
How to investigate policy violations in ThreatLocker?
This document outlines the step-by-step process of how to investigate policy violations in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 10 – Monitoring, Logs and Reports.
Introduction
Investigating policy violations in ThreatLocker helps identify unauthorized access attempts and determine whether additional policies or exceptions are required. This process involves using both the Health Dashboard for a quick overview and the Unified Audit for detailed analysis.
Implementation
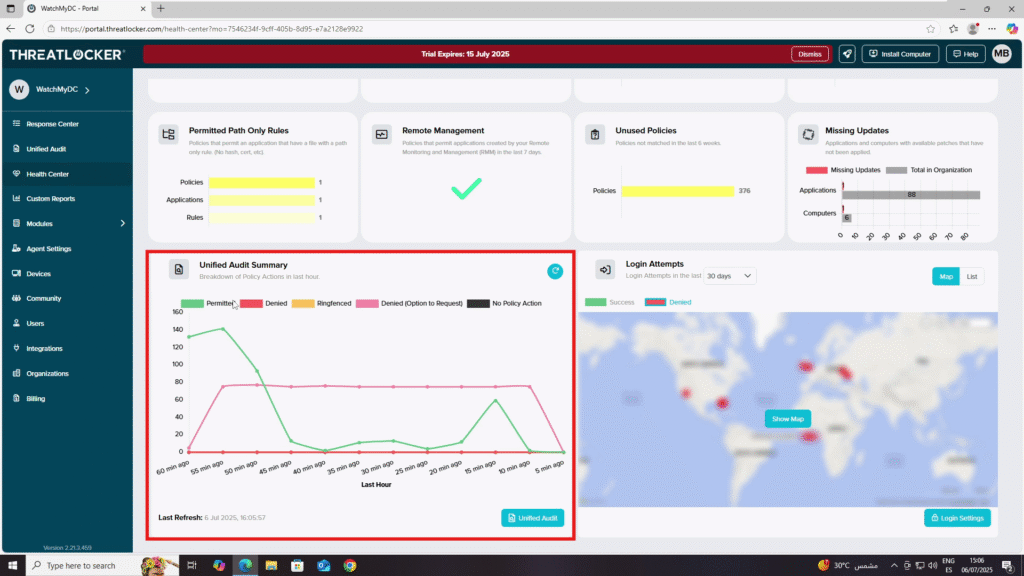
Step 1: Review the Health Center
- Log in to the ThreatLocker Portal.
- Navigate to Health Center from the left-hand menu.
- Review the real-time graphs showing the number of denied actions over the last hour. This helps you quickly identify spikes or unusual activity.
- Use this data as an initial indicator, then proceed to the Unified Audit for deeper investigation.
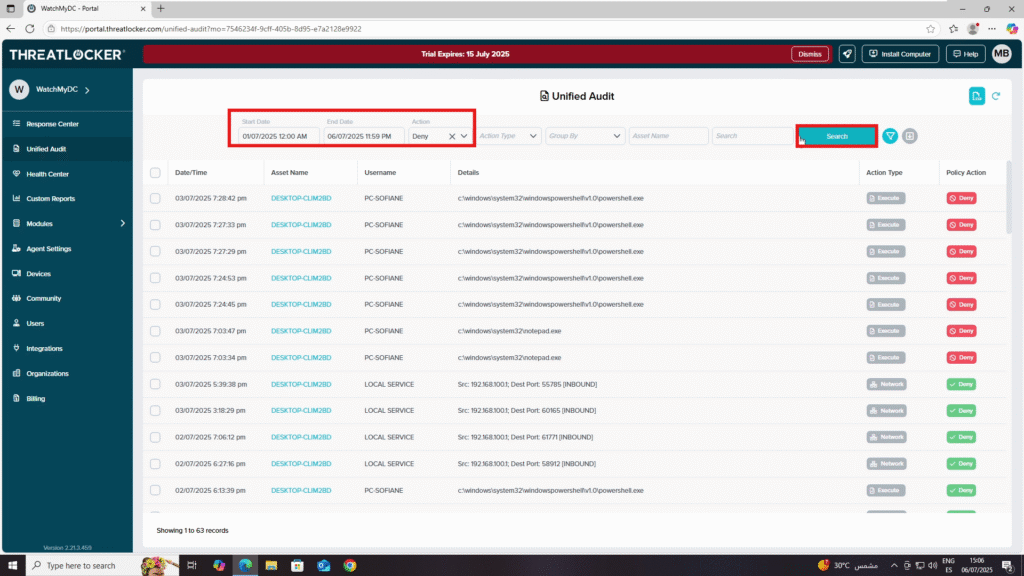
Step 2: Investigate in Unified Audit
- Navigate to Unified Audit.
- In the filter section:
- Set the Start Date and End Date for the investigation period.
- In Action, select Deny to focus on blocked actions.
- Click Search to display all denied actions with details.
- Look for entries with a red “Deny” toggle, which indicates the action was blocked by policy.
- Review the information such as the user, application, and device to understand the cause of the violation.
Conclusion
By combining the quick overview from the Health Dashboard with the detailed logs from Unified Audit, administrators can efficiently investigate policy violations and decide on appropriate corrective actions.
