
How to create storage policies for specific users?
This document outlines the step-by-step process of how to create storage policies for specific users in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 05 – Storage Control.
Introduction
Sometimes, it’s necessary to apply storage control rules to a specific user rather than an entire machine or group. For example, blocking USB access for a particular employee or contractor.ThreatLocker’s Storage Control module allows administrators to target individual users or user groups, ensuring personalized control and compliance in shared device environments.
Implementation
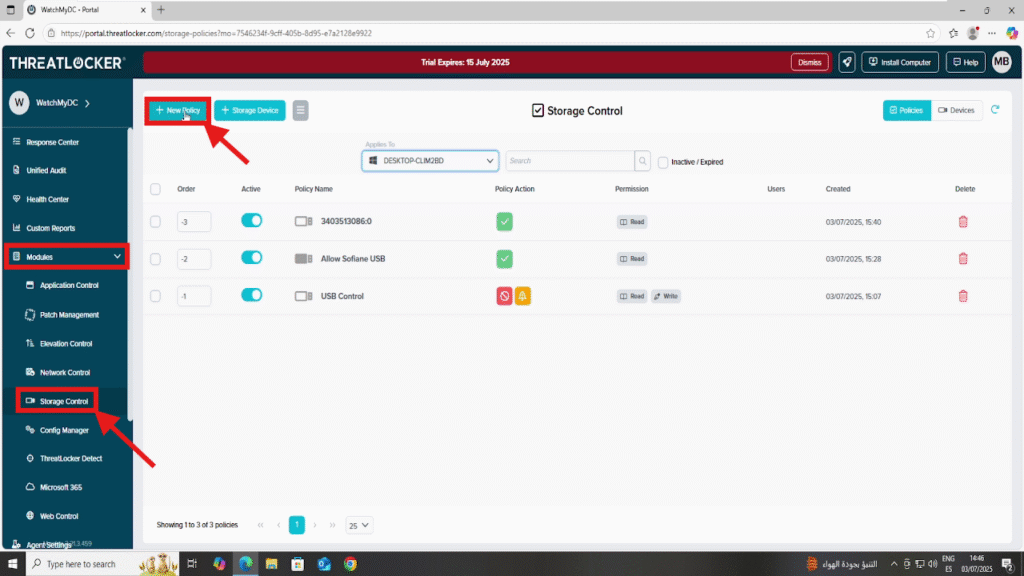
Step 1: Access the Storage Control Module
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Storage Control.
- Click ‘Create Policy’
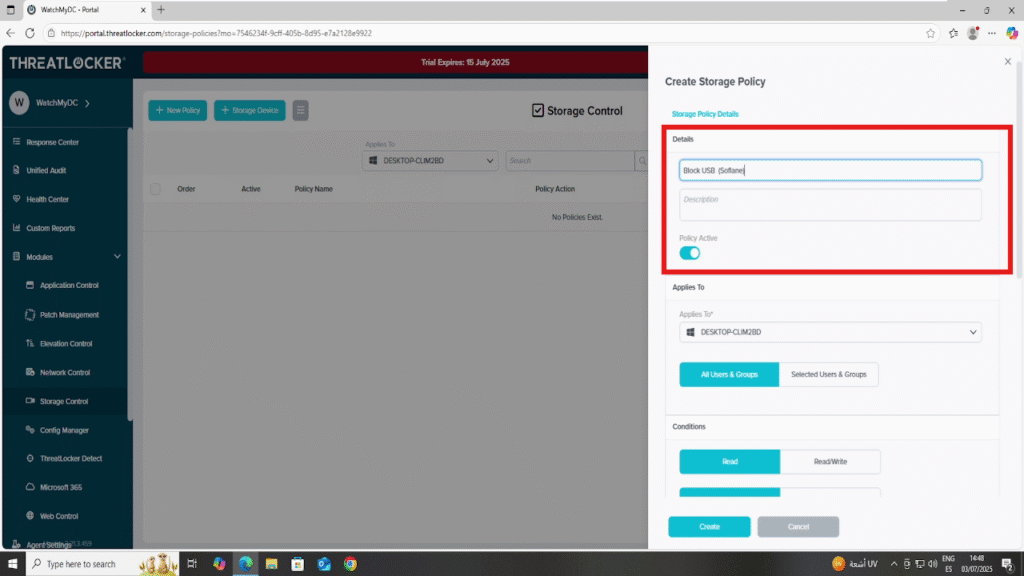
Step 2: Fill in the Policy Creation Form
- In the Details section:
- Name: Block USB – Sofiane
- Description: Block USB for user Sofiane
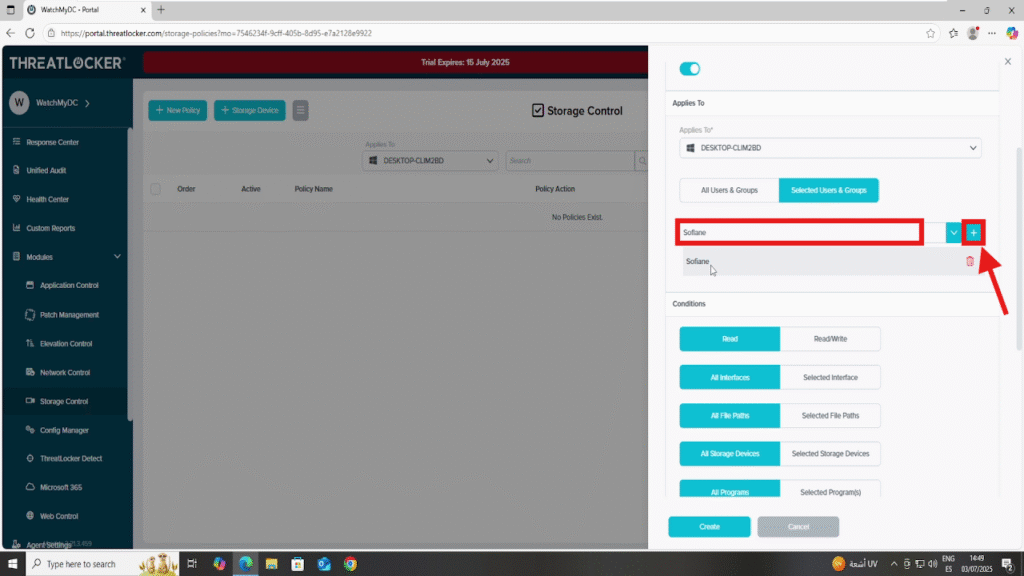
2. In the Applied To section:
- Applied To: Select the target computer or computer group where the policy should be enforced
- Then, under Users and Groups, choose Selected Users/Groups
- Add the specific user (e.g., Sofiane) so the rule is applied only when they are logged in.
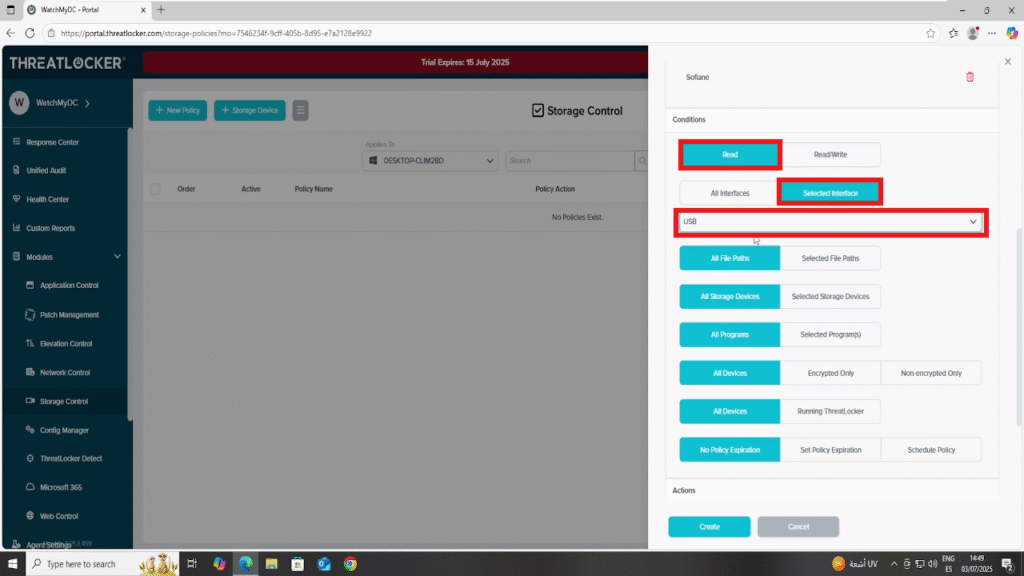
3. In the Condition section:
- Access Type: Read (or Read/Write if you also want to block writing)
- Interface Type: Select Selected Interfaces
- Choose USB to apply the policy only to USB storage devices
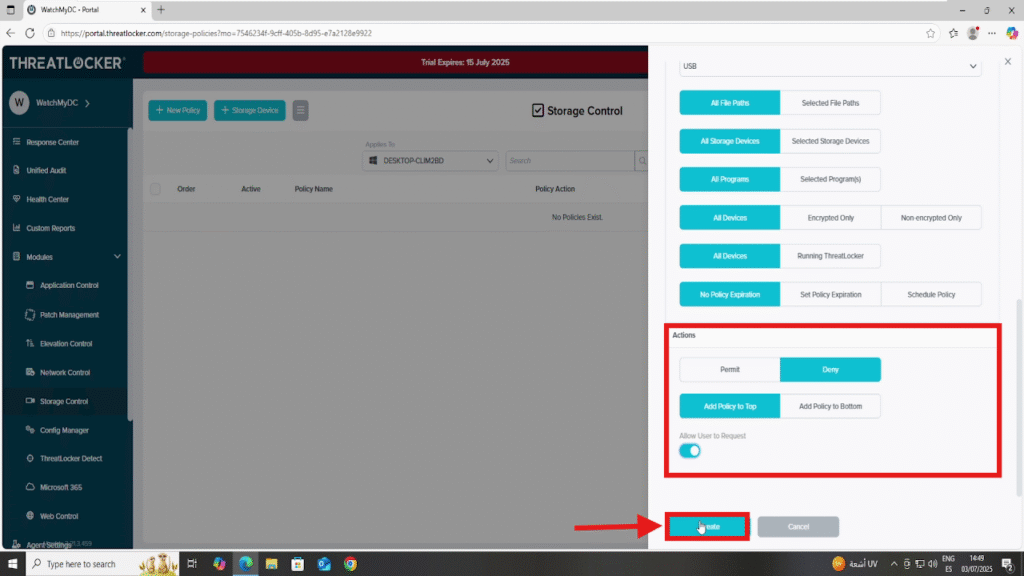
4. In the Action section:
- Select “Deny” as the action
- Enable the ‘Allow User to Request’ option to let users submit a request for temporary access when needed.
- Add the policy to the top of the policy list to ensure it takes priority
Step 3: Deploy the policy
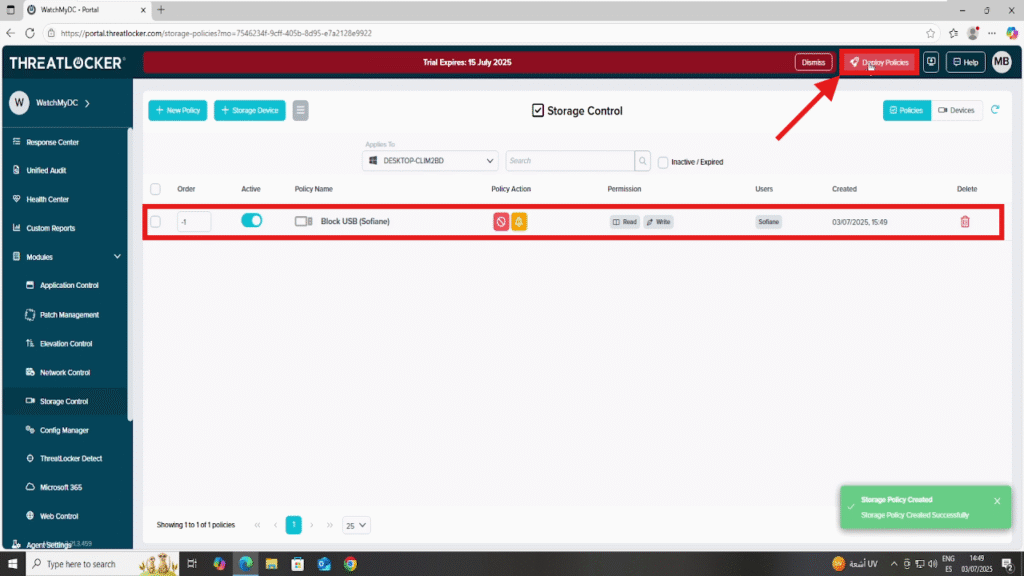
Once all fields are configured, click Create to save the policy
Conclusion
By applying storage control policies to specific users, you gain precise control over who can access USB and external storage — even on shared devices.
This approach allows you to:
- Enforce stricter rules for sensitive user roles
- Maintain flexibility with exception handling
- Strengthen Zero Trust by tying policy enforcement to user identity, not just the machine.
With ThreatLocker, storage access becomes fully customizable, user-aware, and auditable.
