
How to Review Events During Learning Mode?
This document outlines the step-by-step process of how to review events during learning mode in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 04 – Learning and Training Mode.
Introduction
ThreatLocker’s Learning Mode (or Training Mode) is designed to observe endpoint activity and log application behavior without enforcing allow/deny policies. During this period, all executions and interactions are recorded in the Unified Audit log. Reviewing these events is essential to building accurate, least-privilege security policies based on real-world usage.
This guide explains how to review those logged events during Learning Mode to determine which applications should be permitted or denied.
Implementation
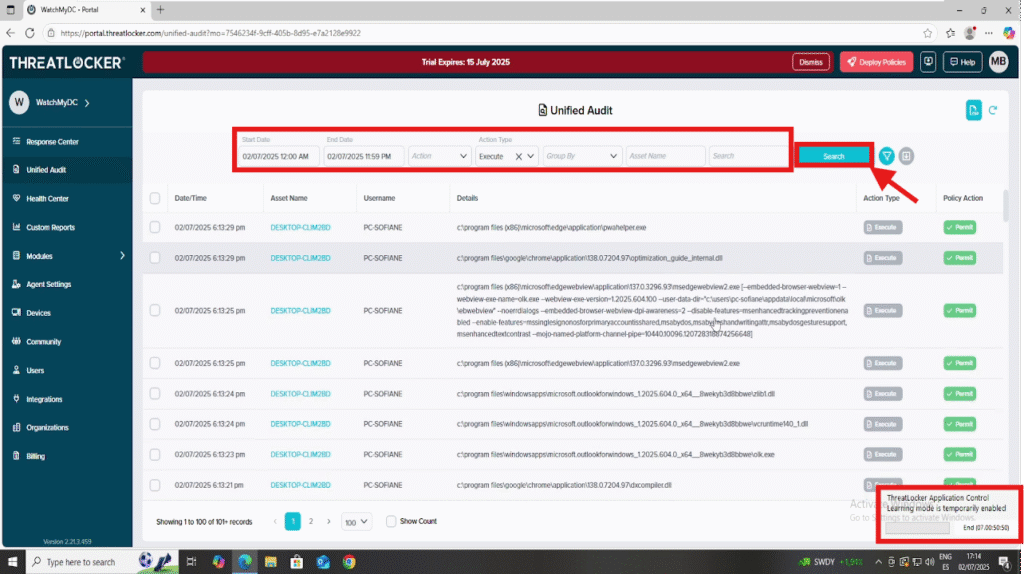
Access the Unified Audit Log
- 1. Log in to the ThreatLocker Portal
- 2. Navigate to Unified Audit from the left-hand menu
- 3. Use filters to narrow down the logs:
- Action Type: Select “Execute” to focus on application activity.
- Time Range: Set the date range to match the Learning Mode period.
- Search by Asset: Use the device name to isolate logs for a specific endpoint
Once all filters are set, click Search to display the relevant audit events.
Conclusion
Reviewing events during Learning Mode is a crucial step in building effective application control policies in ThreatLocker.
By analyzing real-time application activity through the Unified Audit, administrators can identify trusted software, monitor usage patterns, and avoid unnecessary disruptions once enforcement begins.
This review process ensures that policies are tailored to actual user behavior, laying the groundwork for a secure and operationally efficient Zero Trust environment.
