
How to Request Elevation Approval as a User in ThreatLocker?
This document outlines the step-by-step process of how to request elevation approval as a user in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 07 – Elevation Control (Privilege Management).
Introduction
With ThreatLocker Elevation Control, users can request temporary admin rights for specific applications, without needing full local administrator access. This ensures strong security while maintaining operational flexibility.
This guide explains how users can request elevation from their endpoint and how administrators can confirm and process the request.
Implementation
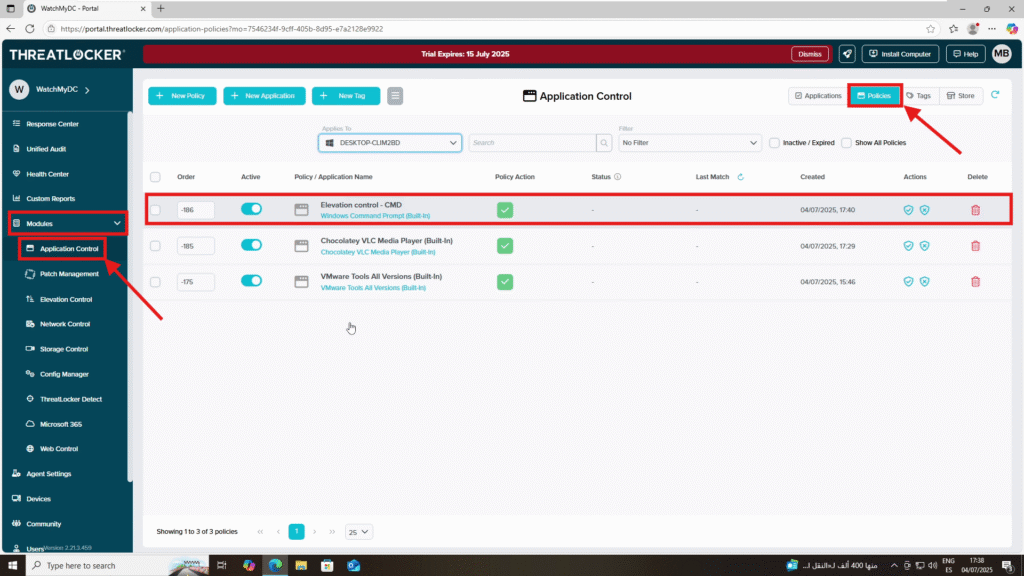
Step 1: Confirm That an Elevation Policy Exists
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Application Control > Policies
- Locate the elevation policy related to the application (e.g., CMD)
- Ensure the policy is active and deployed on the target computer
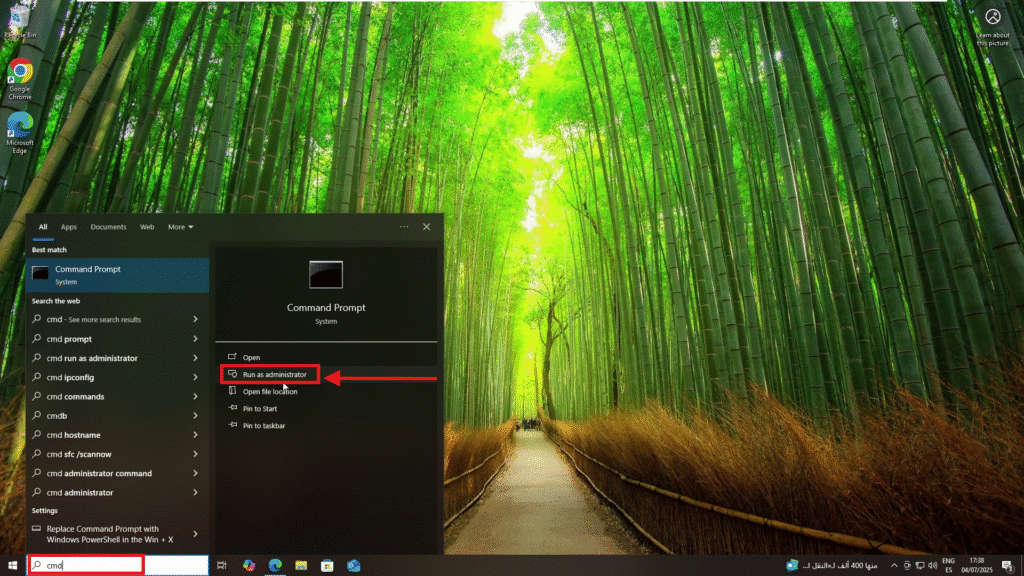
Step 2: Request Elevation from the Endpoint
- On the target computer, try to open the application that requires elevation (e.g., Command Prompt as Administrator)
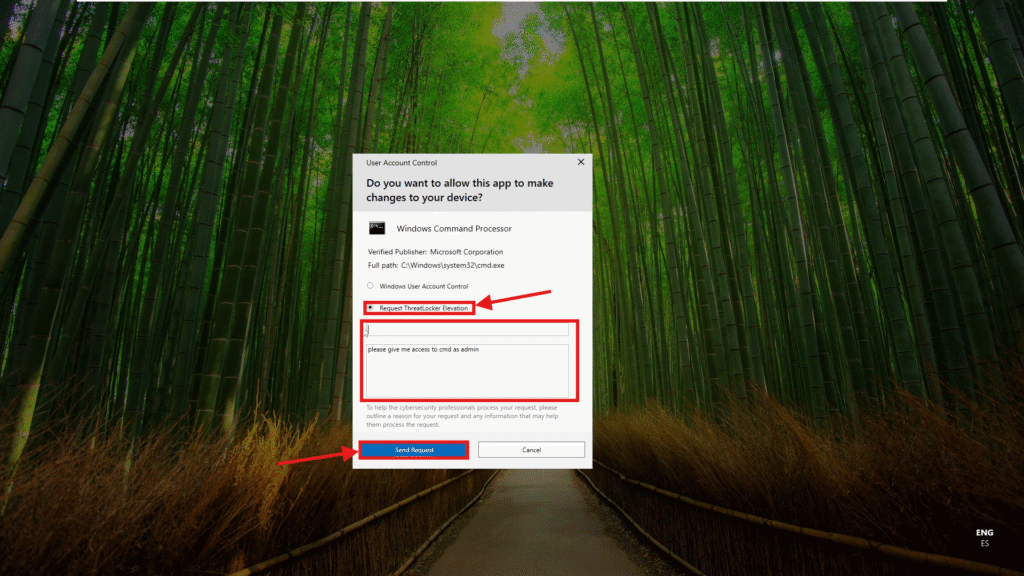
2. The Windows User Account Control (UAC) window will appear
3. Click Request ThreatLocker Elevation
4. Fill in the request form:
- User ID / Email (optional)
- Information: Add a message explaining the reason for the request (e.g., “Need to install drivers”)
5. Click Send Request
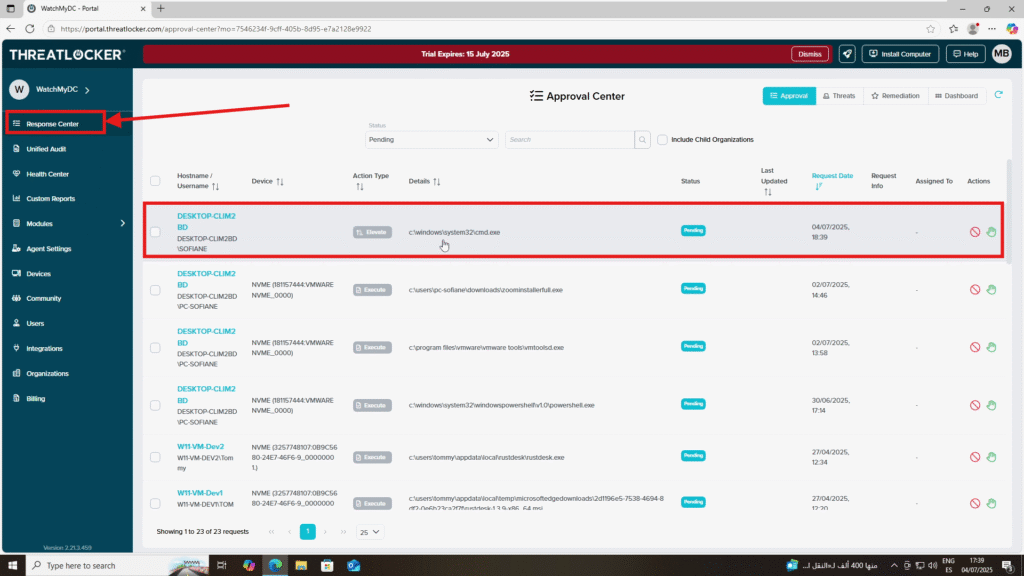
Step 3: Confirm the Request in the ThreatLocker Portal
- Log in to the ThreatLocker Portal
- Navigate to Response Center
- You will see the elevation request listed with all relevant details
Conclusion
ThreatLocker allows users to request elevation securely through the Windows UAC prompt, giving administrators full control over who can run elevated applications and when.
This request-based approach:
- Reduces unnecessary admin rights
- Increases transparency and auditing
- Maintains a strong Zero Trust security model
