
How to whitelist an executable file?
This document outlines the step-by-step process of how to whitelist and executable file in ThreatLocker Dashboard.
This article is a part of our ThreatLocker How-to Guides series, Chapter 03 – Zero Trust Policies (Application Control).
Introduction
The Application Control module in ThreatLocker is designed to block all unknown or unapproved applications by default. To allow (i.e., whitelist) a trusted .exe file, administrators can create an Application Control policy that permits its execution on specific endpoints or for specific users.
Implementation
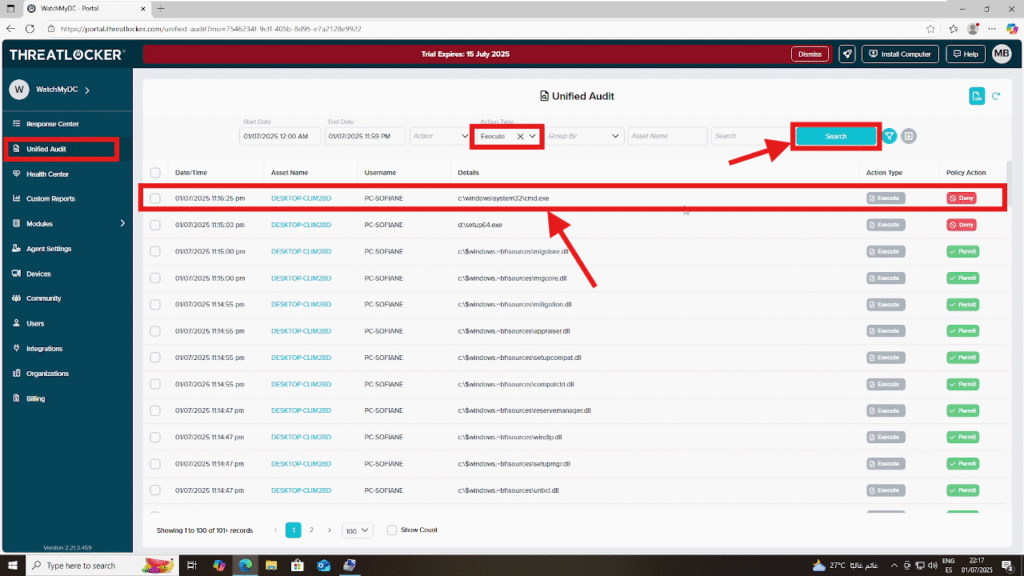
Step 1: Locate the Blocked Executable
Log in to the ThreatLocker Portal and navigate to the Unified Audit section. In the filter options, set the Action Type to Execute, then click Search to display all execution attempts. Locate the blocked application entry (e.g., cmd.exe) that has the action marked as Deny, then click on it to view more details.
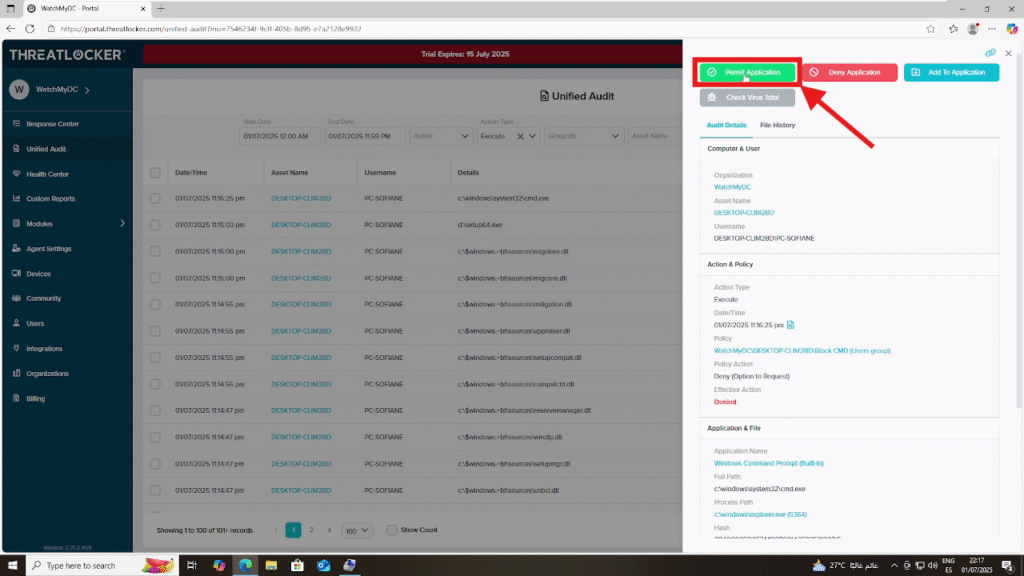
Step 2: Create a New Policy to Whitelist
Once you’ve opened the details of the blocked executable from the audit log, click on the “Permit Application” button. This will begin creating a new policy.
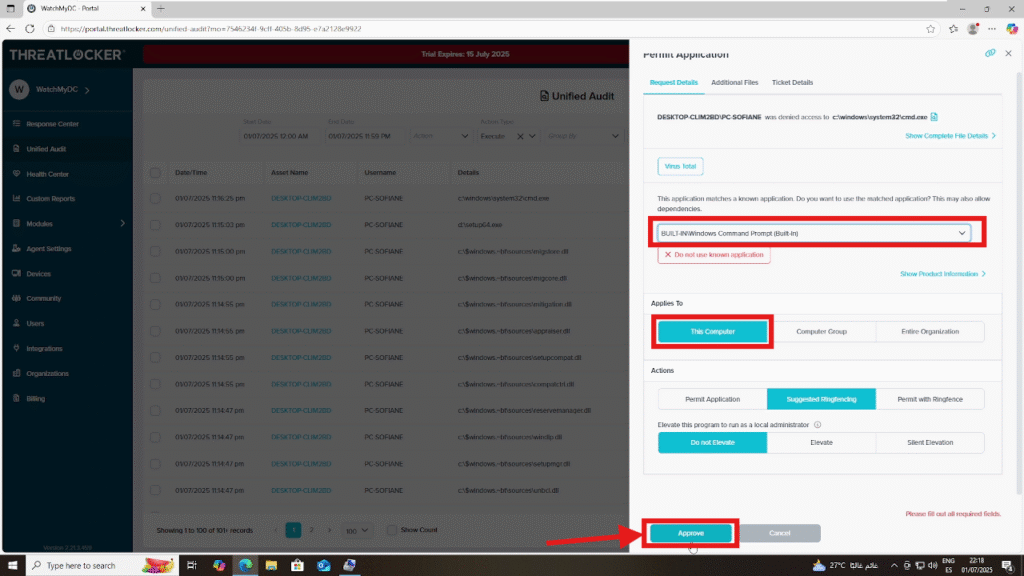
In the policy form, confirm that the correct application is selected. Then, choose the appropriate Computer Group or User Group to which the policy should apply. Next, click Approve to validate and deploy the policy immediately.
Conclusion
Whitelisting a specific executable in ThreatLocker is a quick and effective way to permit trusted applications while maintaining a Zero Trust security model.
By carefully reviewing audit logs and approving only known, safe executables, you ensure that your environment remains both secure and functional.
The policy takes effect immediately upon deployment. However, these can be modified or removed at any time as your security needs evolve.
