
How to use ringfencing for applications?
This document outlines the step-by-step process of how to use ringfencing for applications in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
Ringfencing is a powerful feature in ThreatLocker that allows administrators to control how approved applications interact with the operating system, files, the internet, and other applications.
This enhances security by limiting the scope of what an allowed application can do, even if it is trusted or whitelisted. For example, you can:
- Restrict applications from reading files in sensitive folders
- Block PowerShell from accessing the internet
- Prevent Office apps from launching other executables
Implementation
Step 1: Access Application Control
Log in to the ThreatLocker Portal. Navigate to Modules > Application Control > Policies. Click on “Create Policy” to begin.
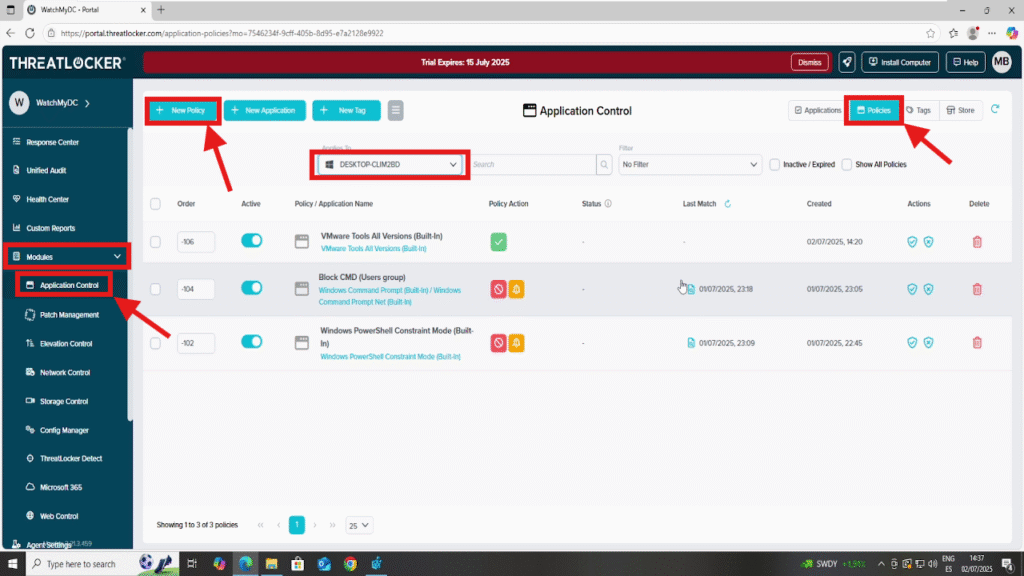
Step 2: Create a Policy with Ringfencing
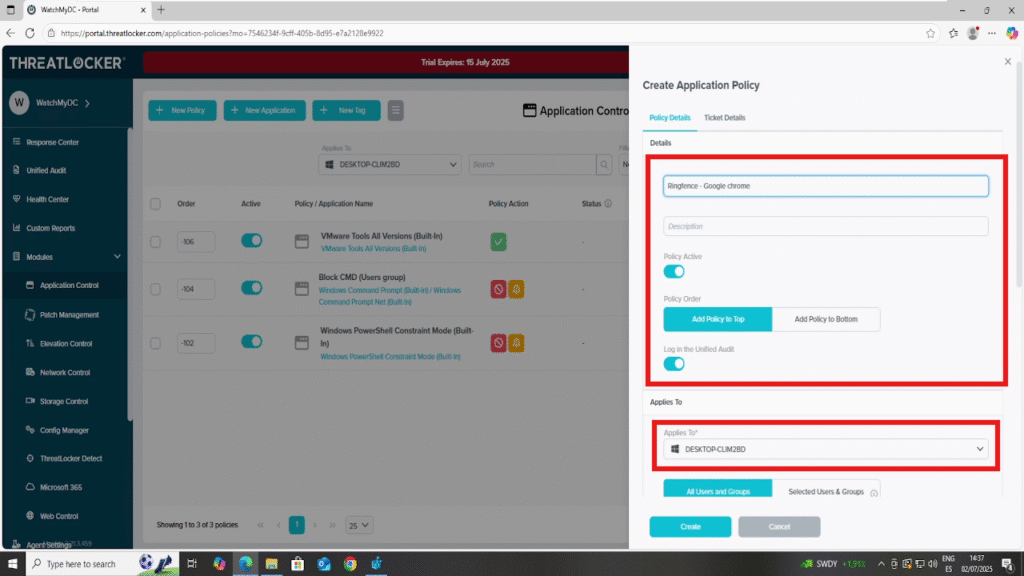
Fill in the creation form. For this example:
- Name: Ringfencing – Google Chrome
- Description: Restrict Chrome from internet and file access
- Apply To: Choose the computer group(s) where this policy should apply
In the Condition section, select the application name (e.g., chrome.exe).In the Action section, Choose “Permit with Ringfencing”
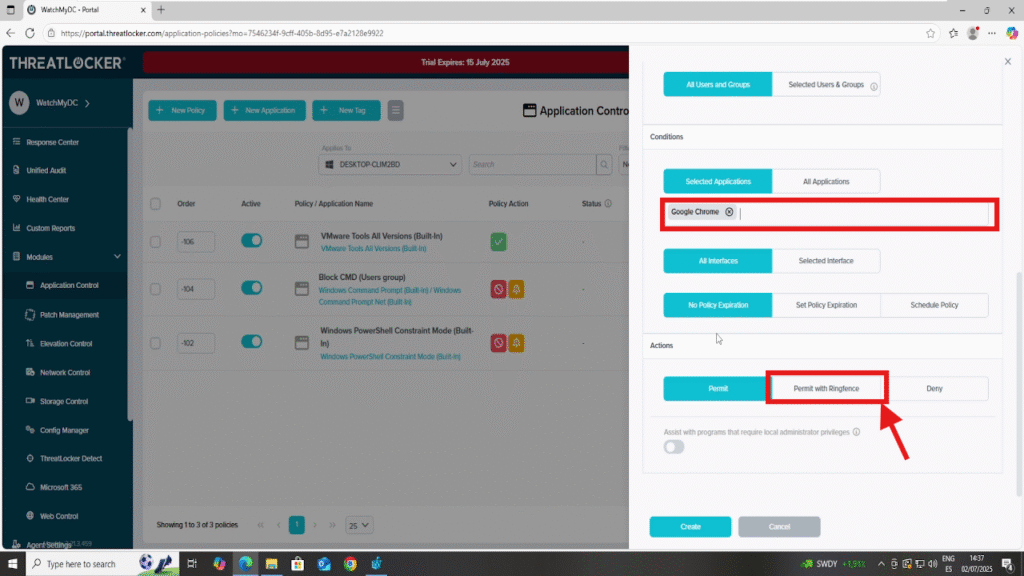
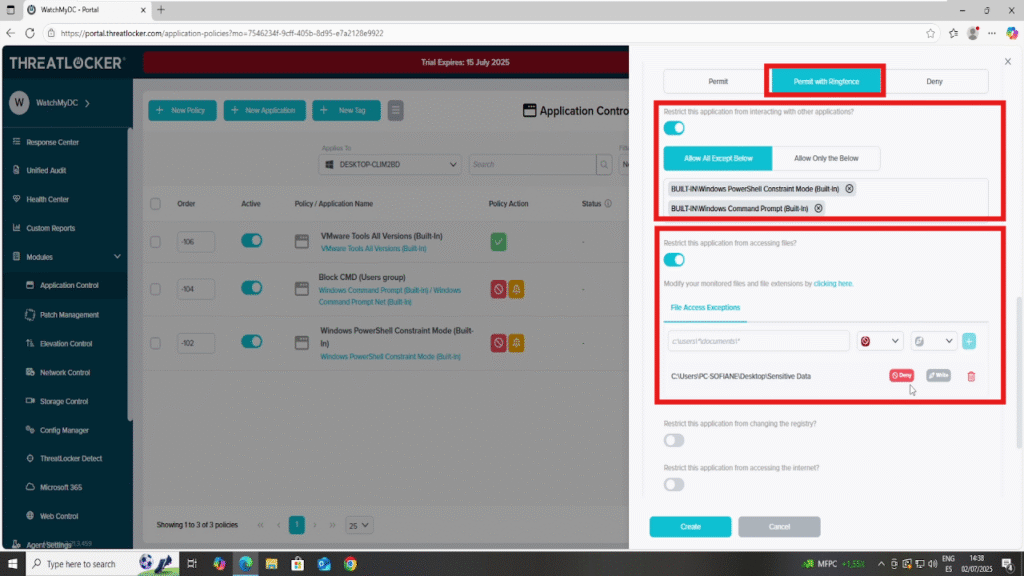
After clicking “Permit with Ringfencing”, four Ringfencing options will appear:
- 1. Restrict this application from interacting with other applications
- Prevents the selected app from launching or injecting into other processes.
- You can add specific applications to restrict interaction with (e.g., block Chrome from launching PowerShell).
- 2. Restrict the application from accessing files
- Controls which file paths the application can access.
- You can define specific directories or file paths to allow or deny (e.g., block access to C:\SensitiveData\).
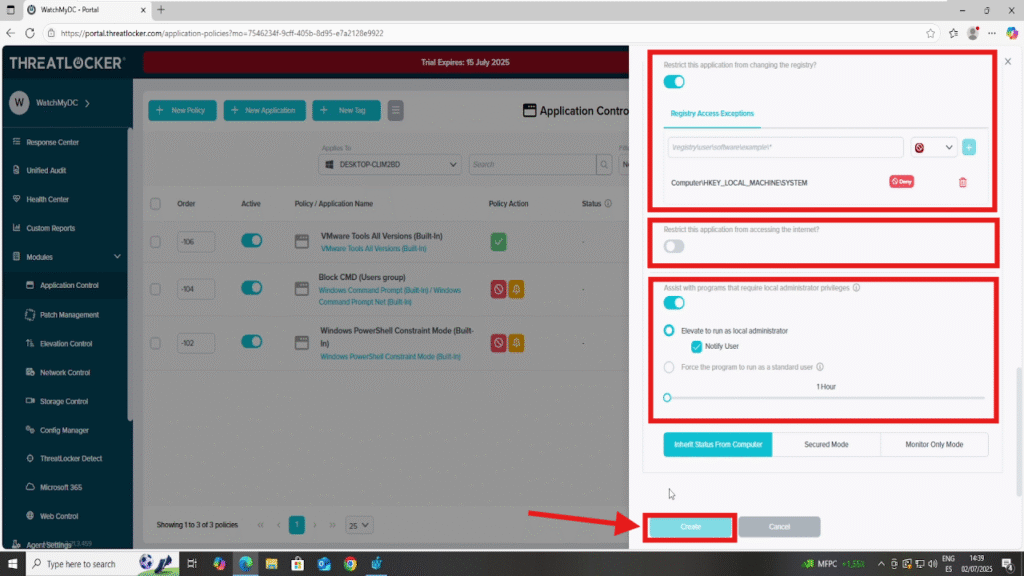
- 3. Restrict the application from modifying registry settings
- Prevents unauthorized changes to the Windows Registry.
- You can choose to block all registry access, or specify certain registry keys to deny (e.g., HKEY_LOCAL_MACHINE\SOFTWARE\Policies).
- 4. Restrict the application from accessing the internet
- Controls network traffic from the application.
- You can block all internet access, or allow/deny specific domains or IP addresses (e.g., block everything except *.mycompany.com).
Once all Ringfencing options are configured, click Create to save the policy.
Step 3: Save the Policy
Once all Ringfencing options are configured, click Create to save the policy.
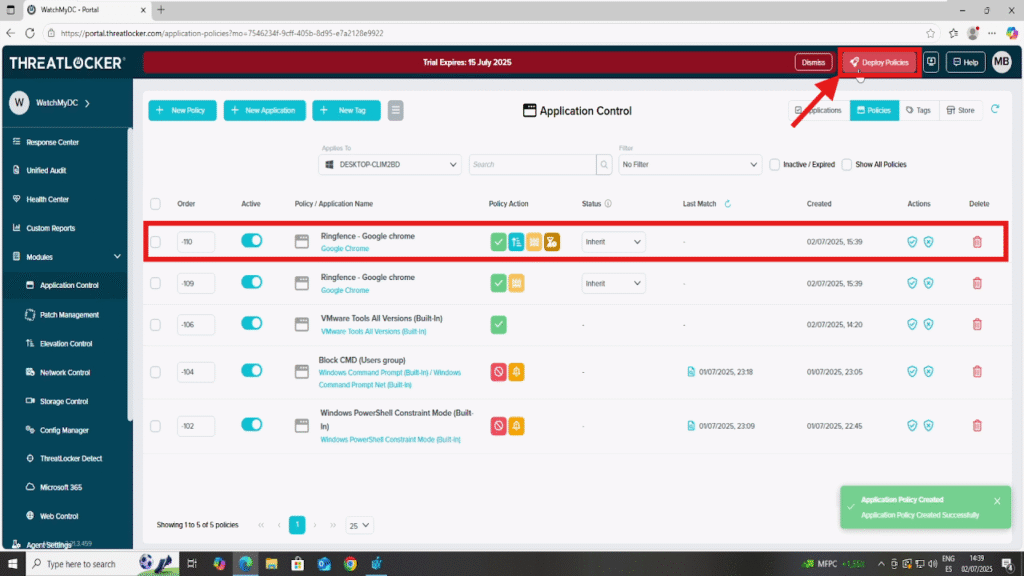
Step 4: Deploy the Policy
Then, click the Deploy button to apply the policy across the selected endpoints.
Conclusion
Using Ringfencing in ThreatLocker significantly enhances your organization’s security posture by limiting what trusted applications can do, even after they’re allowed to run.
By controlling access to files, registry, internet, and interactions with other apps, you:
- Prevent malicious abuse of legitimate software
- Minimize the impact of zero-day vulnerabilities
- Reduce the attack surface without blocking essential tools
When properly configured and deployed, Ringfencing supports a strong Zero Trust strategy while preserving operational functionality.
