
How to use ThreatLocker API?
This document outlines the step-by-step process of how to use ThreatLocker API.
This article is a part of our ThreatLocker How-to Guides series, Chapter 12 – Integration & Third-party Tools.
Introduction
The ThreatLocker API allows you to programmatically interact with your ThreatLocker environment. This can be used for automation, integration with other systems, or custom reporting.
Implementation
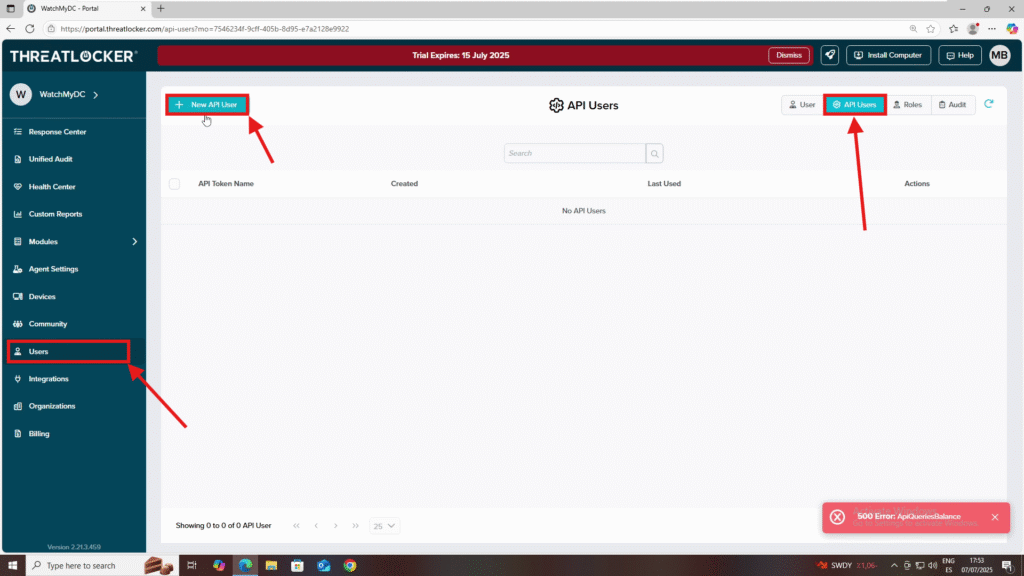
Step 1: Create an API User to use ThreatLocker API
- Log in to the ThreatLocker Portal.
- Navigate to Users > API Users
- Click New API User.
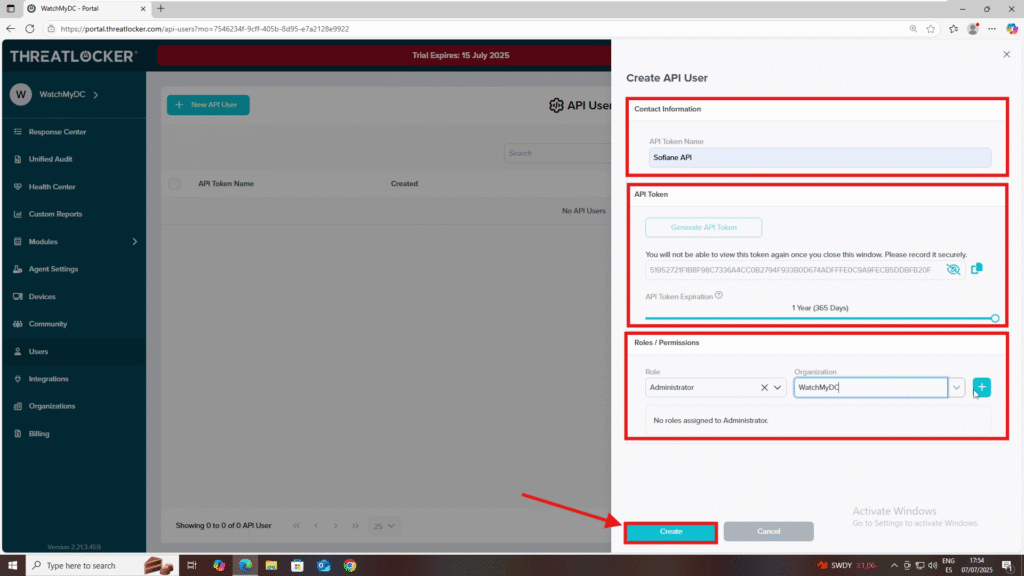
3. Complete the form:
- Contact Information
- API Token Name: Enter a descriptive name (e.g., Integration_Script_Token).
- API Token
- The token will be generated here, copy it and store it securely for later use.
- You can select the Token Expiration (e.g., 1 year, 6 months).
- Role and Permissions
- Select the role.
- Select the organization.
- Click Add to assign it.
- Click Create to confirm.
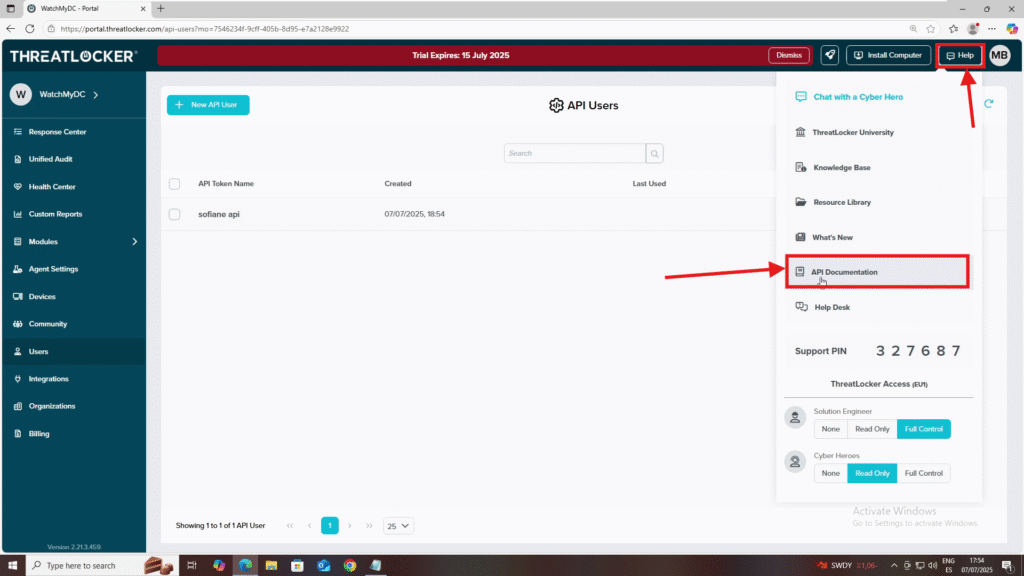
Step 2: Access API Documentation in ThreatLocker
- In the ThreatLocker dashboard, click Help.
- Select API Documentation.
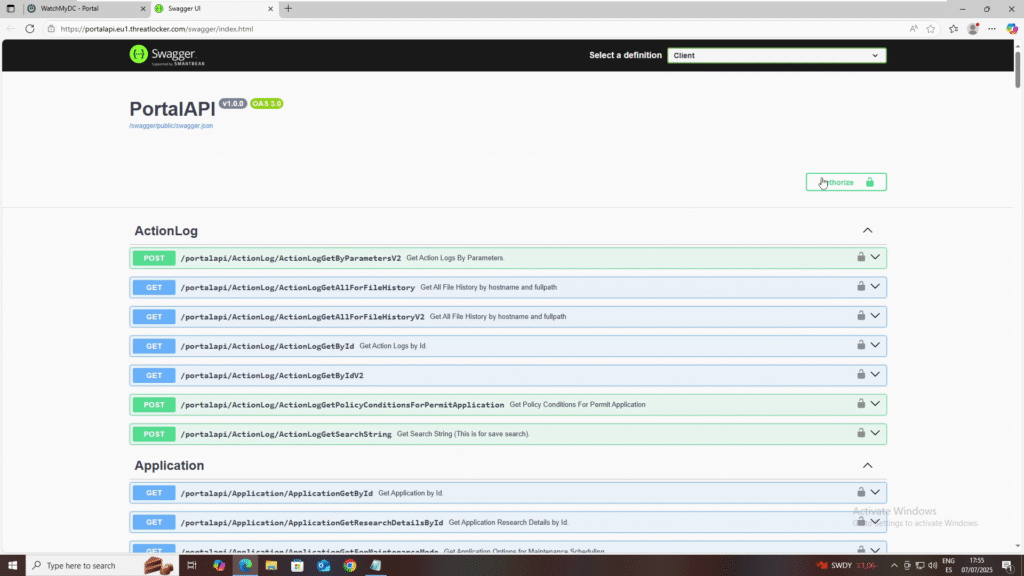
3. The documentation page will list all available fields for using the API, like Actions, Logs, Applications, Computers, etc., along with their supported methods (GET or POST).
Conclusion
Once the API user is created and you have your token, you can use the ThreatLocker API to automate tasks and integrate ThreatLocker data into other systems. Always store your API token securely and follow the documentation for correct usage.
