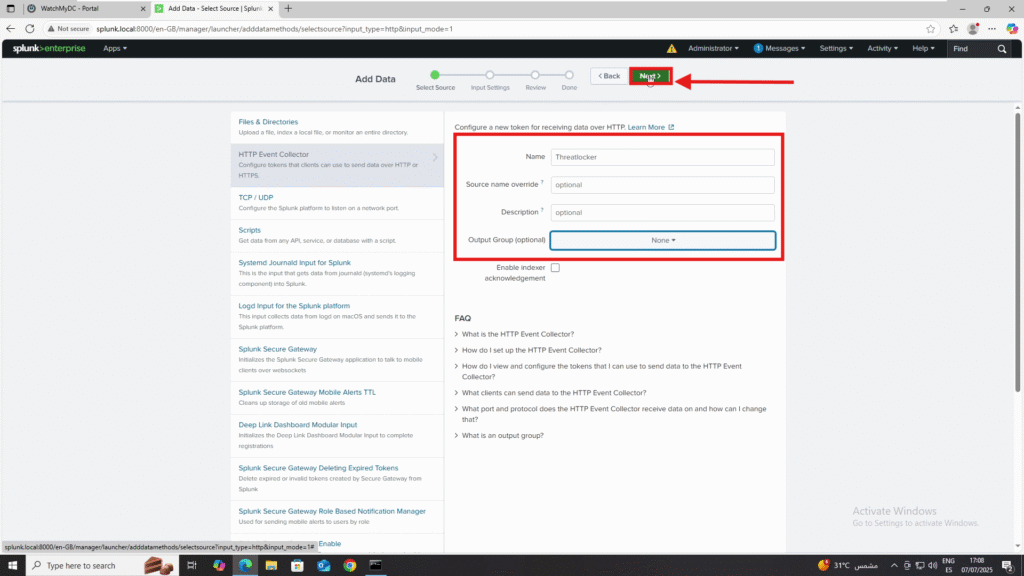
5. In Input Settings, select the Index (e.g., main).
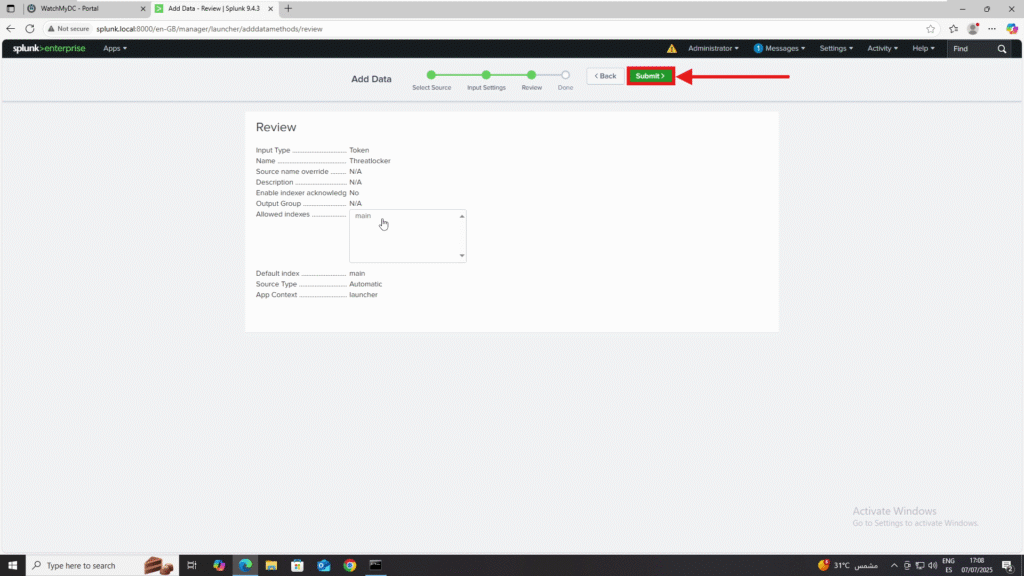
- Click Review.
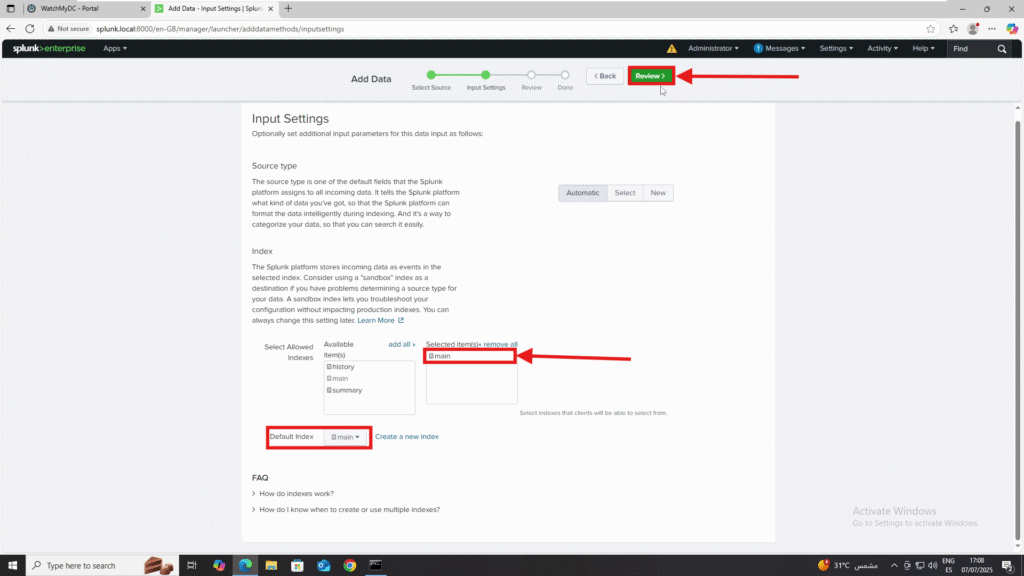
6. Click Submit to confirm
6. Copy the Token Value: this will be used in ThreatLocker.
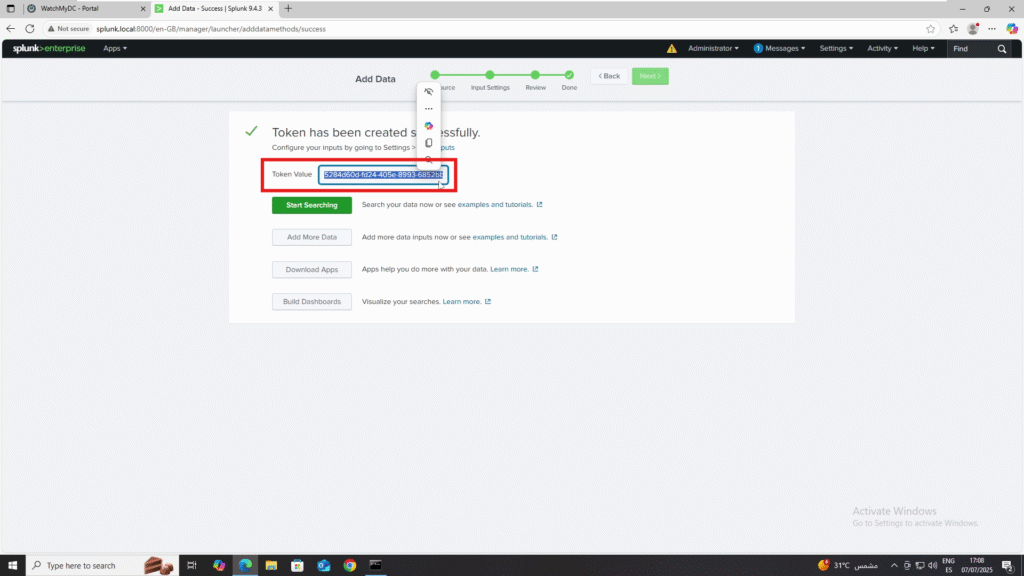
Step 2: Integrate the Token in ThreatLocker
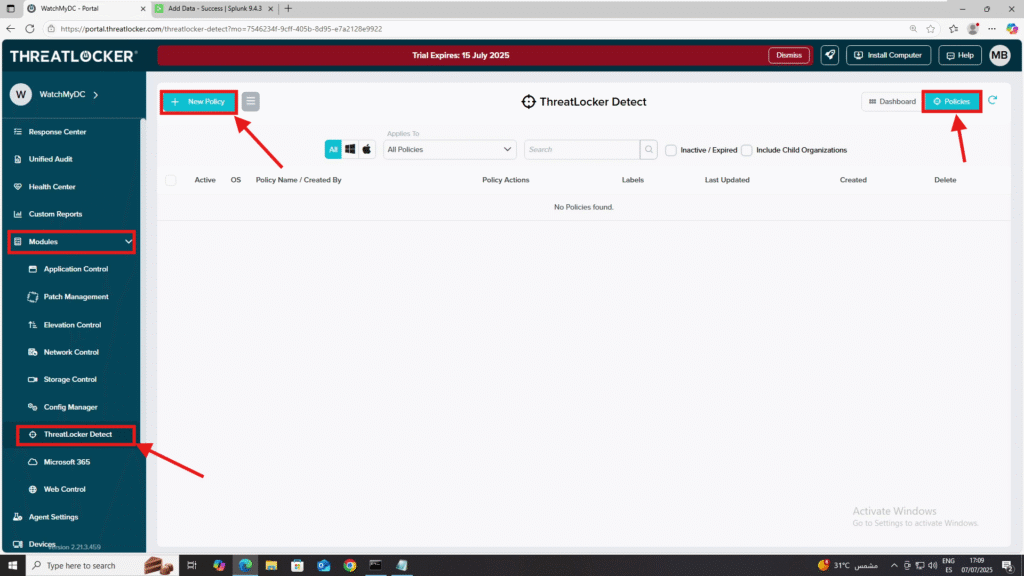
- Log in to the ThreatLocker Portal.
- Navigate to Modules >ThreatLocker Detect > Policies.
- Click New Policy.
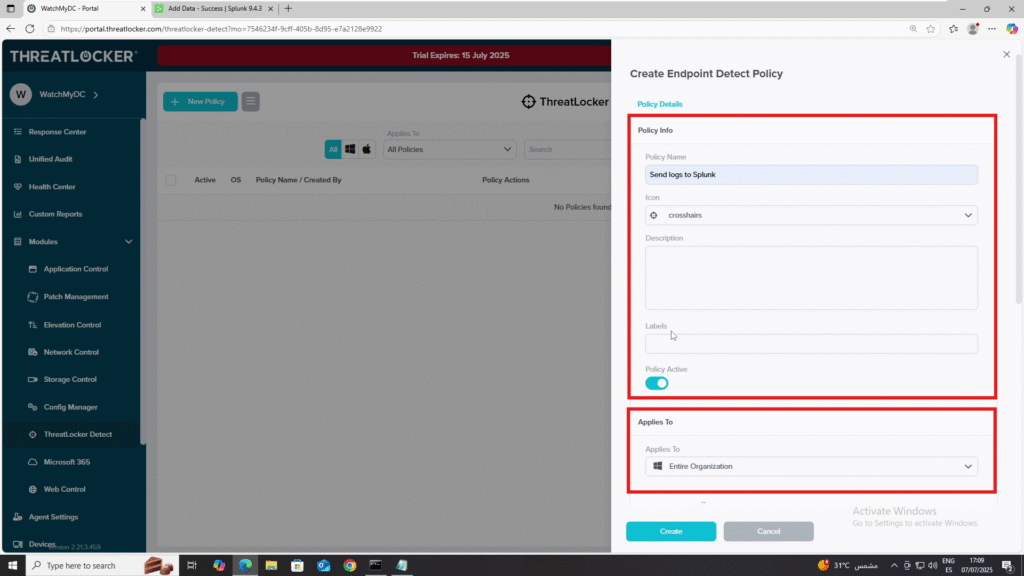
4. Fill out the Policy Info section:
- Policy Name: e.g., Send logs to Splunk
- Icon: Optional
- Description: Optional
- Labels: Optional
5. Applied To: Select the target computer(s) or computer group(s).
6. Policy Conditions:
- Choose If all conditions are true or If any condition is true.
- Add the desired conditions (e.g., Action Type: Deny).
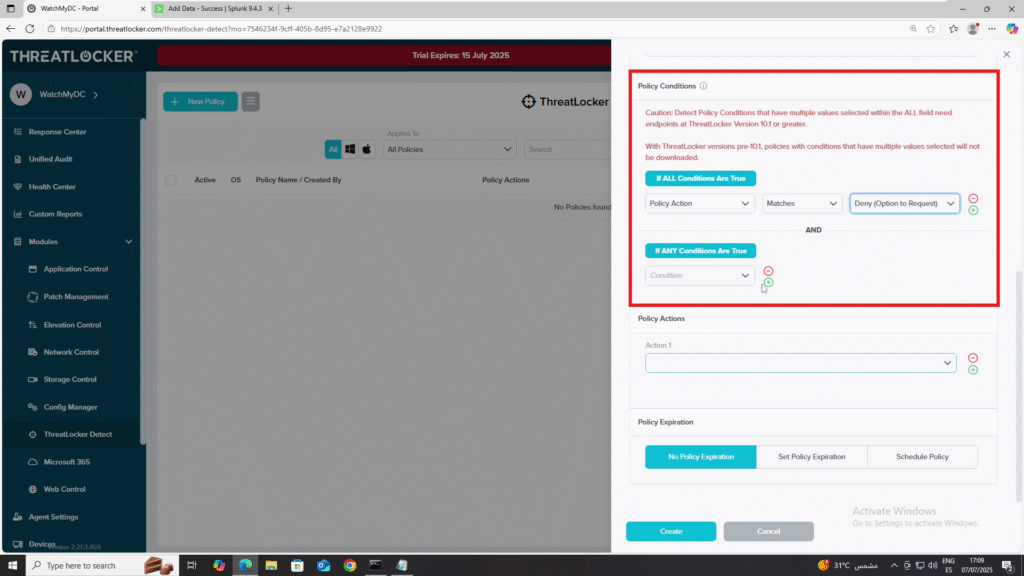
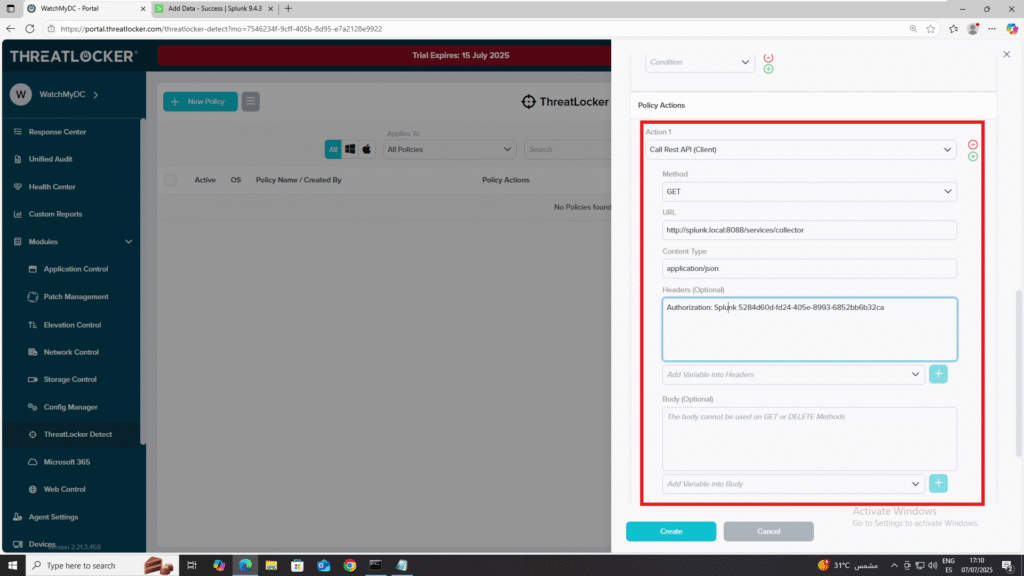
7. Policy Actions:
- Add an action and select Call REST API (Client).
- Method: POST
- URL: http://splunk.local:8088/services/collector
- Content Type: application/json
- Headers: Authorization: Splunk <Your_Token_Here>
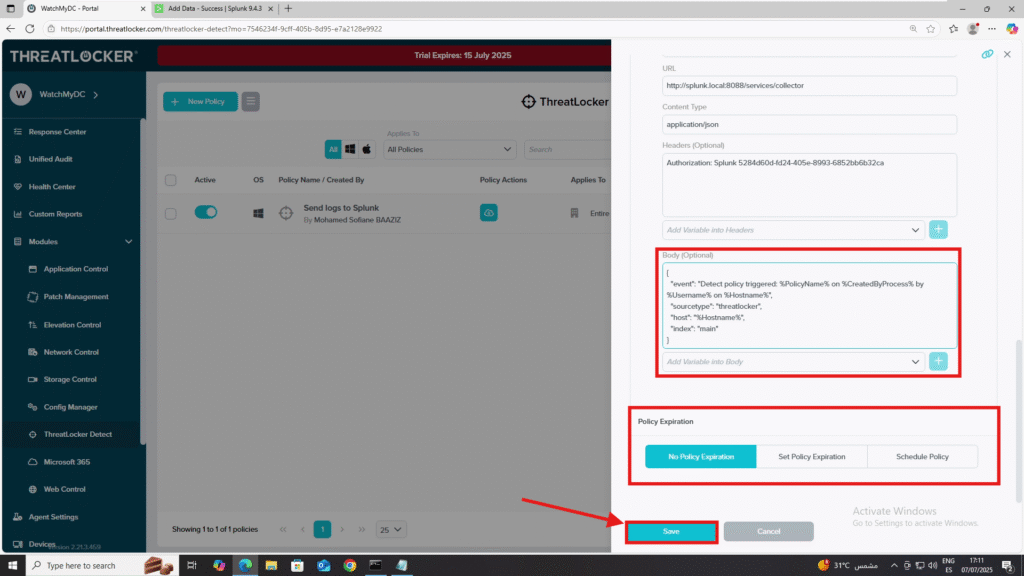
- Body (example):
{
"event": "Detect policy triggered: %PolicyName% on %CreatedByProcess% by %Username% on %Hostname%",
"sourcetype": "threatlocker",
"host": "%Hostname%",
"index": "main"
}8. Policy Expiration: Select No Policy Expiration.
9. Click Save.
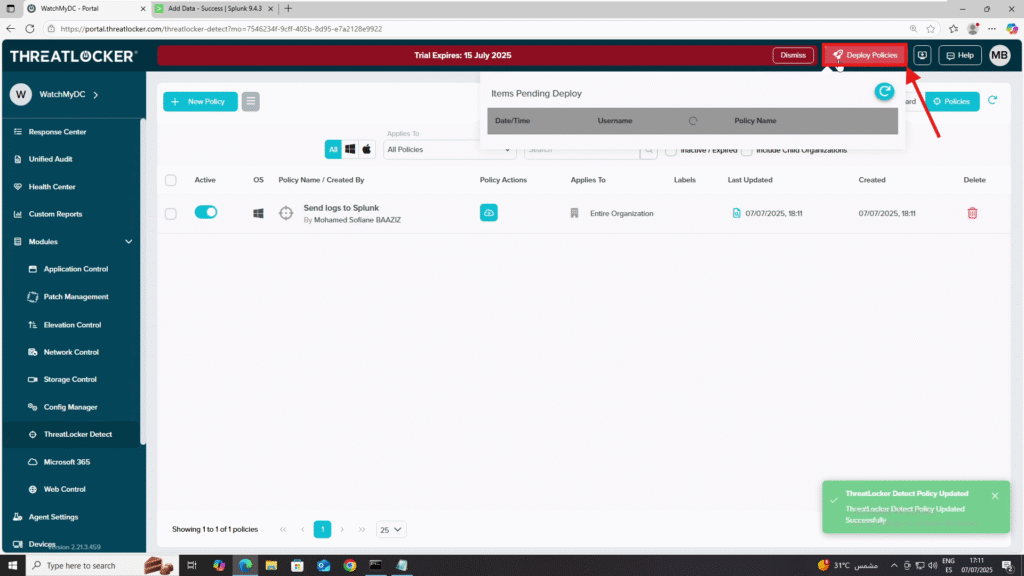
10. Deploy the policy
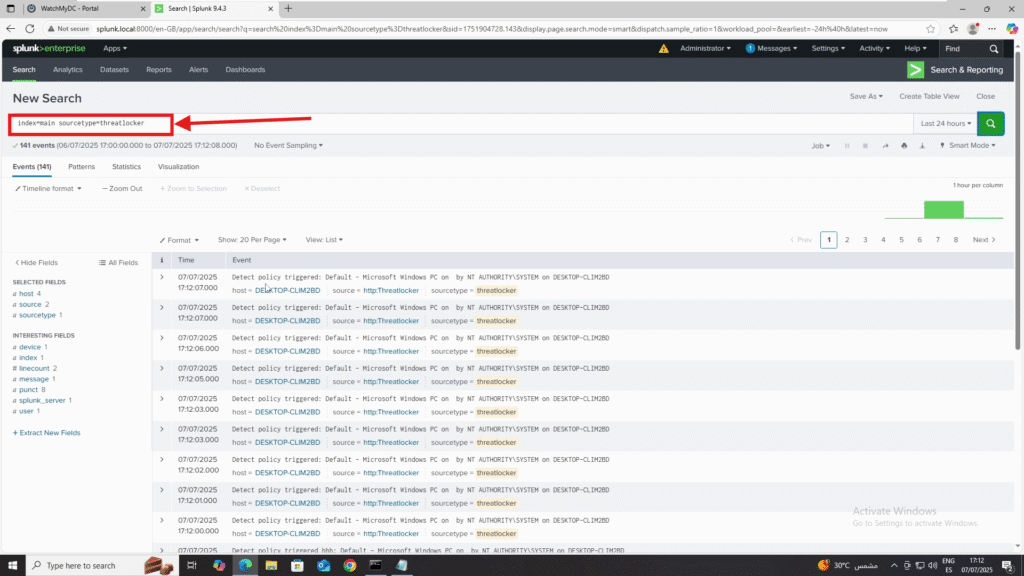
Step 3: Confirm Logs in Splunk
- In Splunk, go to Search & Reporting
- Search: index=main sourcetype=threatlocker
- Click Search to view incoming logs from ThreatLocker.
Conclusion
By integrating ThreatLocker with Splunk through the HTTP Event Collector, you can automatically send and monitor ThreatLocker events in your SIEM dashboard, enabling faster incident detection and response.
