
How to use ThreatLocker Suggested Policies?
This document outlines the step-by-step process of how to use ThreatLocker suggested policies.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
ThreatLocker automatically generates Suggested Policies based on observed behavior during learning mode.
These policies help administrators quickly approve commonly used applications without manually building rules from scratch.
Using suggested policies improves efficiency, especially during initial deployment or onboarding of new devices.
Implementation
Step 1: Access the Application Control Module
- Log in to the ThreatLocker Portal.
- Navigate to: Modules > Application Control > Policies > Policy Management > ThreatLocker Suggested Policies
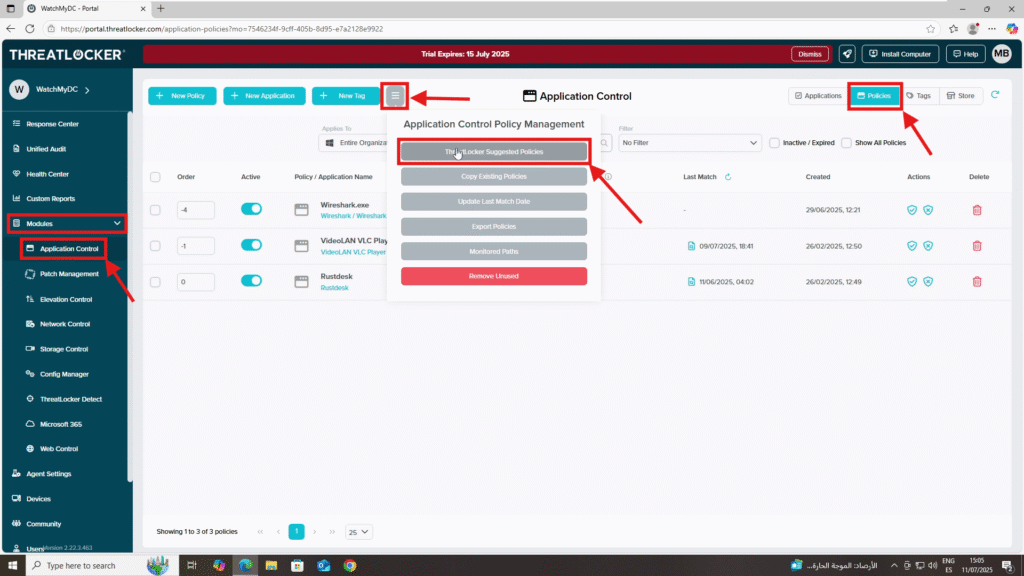
Step 2: Suggested Policies Window
In the ThreatLocker Suggested Policies window, you’ll see a list of predefined policy recommendations. You can use the search bar or apply filters to narrow down the list, such as:
- Microsoft Recommended
- New Group Templates
- Ninite Bundles
- Recommended Policies for Meeting Applications
- Reference Templates
Click on any template to view the individual suggested policies it contains.
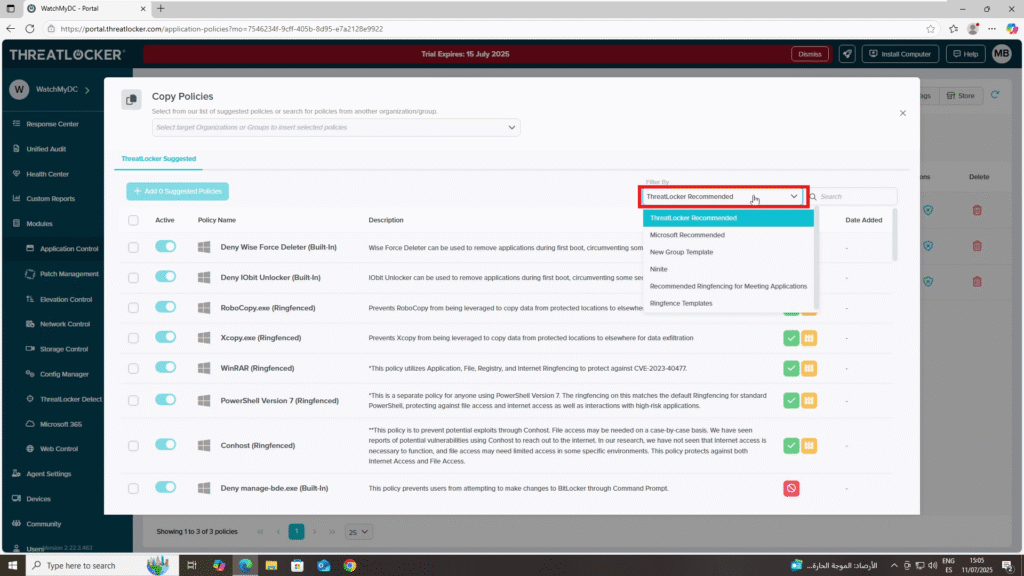
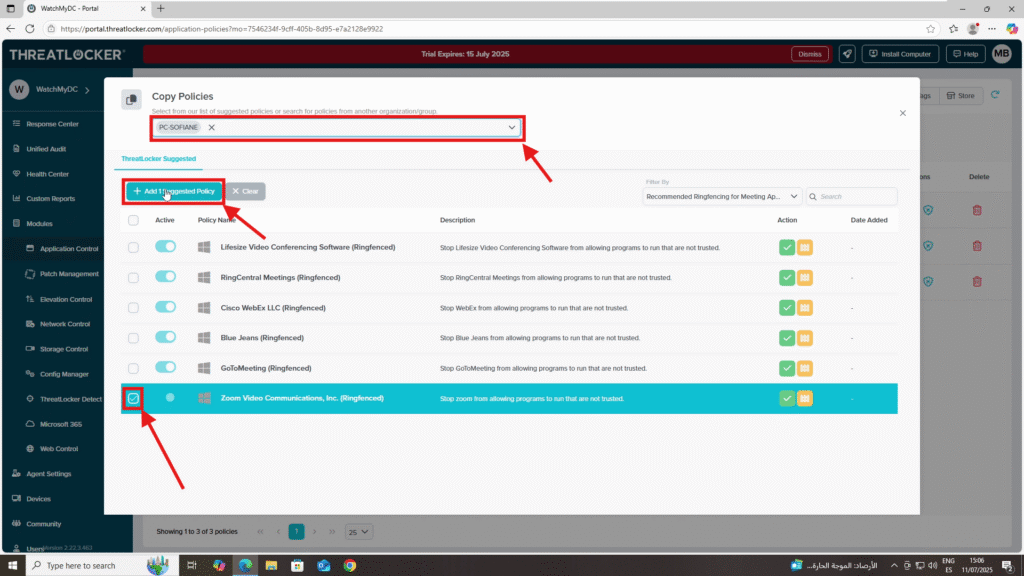
Step 3: Apply a Suggested Policy
Once you’ve located the desired policy:
- Select the policy from the list
- In the upper-left corner, locate the Copy Policies section
- Select the target computer or device group where you want to apply the policy
Click “Add Suggested Policy” to apply it.
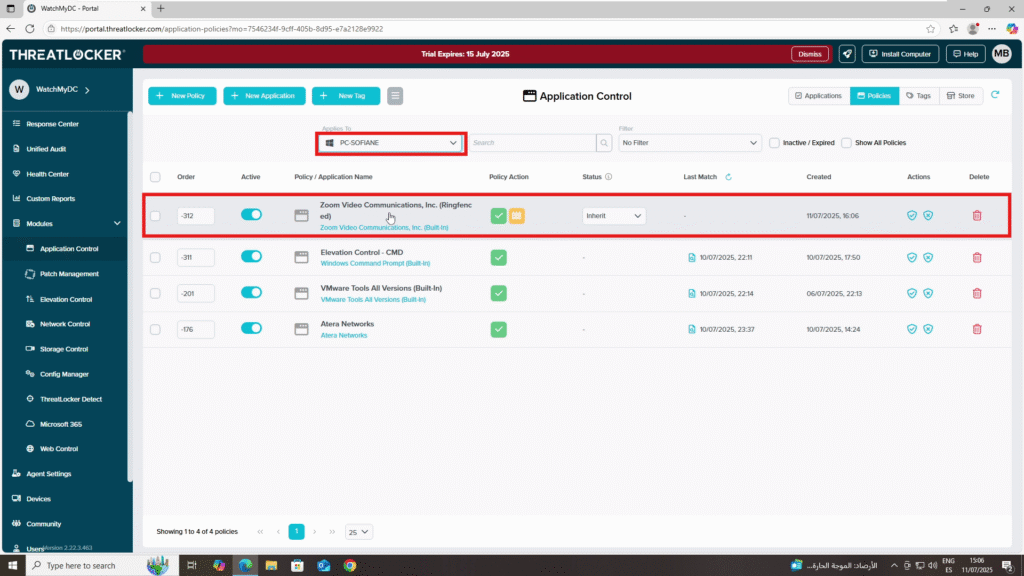
Step 3: Deploy a Suggested Policy
The policy will be added and automatically deployed to the selected target devices.
Conclusion
Using Suggested Policies in ThreatLocker provides an efficient way to deploy security rules based on real-world application behavior.
This approach:
- Accelerates the implementation of a Zero Trust model
- Ensures consistent policy enforcement across endpoints
- Minimizes manual configuration errors
For optimal security, it’s recommended to review each suggested policy before approval to ensure it aligns with your organization’s strategic security objectives.
