
How to prevent lateral movement via network control in ThreatLocker?
This document outlines the step-by-step process of how to prevent lateral movement via network control in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 06 – Network Control & Ringfencing.
Introduction
Lateral movement occurs when attackers gain access to one endpoint and attempt to move across the network to other systems. Blocking such movement is essential to contain attacks and safeguard critical resources.
With ThreatLocker Network Control, you can create policies that restrict access to sensitive ports and services commonly used for lateral movement, such as SMB, SSH, and Telnet.
This guide explains how to configure a network control policy to stop lateral movement across your infrastructure.
Implementation
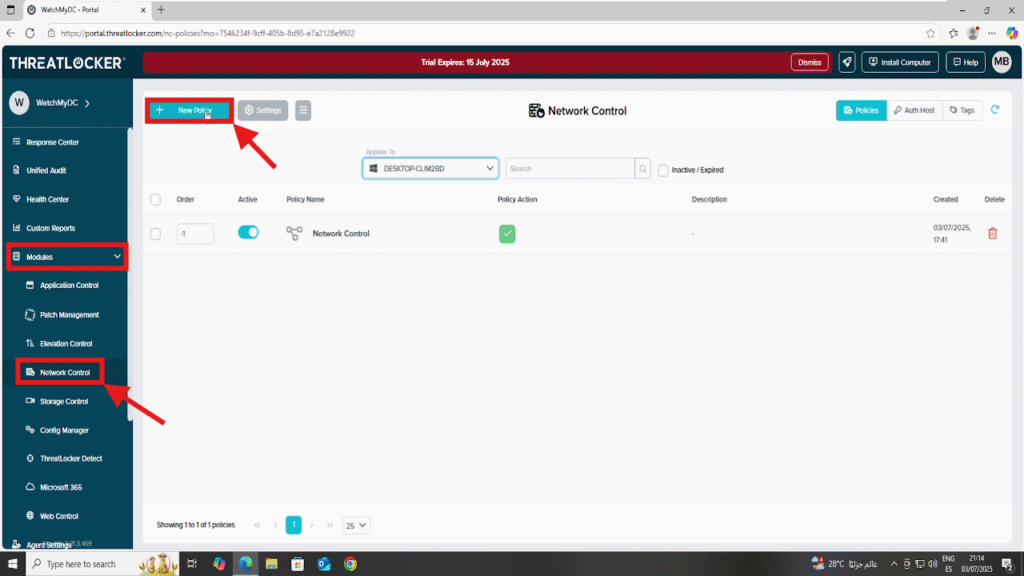
Step 1: Access the Network Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Network Control
- Click Create Policy
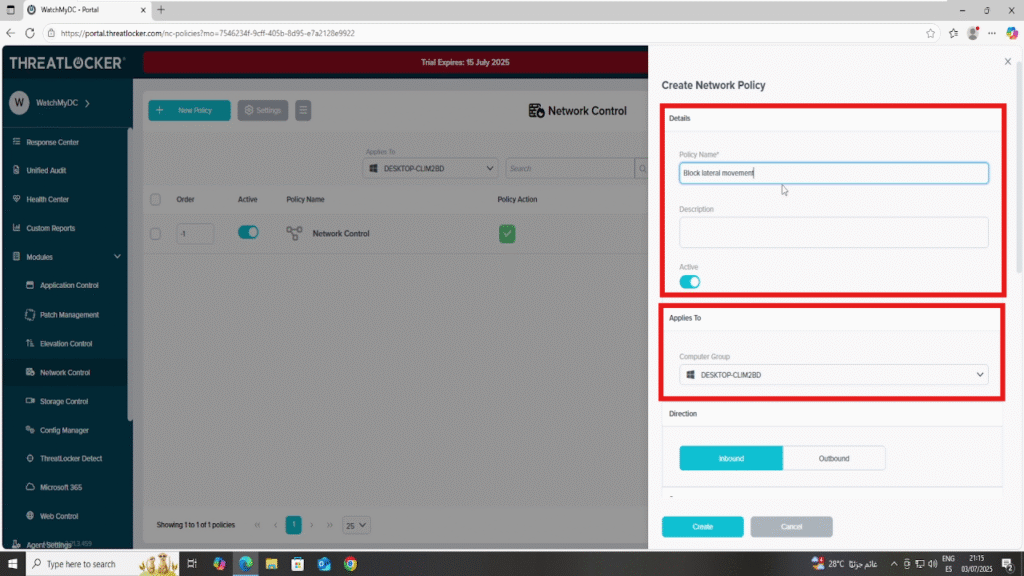
Step 2: Create the Network Control Policy
- Fill the policy form
- In the Details section
- Name: Block Lateral Movement
- Description: Prevent access to ports commonly used for internal lateral movement
- In the Applied To section
- Select the target computer or computer group where this policy will be applied
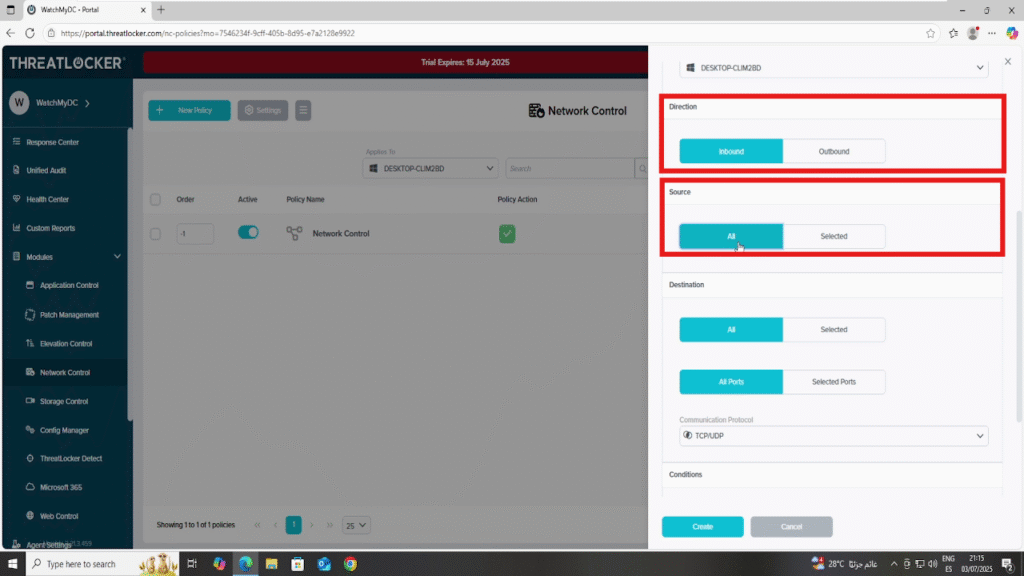
- In the Direction section
- Choose Inbound to block incoming access to specific ports.
2. In the source section:
- Select All to cover all potential originating devices
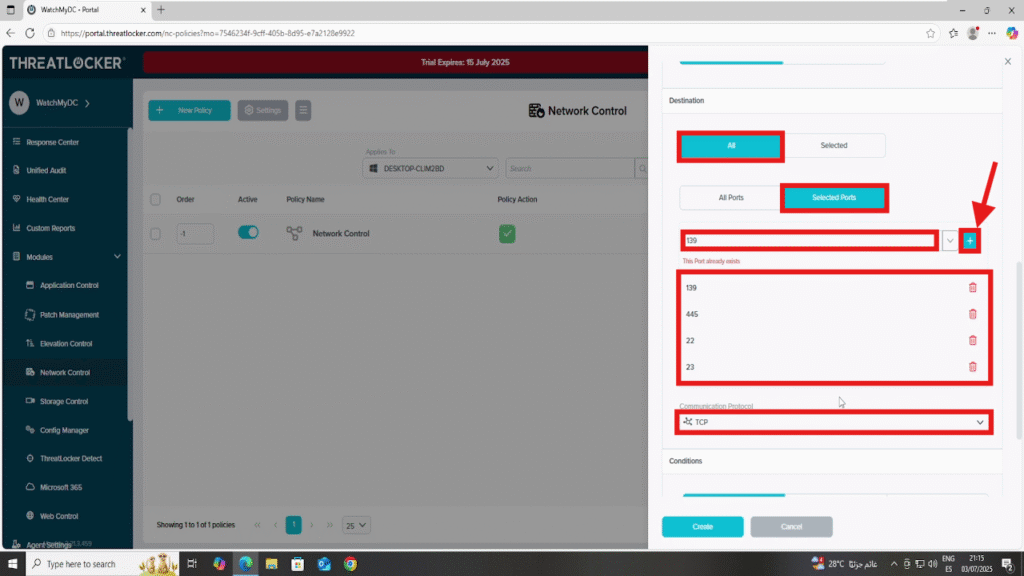
- In the Destination section
- Select All
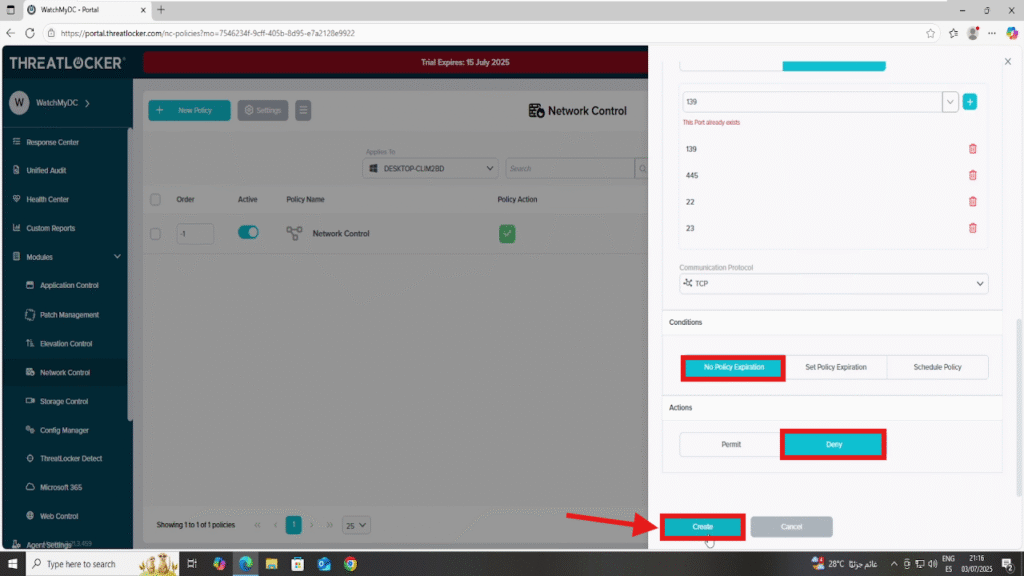
- In the Port field, select “Selected” and specify the following ports:
- 139 (SMB)
- 445 (SMB)
- 22 (SSH/SCP/SFTP)
- 23 (Telnet)
- Set Protocol to TCP
- In the Condition section
- Select No Policy Expiration to ensure the rule remains active indefinitely
- In the Action section
- Select Deny to block all matching traffic
Once all fields are configured, click Create to save the policy
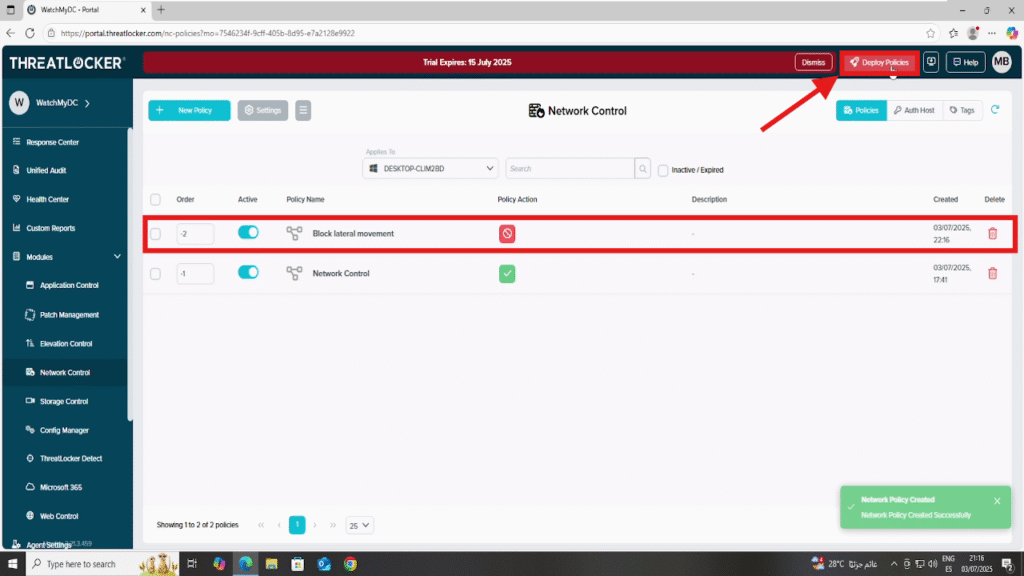
Step 3: Deploy the policy to prevent lateral movement via network control in ThreatLocker
Then click Deploy to enforce the policy across the selected devices
Conclusion
By blocking internal network ports such as SMB, SSH, and Telnet using ThreatLocker Network Control, you significantly reduce the risk of lateral movement across your organization.
This approach helps contain threats, limits attacker mobility, and reinforces your Zero Trust strategy by controlling communication at the network level.
ThreatLocker makes it easier to define and enforce policies that stop lateral spread before it becomes a serious incident.
