
How to use the ThreatLocker dashboard?
This document outlines the step-by-step process of how to use the ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 10 – Monitoring, Logs and Reports.
Introduction
The ThreatLocker Dashboard (Health Center) provides a central overview of your organization’s security posture. It displays the status of various policies, updates, and audit summaries, helping administrators quickly identify issues and take action.
Implementation
Step 1: Access the ThreatLocker Dashboard
- Login to the ThreatLocker Portal.
- From the left-hand menu, navigate to Health Center.
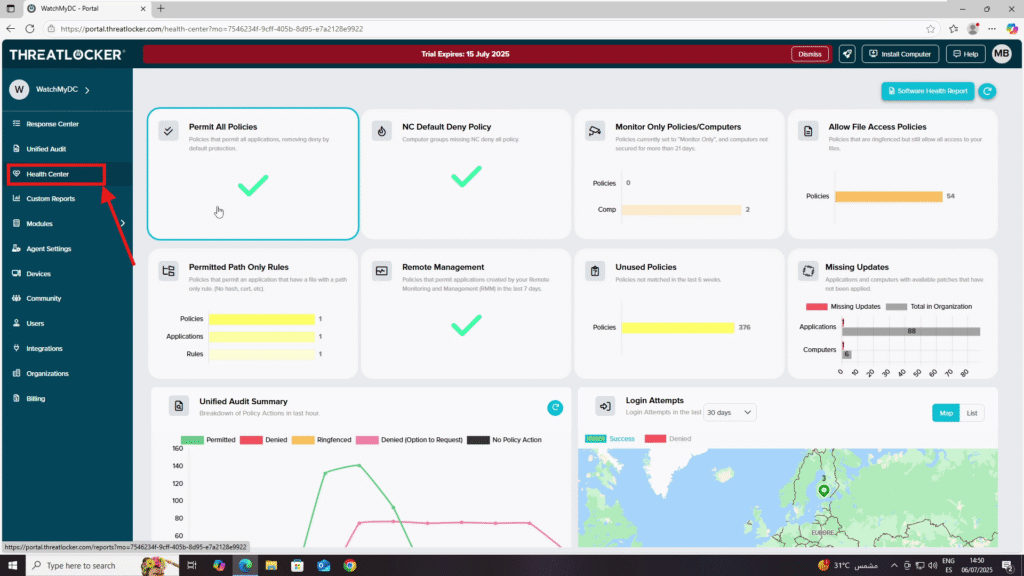
Step 2: Dashboard Overview
The dashboard is divided into multiple sections, each representing the status and key metrics from different ThreatLocker modules.
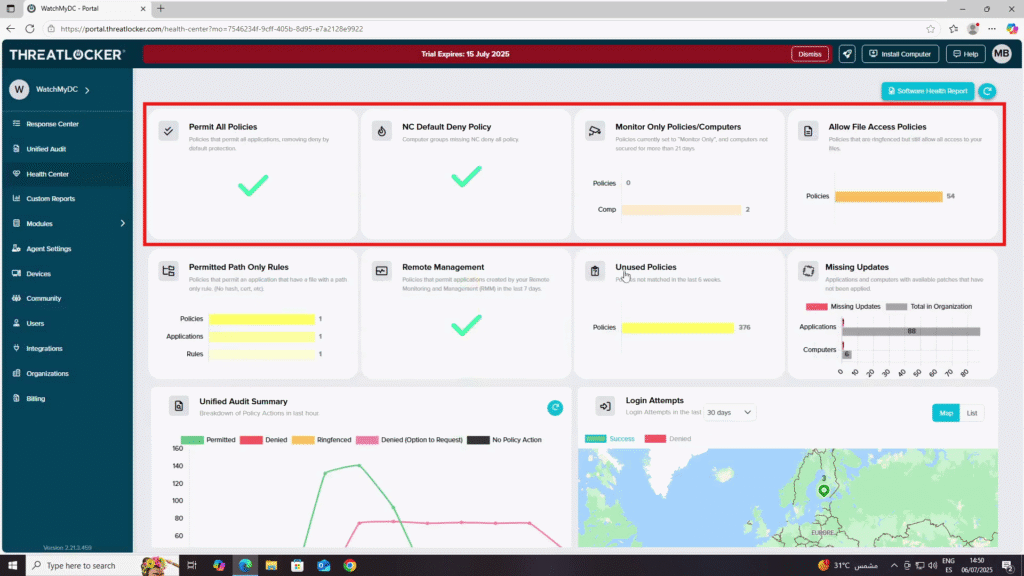
- Top Section : Policy Status
- Permit All Policies – Shows whether all applications are being permitted (should generally be avoided for security).
- NC Default Deny Policy – Indicates if any computer groups are missing the default deny policy.
- Monitor Only Policies/Computers – Displays the number of computers in Monitor Only mode for more than 21 days.
- Allow File Access Policies – Shows the number of ringfenced policies still allowing file access.
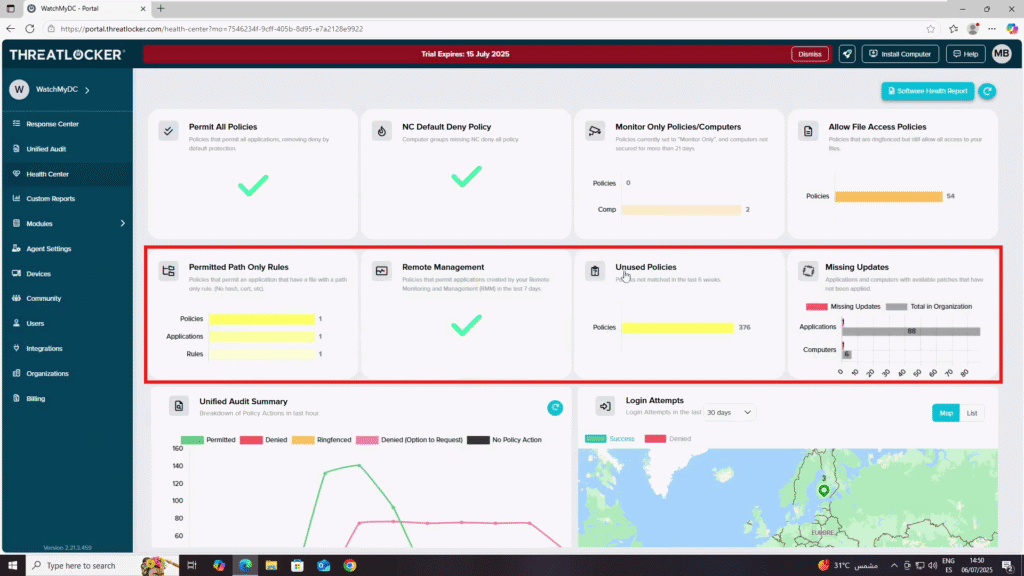
2. Middle Section : Rules & Updates
- Permitted Path Only Rules – Displays counts for policies, applications, and rules with path-only permissions (no hash or certificate).
- Remote Management – Shows the status of policies permitting applications from your RMM tools.
- Unused Policies – Lists policies not matched in the last 6 weeks.
- Missing Updates – Displays applications and computers with available patches not yet applied.
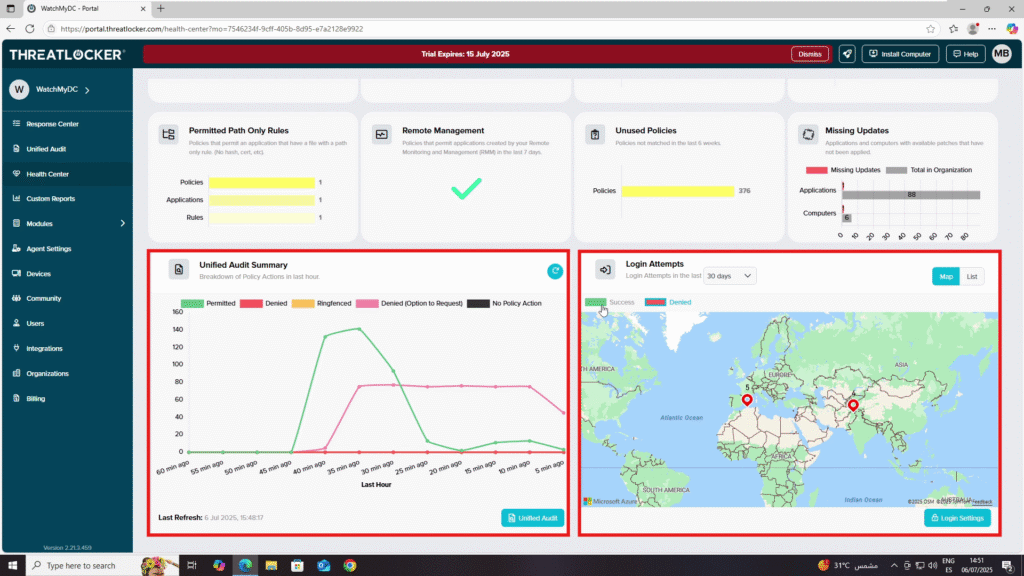
3. Bottom Section – Activity Monitoring
- Unified Audit Summary : A graph showing the breakdown of policy actions in the last hour (Permitted, Denied, Ringfenced, etc.).
- Login Attempts : A world map indicating locations of successful and denied login attempts over the selected time period.
Conclusion
By enabling alert notifications in ThreatLocker, you can stay updated on critical user requests in real-time, helping you respond quickly to operational needs or potential security concerns.
