
How to monitor user activity in ThreatLocker?
This document outlines the step-by-step process of how to monitor user activity in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 09 – User and Device Management.
Introduction
Monitoring user activity is essential for tracking changes, access attempts, and policy-related actions within the ThreatLocker environment. The User Audit feature allows administrators to review detailed logs of user actions, including logins, policy changes, and other interactions.
Implementation
Step 1: Access the Computer Management Section
- Log in to the ThreatLocker Portal.
- Navigate to Users > Audits
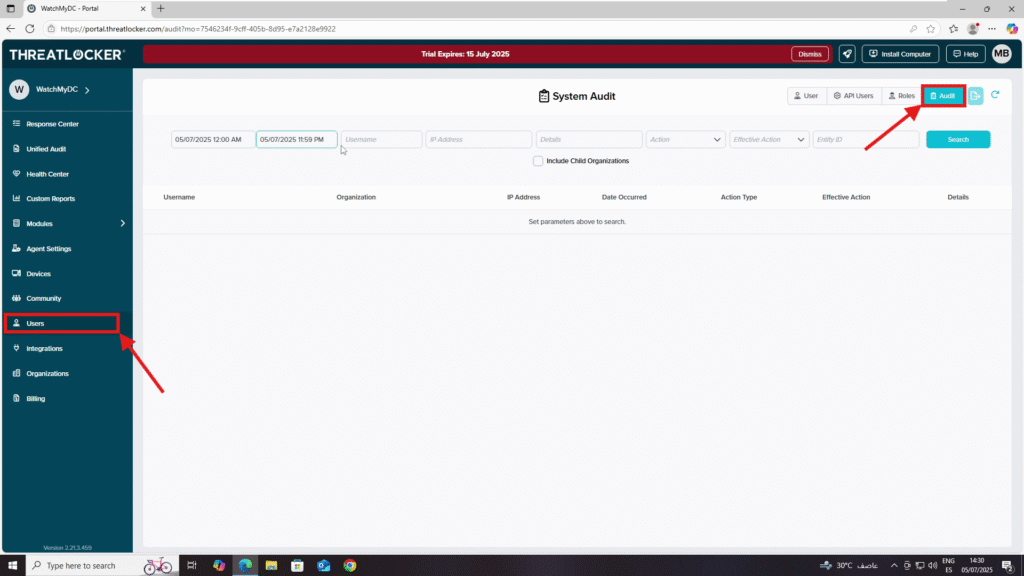
Step 2: Monitor User Actions
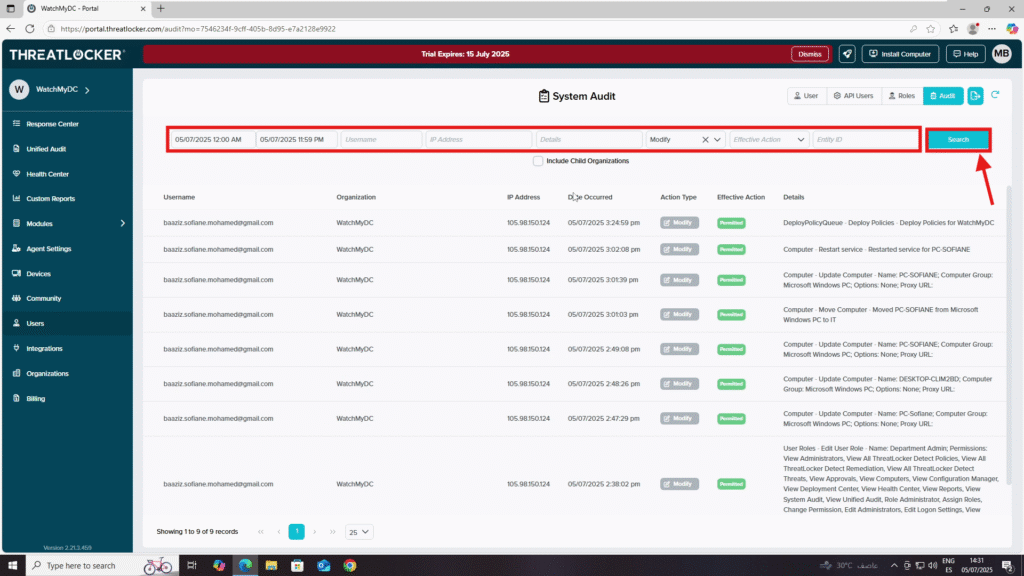
- In the Audit Users section, use the available filters to narrow down the results:
- Date Range: Set the Start and End Date
- Username: Filter actions by a specific user
- IP Address: Track actions from a specific IP
- Details: Search for keywords related to the action
- Action: Select types of activity to monitor (e.g., Create, Delete, Logon, Modify, Read)
- Once filters are configured, click Search to display the activity logs.
- You will see entries with details such as:
- Username
- Organization
- IP Address
- Date/Time of the event
- Action Type
- Additional details
Conclusion
The User Audit section provides a clear view of user-related events in your organization. By using filters effectively, you can monitor access attempts, configuration changes, and policy actions to maintain compliance and security visibility.
