
How to monitor USB device usage in ThreatLocker?
This document outlines the step-by-step process of how to monitor USB device usage in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 10 – Monitoring, Logs and Reports.
Introduction
Monitoring USB device usage is essential for maintaining security and preventing unauthorized data transfer. ThreatLocker provides the ability to track all read and write operations to external devices via the Unified Audit module.
Implementation
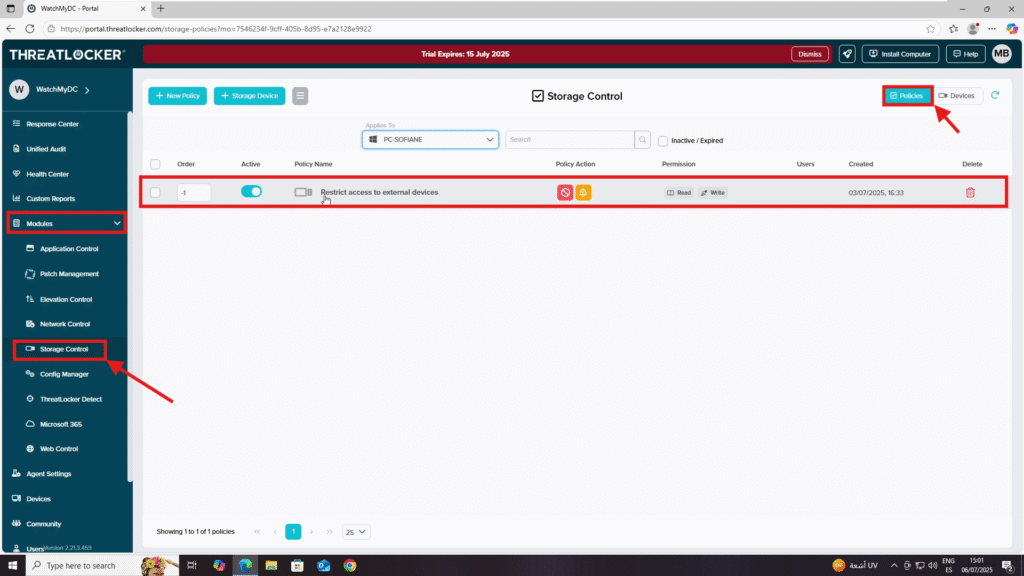
Step 1: Confirm that a USB Device Policy Exists
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Storage Control > Policies.
- Check if a policy controlling USB or external device access exists (e.g., Restrict Access to External Devices).
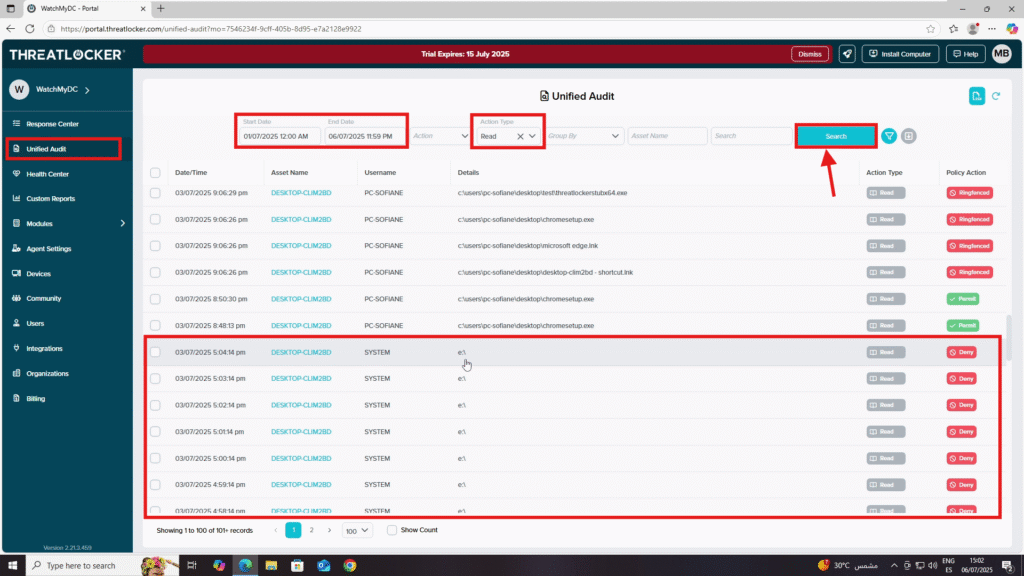
Step 2: Monitor Activity in Unified Audit
- After a USB or external device has been used (read/write actions performed), go to Unified Audit.
- In the filter section:
- Set the Start Date and End Date.
- In Action Type, select Read or Write (depending on what you want to monitor).
- Click Search to display all logs.
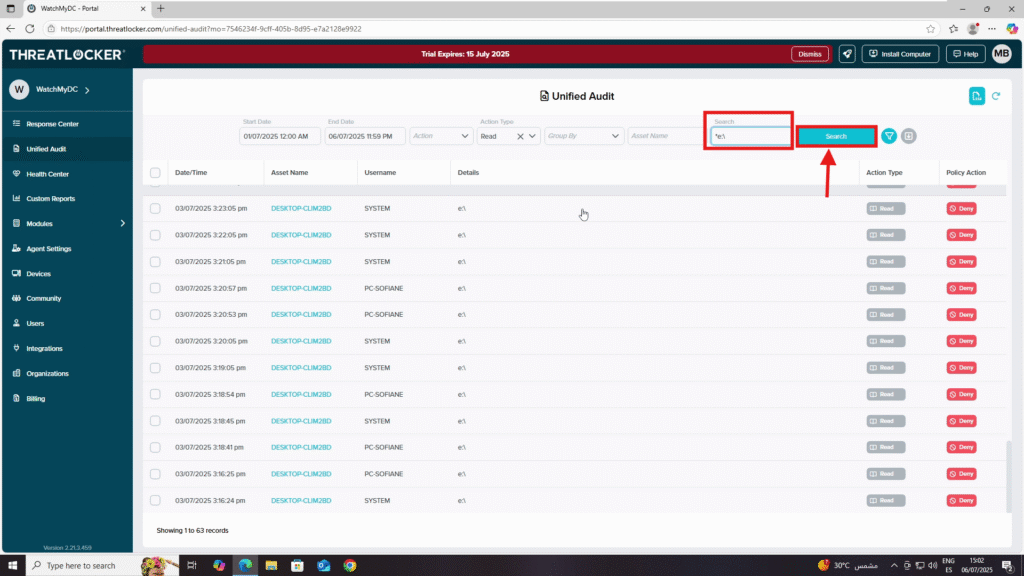
4. To focus on a specific USB drive, locate its path (e.g., /E) and use the search bar with a wildcard: */e
5. Then click Search again to filter only that device’s activity.
Conclusion
By ensuring a proper USB policy is in place and using Unified Audit’s filtering tools, administrators can easily track all USB device interactions, helping maintain compliance and data security.
