
How to Monitor File Copy Activity in ThreatLocker?
This document outlines the step-by-step process of how to monitor file copy activity in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 05 – Storage Control.
Introduction
Monitoring file copy activity is crucial for detecting data exfiltration, unauthorized transfers, and ensuring compliance with internal policies.
With ThreatLocker’s Unified Audit, administrators can track when files are written to USB or external devices. This allows them to monitor, investigate, and respond to suspicious behavior in real time.This guide shows how to view file copy attempts using Unified Audit.
Implementation
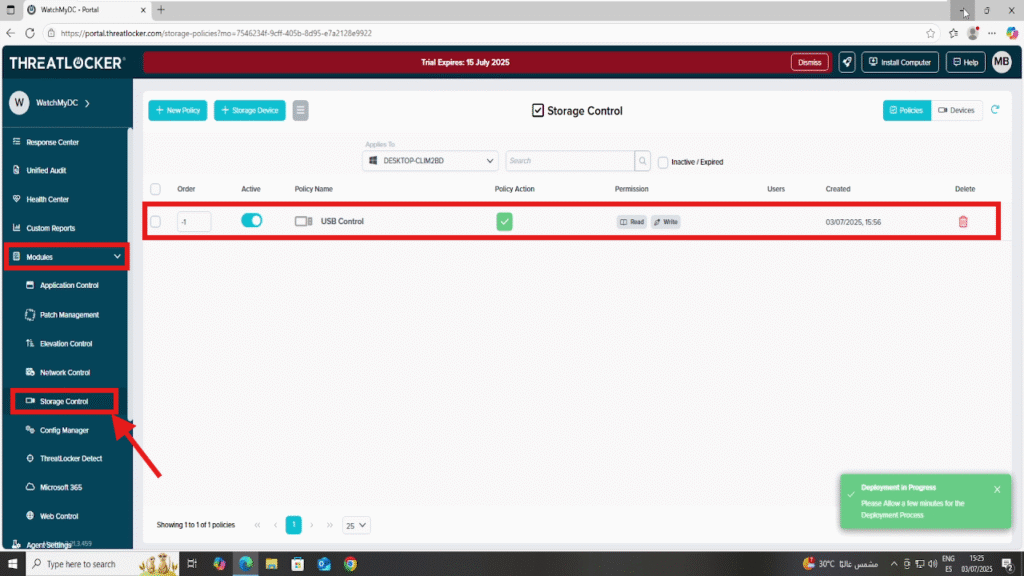
Step 1: Ensure a USB Storage Control Policy Exists
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Storage Control
- Verify that a USB control policy (e.g., “USB Control”) is active
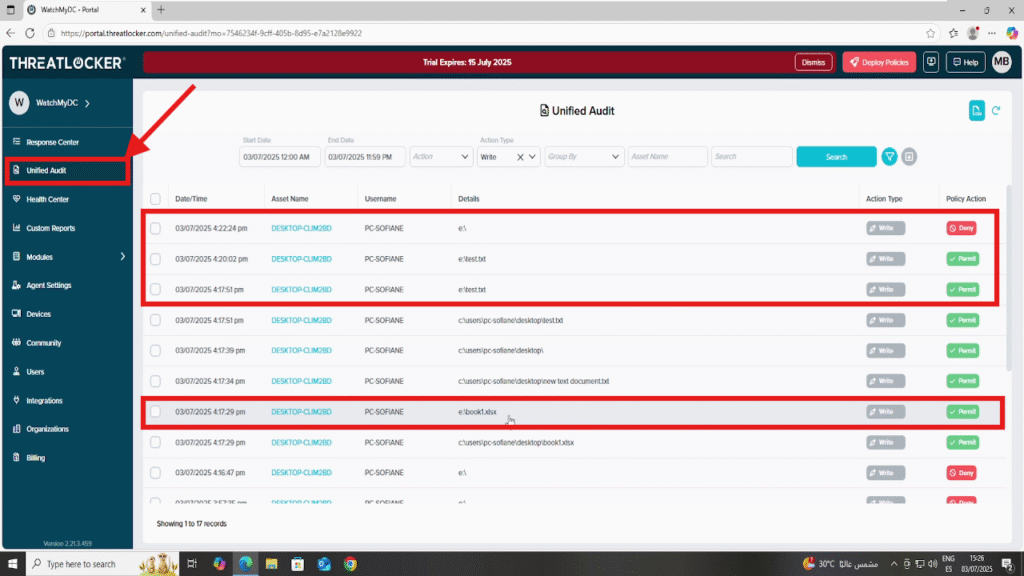
Step 2: Navigate to Unified Audit
- Use the following filters:
- Date Range: Set the Start Date and End Date
- Access Type: Select Write to view file copy and file modification attempts
Click Search and you will now see detailed logs showing:
- The user who performed the copy
- The file path
- The target device
- Timestamp and policy result (Allowed or Denied)
Conclusion
With ThreatLocker’s Unified Audit, monitoring file copy activity is simple and precise.
This allows you to:
- Detect unauthorized data transfers
- Investigate suspicious behavior
- Strengthen compliance and data protection strategies
- Maintain full visibility over USB write operations
Combined with Storage Control, Unified Audit gives you full control and traceability over file movement in your organization.
