
How to log elevated activity in ThreatLocker?
This document outlines the step-by-step process of how to log elevated activity in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 07 – Elevation Control (Privilege Management).
Introduction
ThreatLocker allows administrators to monitor all actions that require elevated privileges. By reviewing elevation logs, you can track which applications were elevated, who ran them, and when. This improves visibility, ensures compliance, and helps detect unauthorized usage of admin rights.
Implementation
Step 1: Access Unified Audit
- Log in to the ThreatLocker Portal.
- Navigate to Unified Audit
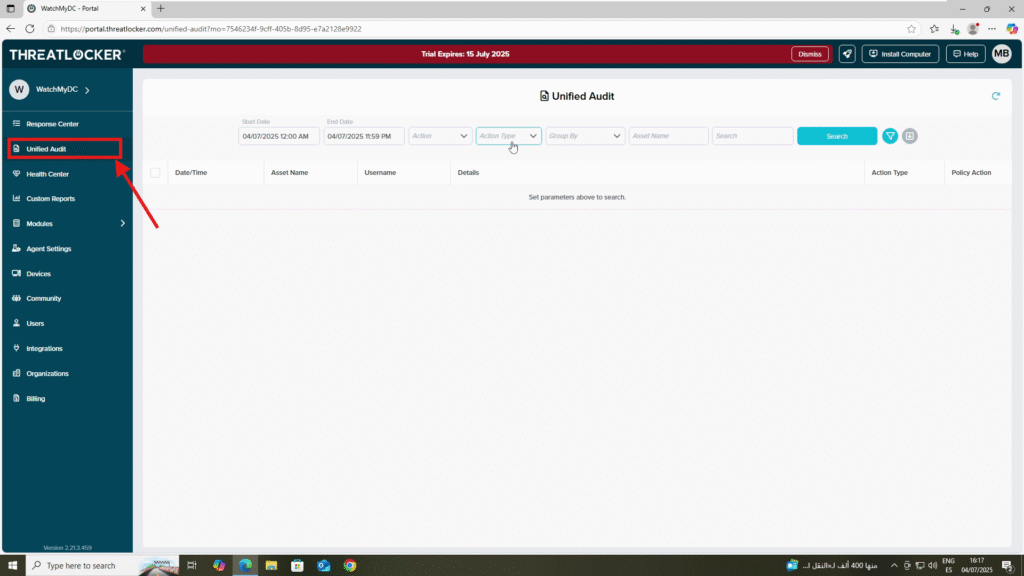
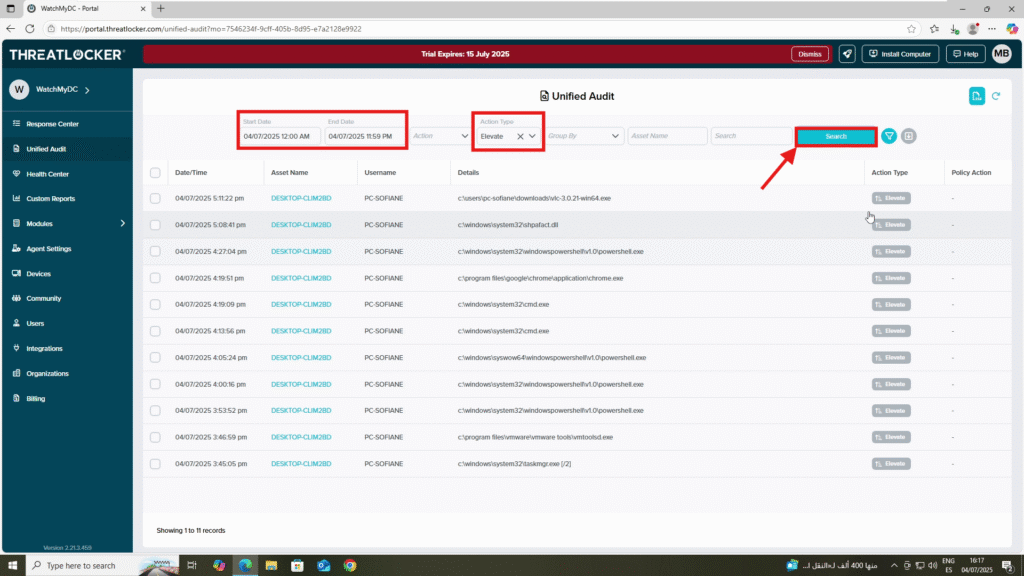
3. In the filter fields, configure the following:
- Date Range: Select a start and end date to define the time period
- Action Type: Set to Elevate to filter only elevated activity
- Click Search to display the logs
- You will see a list of events with detailed information, including Date/Time, Asset Name, Username, Details, Action Type, and Policy Action.
Conclusion
Auditing elevated activity gives you full visibility into when and how elevation is being used across your organization.
By regularly reviewing these logs, you can:
- Ensure elevation is only used where authorized
- Detect anomalies or privilege abuse
- Strengthen your Zero Trust strategy
ThreatLocker’s Unified Audit is an essential tool for tracking and controlling privileged activity in real time.


