
How to view blocked application attempts in ThreatLocker?
This document outlines the step-by-step process of how to view blocked applications attempts in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 10 – Monitoring, Logs and Reports.
Introduction
In ThreatLocker, the Unified Audit feature allows administrators to review all blocked application attempts. This is useful for monitoring potential threats, verifying policy effectiveness, and identifying applications that users may need for legitimate purposes.
Implementation
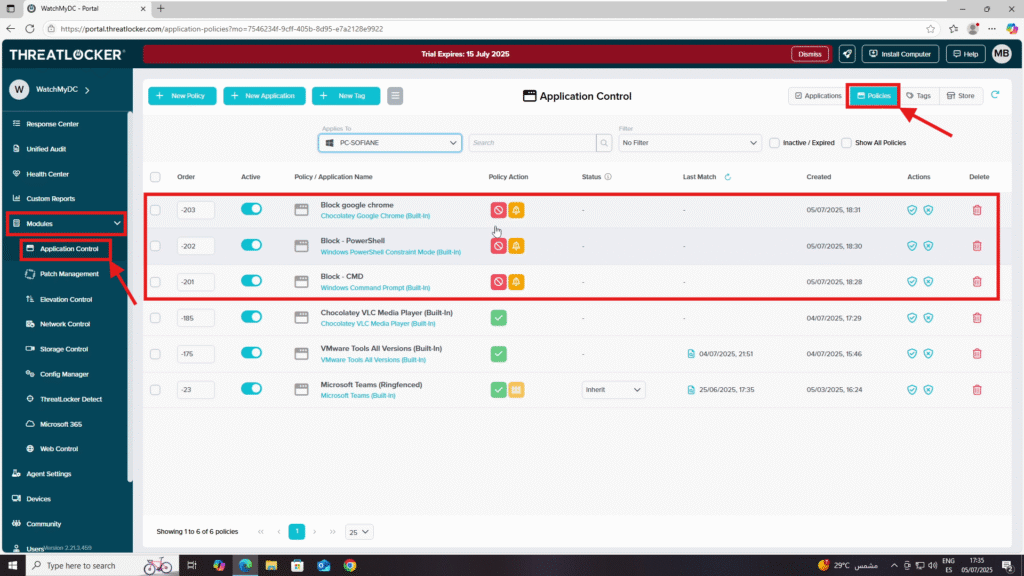
Step 1: Confirm That a Blocking Policy Exists
Before searching for blocked attempts, ensure that a policy is in place to block the application.
- Log in to the ThreatLocker Portal.
- Navigate to Modules > Application Control > Policies.
- Locate the policy that blocks the target application.
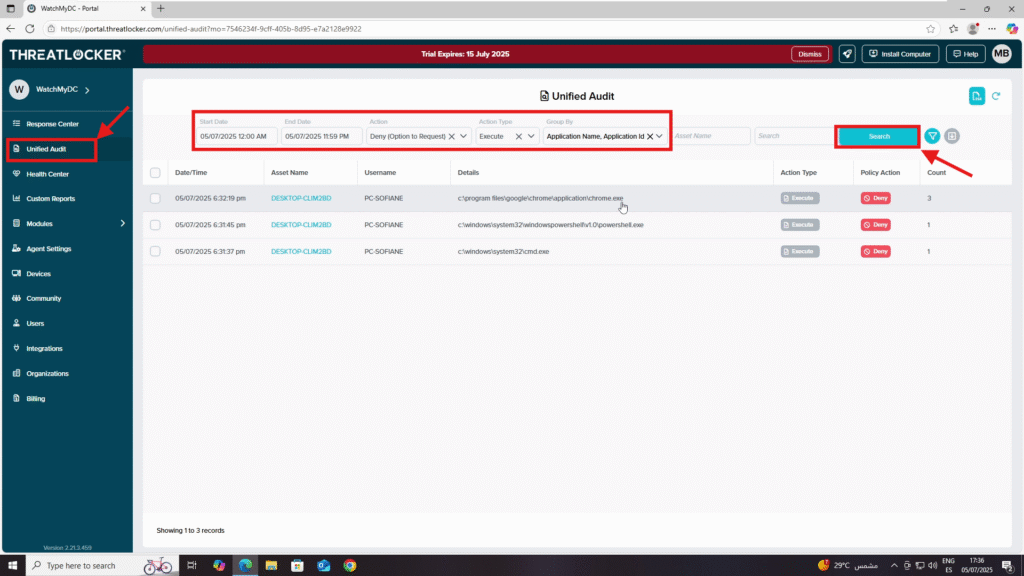
Step 2: Audit the Blocked Execution Attempt
Once you have tried to run the blocked application, you can view the attempt in the Unified Audit.
- Navigate to Unified Audit from the left-hand menu.
- Use the filter section to narrow results:
- Start Date / End Date: Select the time period to search.
- Action: Choose Deny or Deny (Option to Request) depending on your need.
- Action Type: Set to Execute.
- Group By: Select Application Name and Application ID for a clearer view.
- Click Search to display results.
- The audit results will show:
- Date / Time of the attempt
- Asset Name (device)
- Username of the user who attempted execution
- Details (path, hash, etc.)
- Count (number of attempts)
Conclusion
By reviewing blocked execution attempts in ThreatLocker’s Unified Audit, you can quickly identify when and by whom an application was blocked. This helps in both security monitoring and policy adjustment to ensure a balance between protection and productivity.
