
How to isolate an application from the network in ThreatLocker?
This document outlines the step-by-step process of how to isolate an application from the network in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 06 – Network Control & Ringfencing.
Introduction
Isolating an application from the network is a powerful way to protect systems from unwanted communications, data exfiltration, or malware activity. With ThreatLocker Application Control, you can apply network ringfencing rules directly to specific applications, blocking them from accessing the internet or communicating over the local network.In this article, we will show how to isolate an application such as Google Chrome from any network access using Application Control and Network Ringfencing.
Implementation
Step 1: Access the Network Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Application Control
- Click Create Policy
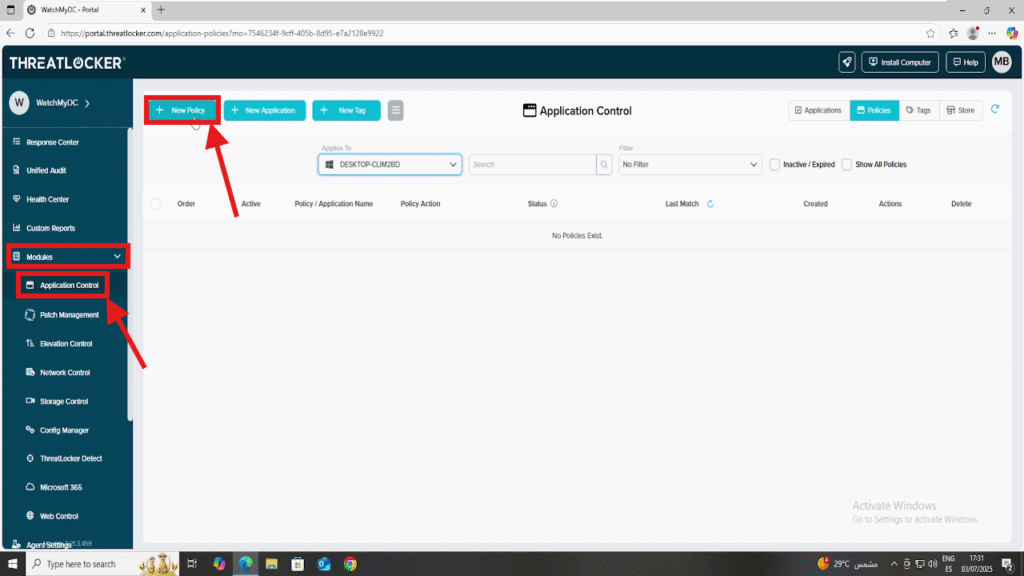
Step 2: Create the Application Control Policy
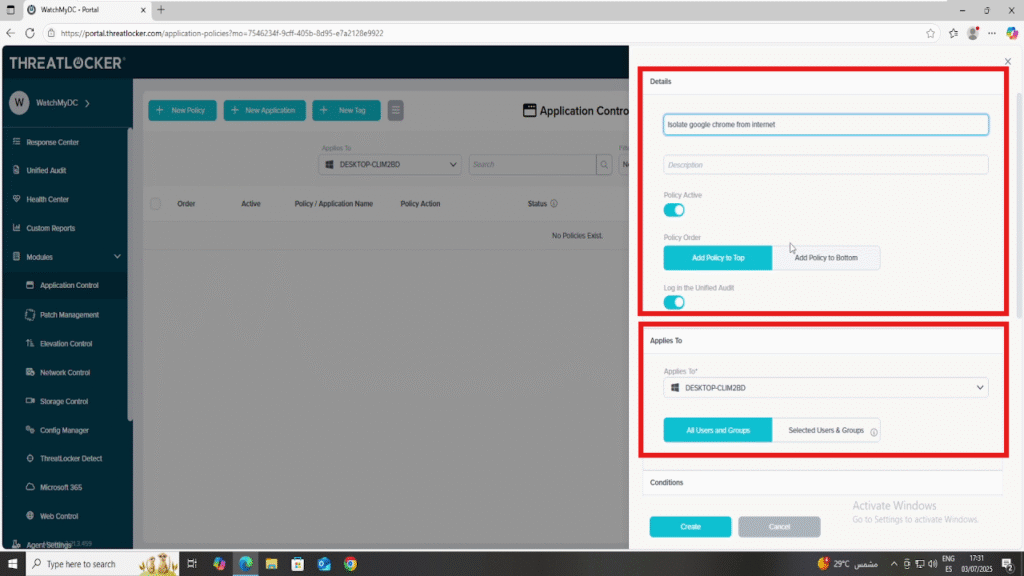
- Fill the policy form:
- In the Details section
- Name: Isolate Google Chrome from internet access
- Description: Prevent Chrome from accessing any network interface
- In the Applied To section
- Select the target computer or computer group where the policy should apply
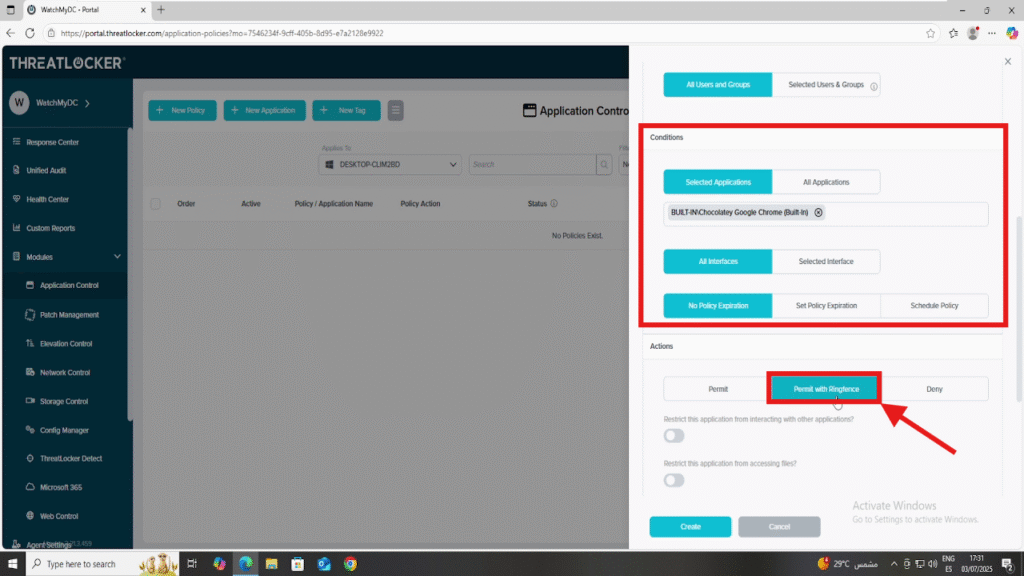
- In the Condition section
- Select the application: Google Chrome
- Select All Interfaces to apply this to all network types
- Set No Policy Expiration to keep the policy active indefinitely
- In the Action section
- Select Permit with Ringfencing
- Then activate the following option:
- Restrict this application from accessing the internet
- Leave the exclusion list empty to fully block all network communication
- Restrict this application from accessing the internet
- Elevation Control can be also enabled to allow the application to run with local administrator privileges for a specific duration (e.g., 8 hours).
- Optionally, enable “Notify User” to display a message informing the user that elevation is active.
2. After completing all required fields, click Create to save the policy
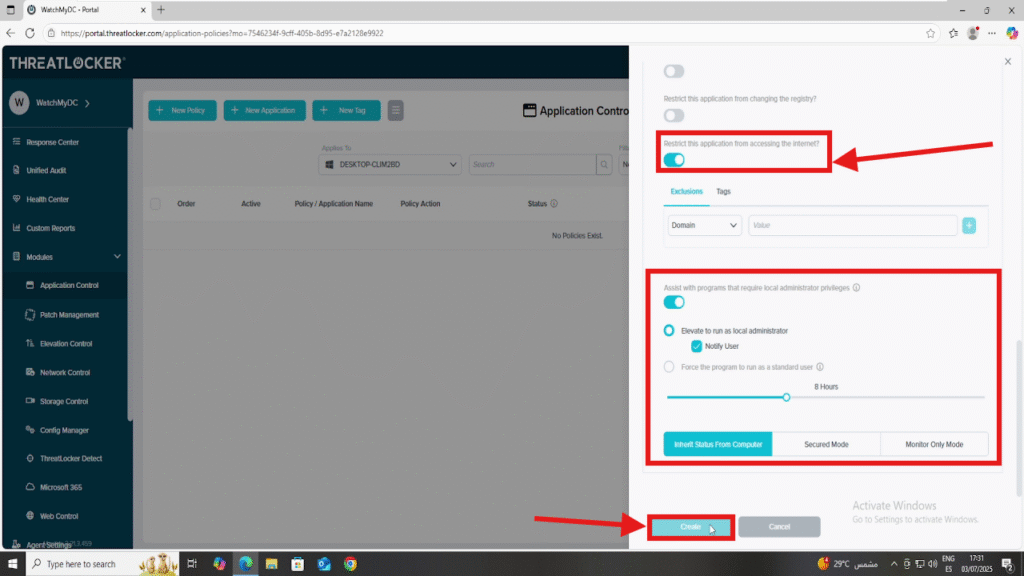
Step 3: Deploy the policy to isolate an application from the network in ThreatLocker
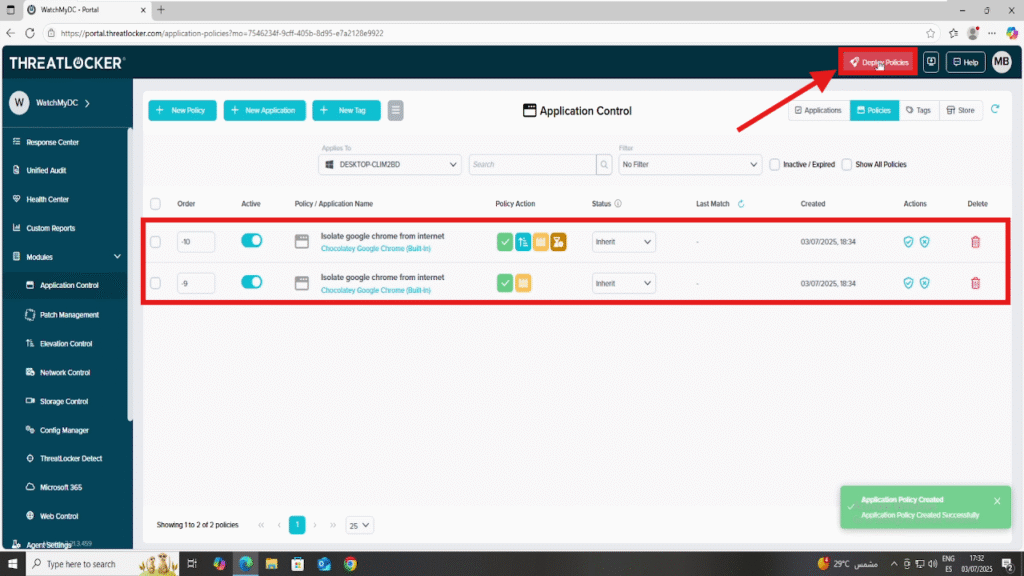
Conclusion
By isolating an application from the network using ThreatLocker, you ensure that it cannot access the internet or communicate with other devices, even if it has full permissions.
This method is especially useful for:
- Blocking internet access for sensitive or legacy applications
- Preventing data leaks and external connections
- Enforcing a Zero Trust approach at the application level
ThreatLocker gives you simple and powerful tools to protect your environment with precision and control.
