
How to Manage Scheduled Policy Activations in ThreatLocker?
This document outlines the step-by-step process of how to manage scheduled policy activations in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
In some scenarios, security policies need to be active only during specific time periods for example, enabling software during business hours, or disabling tools after working hours.
ThreatLocker allows administrators to schedule policies so they are automatically enabled or disabled based on a predefined schedule.
This guide explains how to configure and manage scheduled activations for application control policies.
Implementation
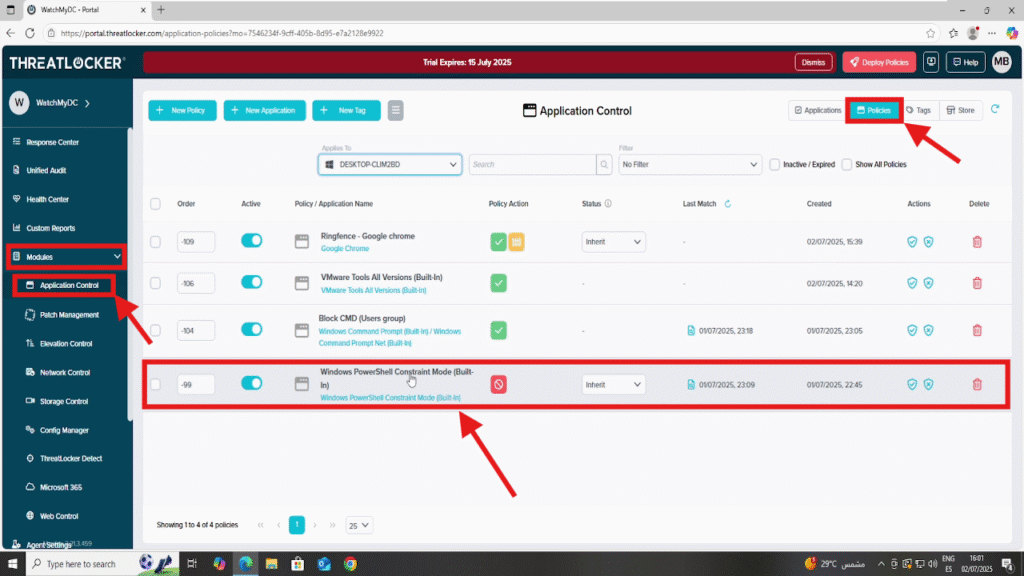
Step 1: Access the Application Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Application Control > Policies.
- Locate or create the policy where you want to apply the temporary rule.
- In this example, we’ll modify the policy for PowerShell.
- Click on the policy to open the configuration panel.
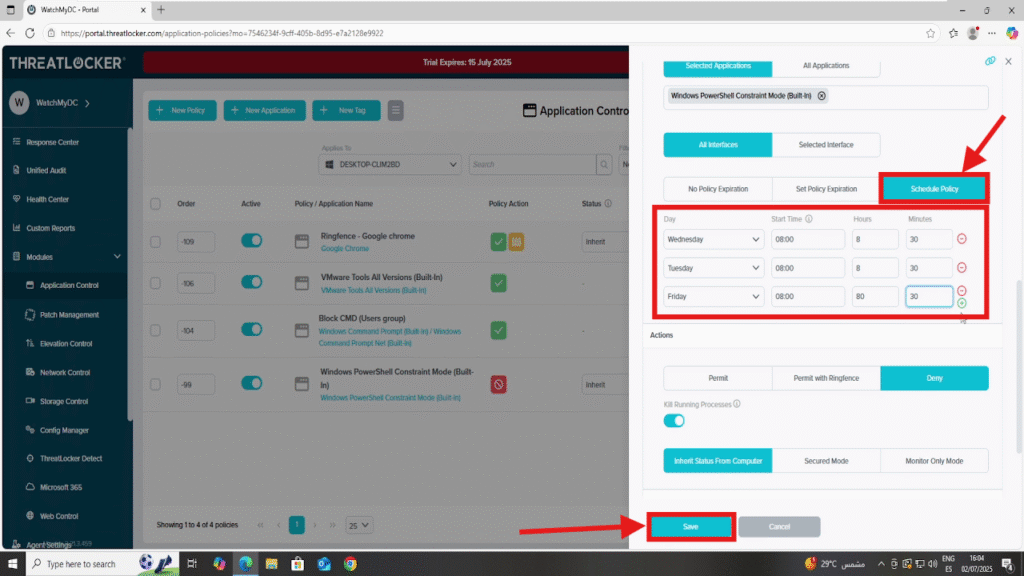
Step 2: Edit the Conditions Section
- Scroll to the Conditions section of the policy editor.
- Enable the option “Schedule Policy”.
- Select the days on which the policy should apply (e.g., Monday to Friday, weekends, or specific days depending on the specific needs of your environment).
- You can add or remove days as needed for precise scheduling.
Step 2: Deploy to apply to manage scheduled policy activation
After making your changes, click the “Deploy” button to apply the updated policy to all relevant endpoints.
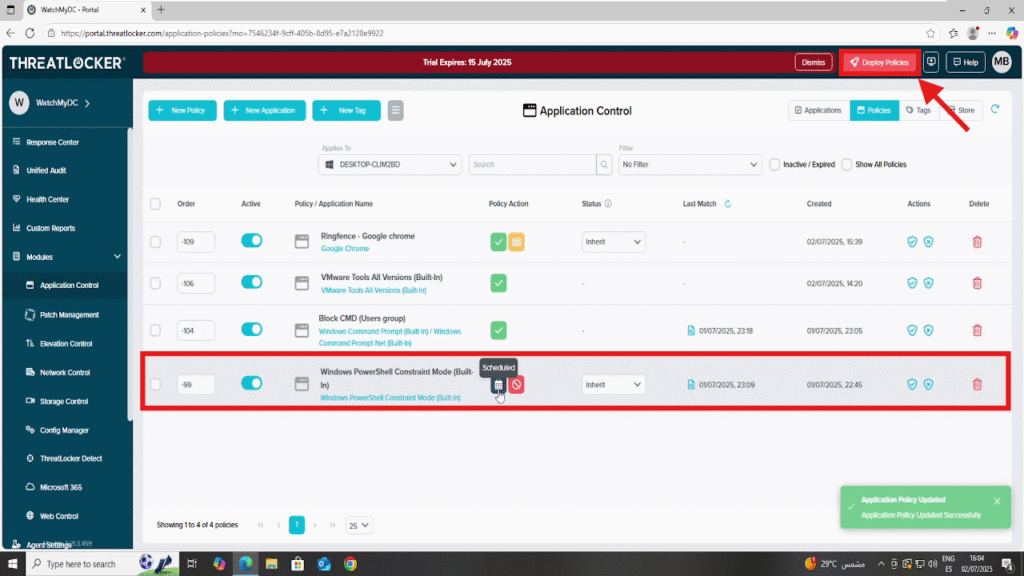
Once deployed, the policy will appear in the list of active policies.
Conclusion
Using Scheduled Policy Activation in ThreatLocker allows you to apply security rules at predefined times, improving automation and reducing administrative overhead.
This is particularly useful for enforcing restrictions during work hours, granting access during maintenance windows, or aligning policies with business operations.By configuring scheduled activations, you maintain strong control while supporting operational flexibility, a key aspect of an effective Zero Trust strategy.
