
How to restrict elevated access to specific users in ThreatLocker?
This document outlines the step-by-step process of how to restrict elevated access to specific users in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 07 – Elevation Control (Privilege Management).
Introduction
While ThreatLocker’s Elevation Control feature enables applications to run with administrator privileges, it is equally crucial to limit elevation access to trusted users only. Doing so helps prevent unauthorized use of powerful tools such as the Command Prompt (CMD).
This guide outlines the steps to block elevated CMD access for a specific user by configuring a custom elevation control policy.
Implementation
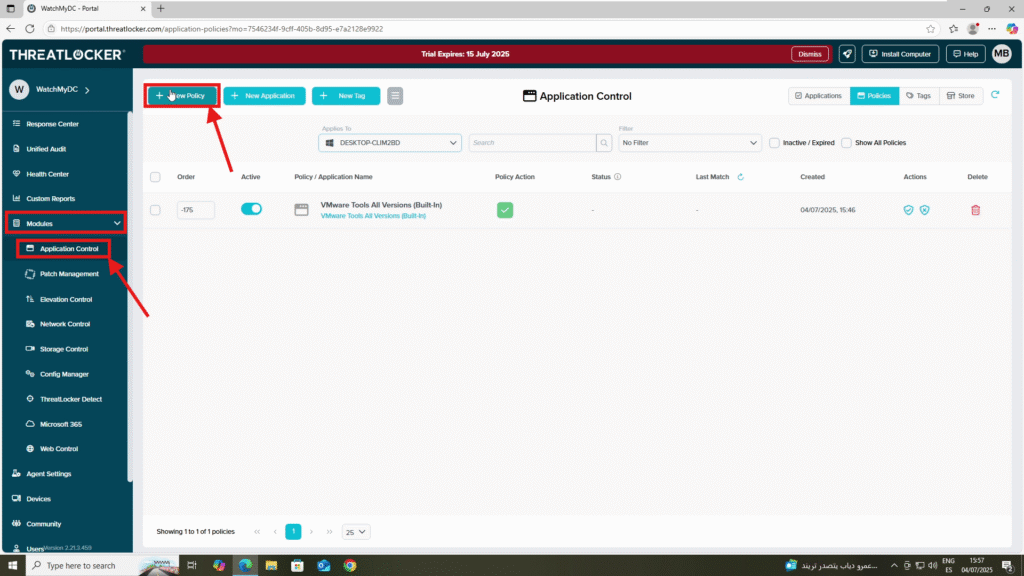
Step 1: Access the Application Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Application Control
- Click Create Policy
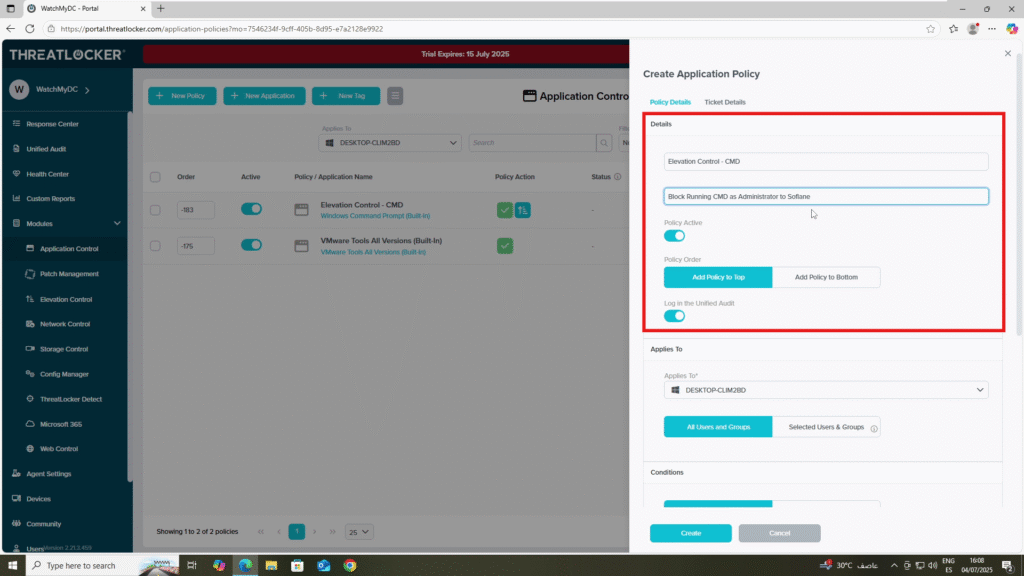
Step 2: Create the Elevation Policy
- Fill the policy form:
- In the Details section:
- Name: Elevation Control – CMD
- Description: Block running CMD as administrator for Sofiane
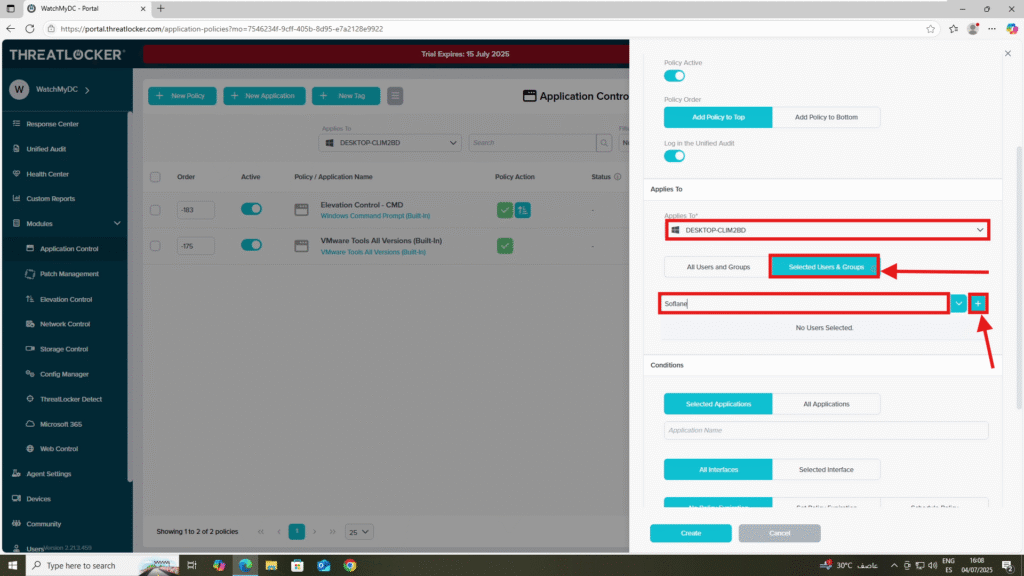
- In the Applied To section:
- Select the target computer or computer group where the policy should apply
- Choose Selected Users and Groups
- Add the specific user (e.g., sofiane)
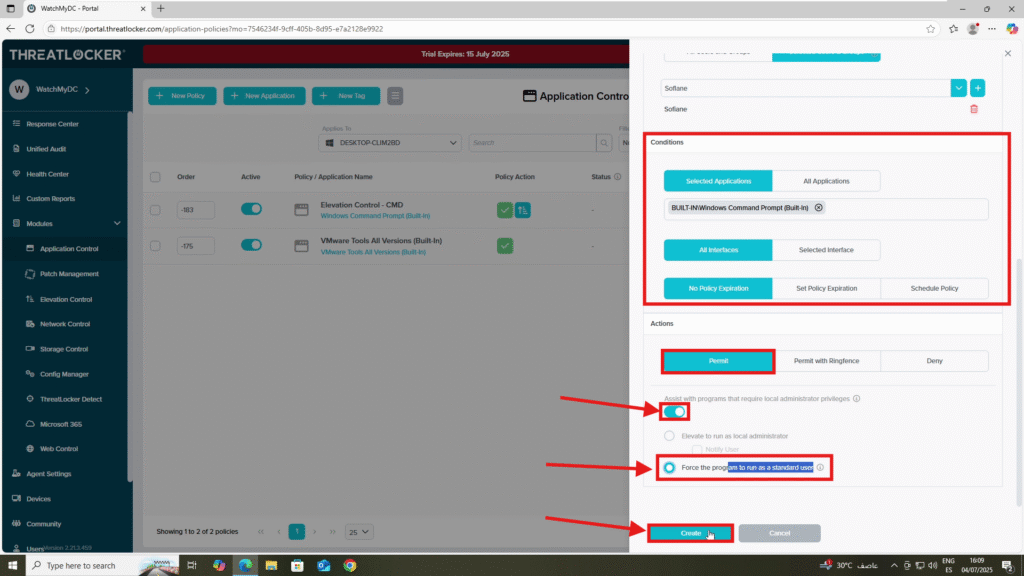
- In the Condition section:
- Select the application: Command Prompt (CMD)
- Choose All Interfaces
- Select “No Policy Expiration” to ensure the rule remains active indefinitely.
- In the Action section:
- Enable “Assist with programs that require local administrator privileges”
- Enable “Force the program to run as a standard user”
- Enable “Assist with programs that require local administrator privileges”
2. Once all fields are completed, click ‘Create’ to save and activate the policy.
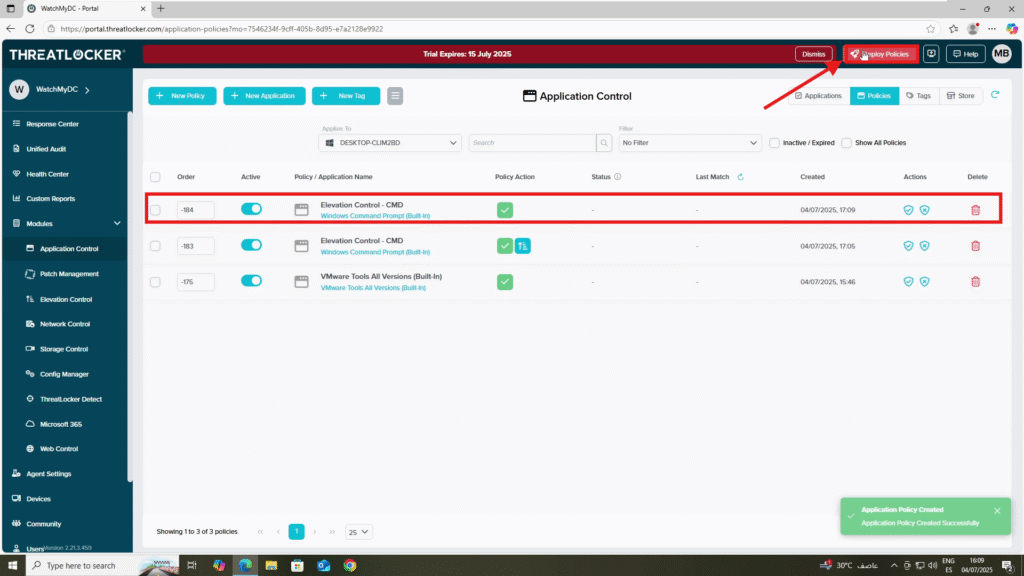
Step 3: Deploy the Policy to restrict elevated access to specific users in ThreatLocker
Deploy the policy from the policy list to enforce it on the target devices
Conclusion
By restricting elevation based on specific users, you reduce the risk of privilege misuse while maintaining flexibility for authorized personnel.ThreatLocker’s fine-grained controls allow you to enforce Zero Trust principles by ensuring only the right people have the right access at the right time.
