
How to Log USB Device Activity in ThreatLocker?
This document outlines the step-by-step process of how to log USB device activity in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 05 – Storage Control.
Introduction
Monitoring USB activity is essential for auditing, incident response, and compliance.
Using ThreatLocker’s Unified Audit and Storage Control modules, administrators can log all attempts to access USB storage devices, whether they’re permitted or denied. This includes the user, device, serial number, and timestamp.This guide shows how to ensure logging is active and how to view USB activity logs in ThreatLocker.
Implementation
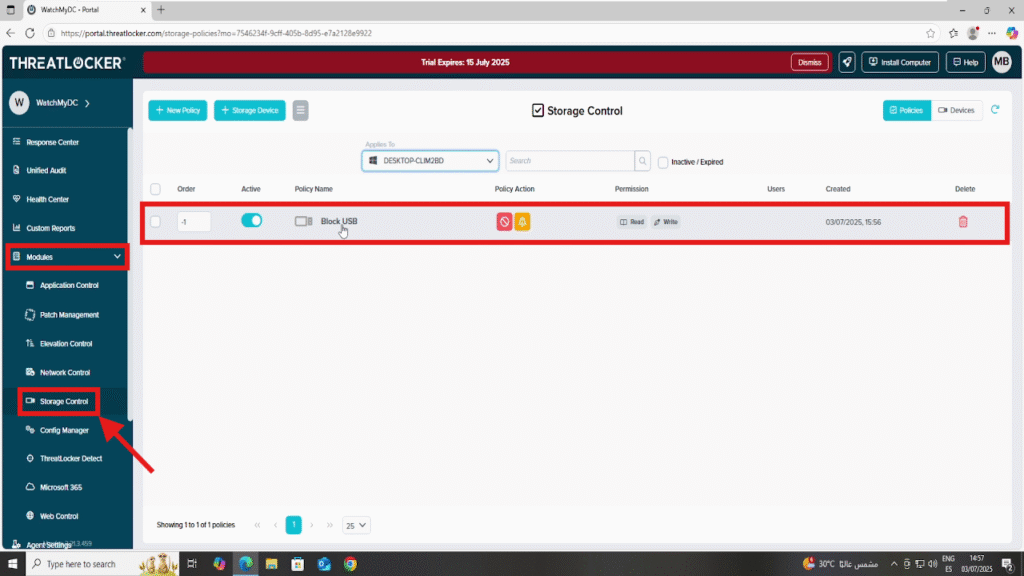
Step 1: Ensure Storage Control Policy Is Active
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Storage Control
- Confirm that at least one Storage Control policy is enabled on the relevant computers
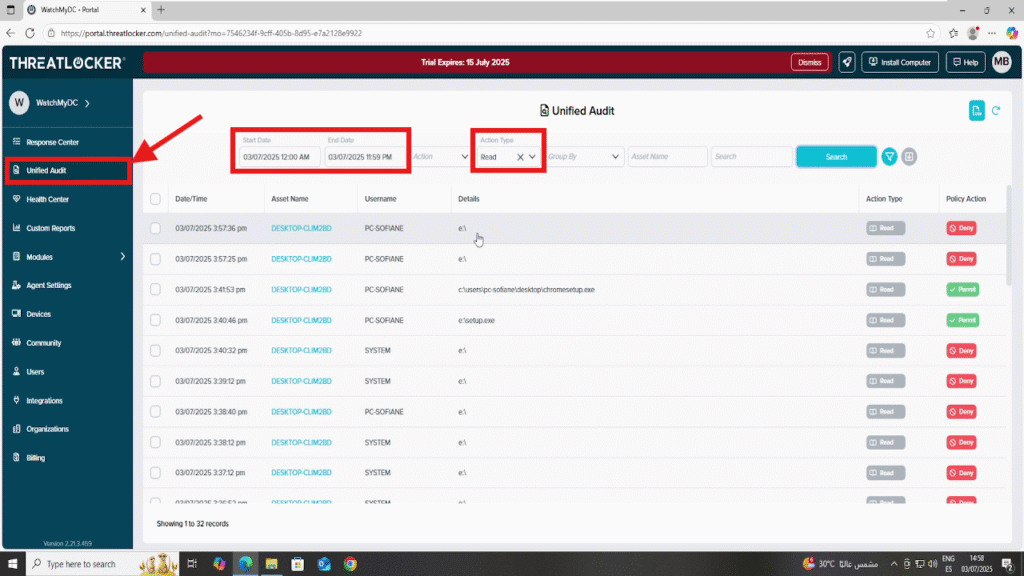
Step 2: View USB Logs in Unified Audit
Go to Unified Audit from the left navigation menu.
In the filter options:
- Choose a date range by setting the Start Date and End ate
- Access Type: Select Read or Write.
You will then see all USB access attempts, including successful and denied actions.
Conclusion
ThreatLocker’s Unified Audit gives you full visibility into all USB storage activity across your endpoints.
By combining it with Storage Control policies, you can monitor, analyze, and respond to every USB access attempt, whether allowed or denied.
This approach helps you to:
- Detect unauthorized USB usage
- Maintain strong audit trails for compliance
- Enforce Zero Trust by reviewing access based on behavior and identity
Logging USB activity is a key component of a secure and transparent IT environment.
