
How to log network activity for applications in ThreatLocker?
This document outlines the step-by-step process of how to log network activity for applications in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 06 – Network Control & Ringfencing.
Introduction
Monitoring network activity is essential for understanding how applications interact with external and internal systems. With ThreatLocker Unified Audit, you can review all network-related actions performed by applications, including IP addresses, ports, and protocols used.
This helps with threat detection, compliance auditing, and validating that policies are functioning as expected.
Implementation
Step 1: Access Unified Audit
- Log in to the ThreatLocker Portal.
- Navigate to Unified Audit
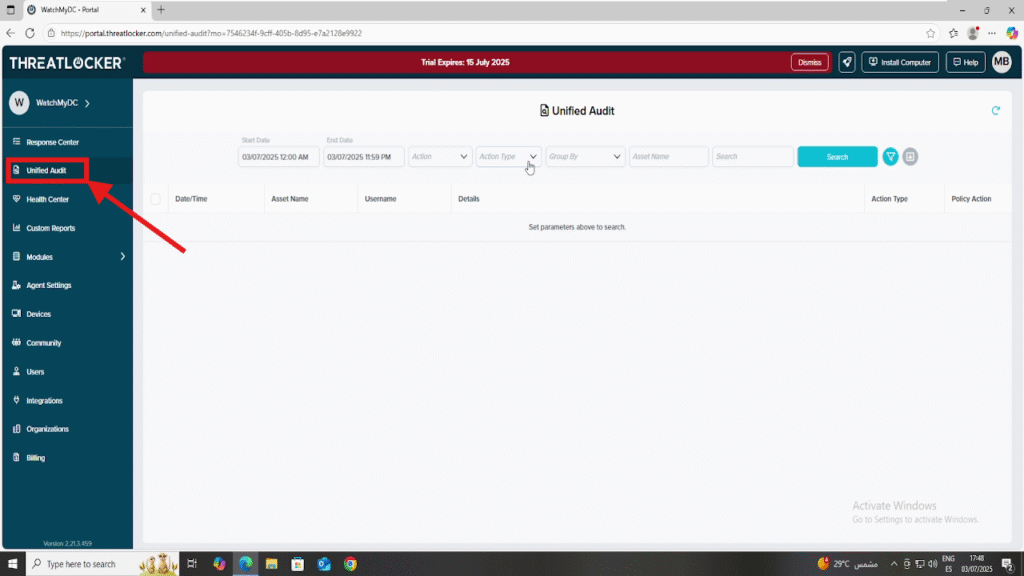
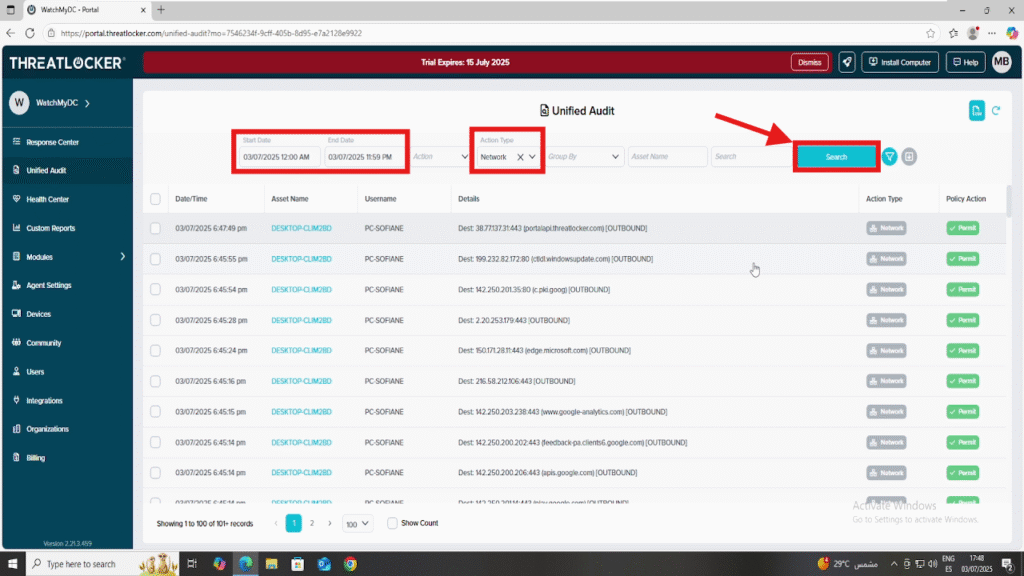
Step 2: Configure the Settings
- Date Range: Select a start and end date to define the time period
- Action Type: Set to Network to view only network activity
- Click Search to display the logs
- You will see a list of events with detailed information, including Date/Time, Asset Name, Username, Details, Action Type, and Policy Action.
Conclusion
Using ThreatLocker Unified Audit, you can easily monitor network activity for any application in your environment. This visibility helps detect anomaly behaviour, enforce Zero Trust policies, and troubleshoot access issues.
Regularly reviewing audit logs improves your organization’s ability to detect network threats early and maintain compliance.
